This step-by-step tutorial demonstrates how to apply Local Group Policy to administrators in Windows 11 and Windows 10. It also includes information about Windows system administration, Local Group Policy, troubleshooting tips, and best practices for managing multiple Windows devices.
Applying Local Group Policy settings only to administrators allows you to enable or disable features only for administrative users, giving you more control over who can make changes to your PC configuration and perform certain actions.
Local Group Policy in Windows Explained
Group Policy is a Windows feature that is available in Pro, Enterprise, and Server variants of the operating system. It allows for the administration and configuration of Windows devices, including system and user settings, as well as configuring third-party applications. It is the way to manage Windows’ security policies, user permissions, network configuration, and user profiles.
Group Policies are made up of Group Policy Objects (GPOs). Each individual GPO contains a number of configuration options that change how the associated Windows feature or application functions. GPOs are applied as either a Computer Configuration which applies to a specific Windows device and any user who is logged in to it, or User Configuration, which applies to a single user account while they are logged in, regardless of which device they are logged in to.
Some configurations that are commonly implemented using Windows Group Policies and Group Policy Objects include:
- Automatically configuring network shares and shared printers.
- Setting login and logoff scripts.
- Automatically configuring web browser settings like proxies and whether scripts are allowed or not.
- Configuring anti-malware and firewall rules.
- Blocking access to certain applications or Windows features.
Windows Group Policy GPOs can be one of two types:
- Local Group Policy: Local group policies apply only to the specific device they are configured on. Importantly, Local Group Policy Objects are overridden by domain Group Policy Objects from Group Policy in Active Directory.
- Group Policy in Active Directory: Group Policy Objects can be created in a Windows Active Directory domain. These policies are scoped based on the user or device Organizational Unit within Active Directory. Active Directory is usually deployed to manage Windows devices and users in an enterprise environment.
Group Policy to administrators: Required versions
Home editions of Windows do not let you manage Local Group Policy. To use Local Group Policy or Group Policy in Active Directory you will need to be running one of the following versions of Windows:
- Windows 10 Pro, Enterprise, or Education.
- Windows 11 Pro, Enterprise, or Education.
- Windows 7/8 Pro, Enterprise, or Ultimate (note that you should no longer be using these versions of Windows as they are obsolete and no longer receive updates).
You will also need your own administrator user account.
Step-by-step tutorial: applying Local Group Policy to administrators in Windows
To manage Group Policy for administrators, you can create a custom Microsoft Management Console (MMC) window that edits group policies only for users in the Administrators group:
- Right-click on the Start button, then select Run.
- Enter mmc, click OK, and click Yes on the User Account Control Prompt to open the MMC.
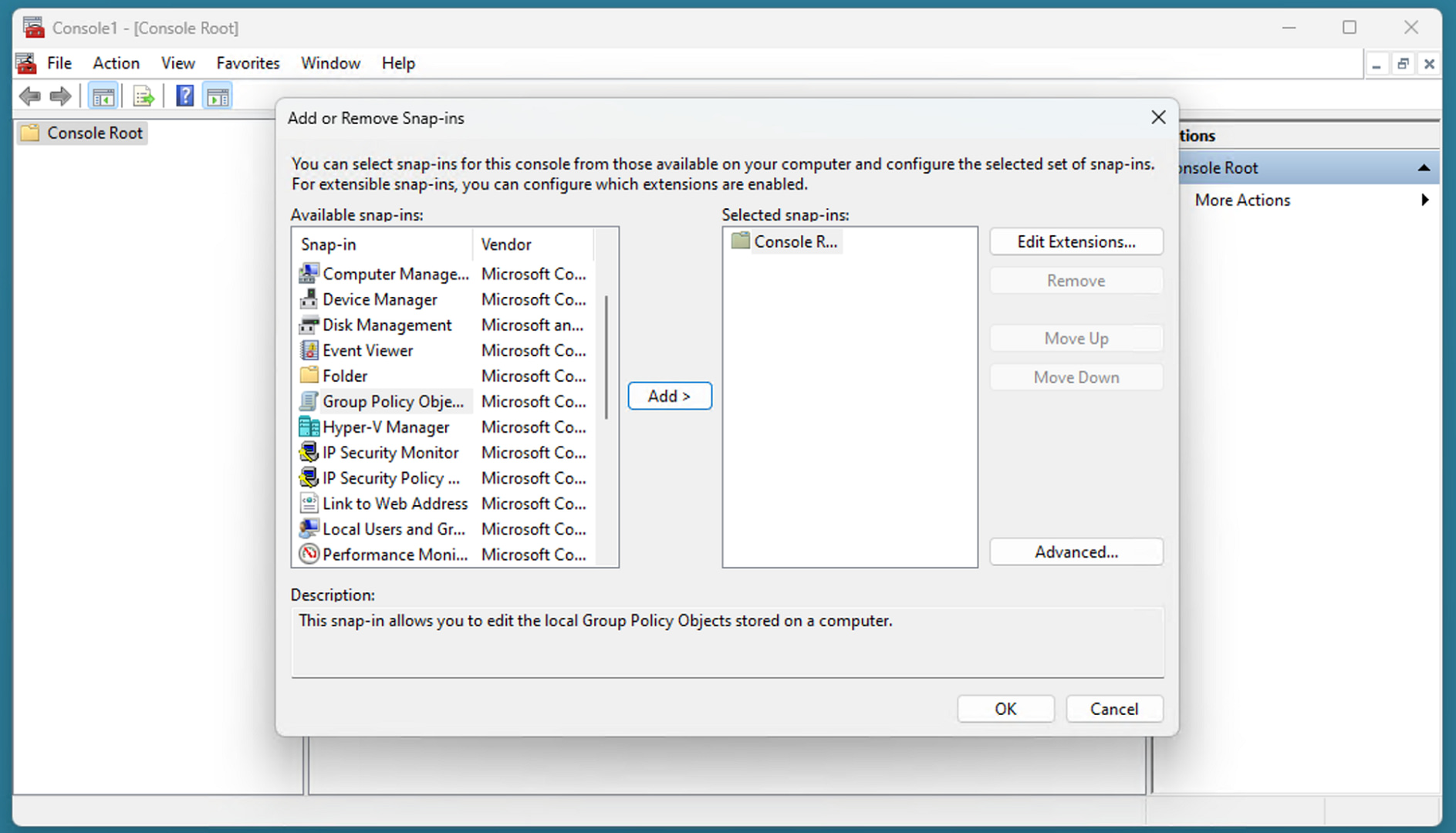
- Click on File in the menu bar, and then select Add/Remove Snap-In…
- Choose Group Policy Object Editor from the list of Available snap-ins.
- Click the Add > button to add it to the list of Selected snap-ins.
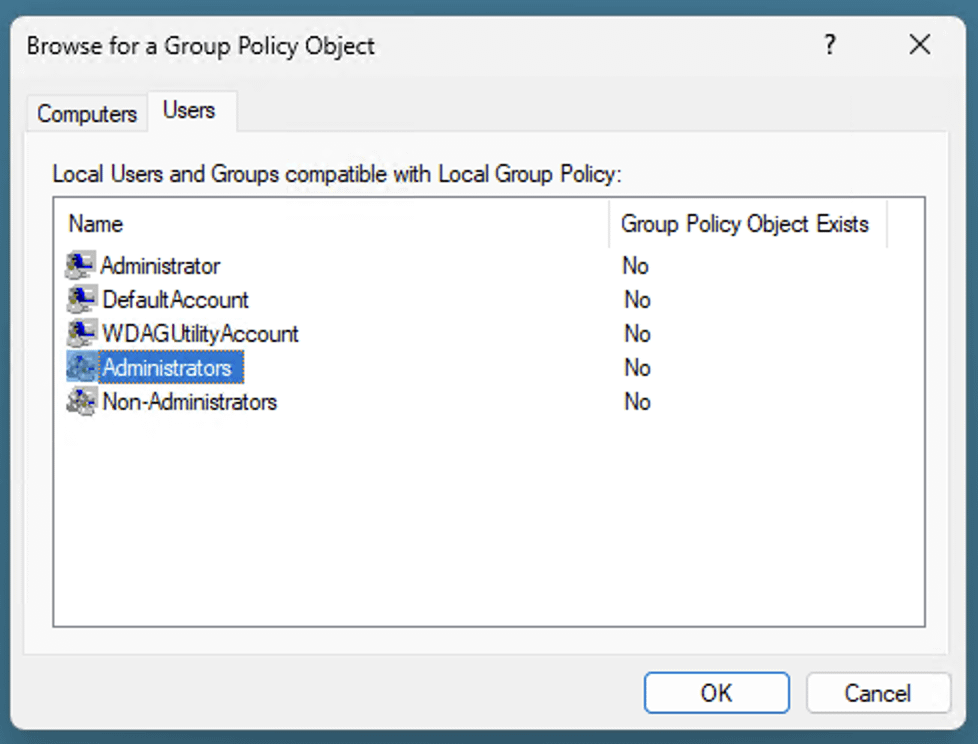
- Click on the Browse button in the Select Group Policy Object window.
- Select the Users tab and then select the Administrators user group (or alternatively, any other user group you want to specifically apply a policy to) and then press OK.
- Click Finish in the Select Group Policy window and then press OK in the Add or Remove Snap-ins window.
- The MMC window will now show your Local Group Policy Editor for administrative users in the navigation pane.
- Select File then Save As, and save this custom MMC view to the desktop as Group Policy Editor for administrative users.
- Now, you can skip all of the above steps whenever you want to manage user policies and use the MMC file saved to your desktop to go directly to the Group Policy Editor for administrators.
Any changes to group policy you make in this MMC window will apply only to administrative users on the local system. For example, you could configure a group policy that hides the desktop Internet Explorer icon for Administrators:
- Open the MMC using the file you created above.
- Navigate to Local Computer/Administrators Policy/User Configuration/Administrative Templates/Desktop.
- Double-click on Hide Internet Explorer icon on desktop setting.
- Select Enabled in the setting window and then click OK.
- To apply the changes, reboot or run the command gpupdate /force from PowerShell or the command prompt.
To reverse this, repeat the above process, but instead of selecting Enabled in the Hide Internet Explorer icon on desktop setting, select Disabled or Not Configured. Thoroughly test any Local Group Policy Objects after configuring them, to ensure that they are having the intended effect.
Troubleshooting common Local Group Policy issues
If the settings configured in Local Group Policy do not have any effect, you can troubleshoot by:
- Checking the policies are assigned to the Administrators user group.
- Making sure that the users you want the settings to apply to are Administrators on the local machine.
If the settings are being applied to non-administrative users instead of (or in addition to) administrative users, check that:
- You’re not assigning the group policy to the machine (which covers all users on it) instead of a user group.
- Your group policy targets the intended user group.
To list all group policies that are in effect, run gpresult /r from the command line. If there are conflicting group policies the most restrictive policy is always applied.
If you make an error when configuring group policies (and can’t figure out which specific policy to undo to put things right), you can revert all group policies by running the following commands as an administrator:
gpupdate /force
secedit /configure /cfg %windir%\inf\defltbase.inf /db defltbase.sdb /verbose
You’ll need to restart your device to complete the process. The command above resets both the computer configuration and user configuration policies.
Why apply Local Group Policy to administrators only?
Usually, Group Policy is used in larger Windows deployments as part of an Active Directory domain for centralized control of multiple Windows devices. However, administrators of smaller deployments for businesses and home users can benefit from creating and managing group policies, as it allows them to do things such as:
- Prevent administrator accounts from being used for non-administrative purposes by blocking apps.
- Prevent administrative users from being able to execute scripts.
- Prevent end users who need administrator accounts for other reasons (like legacy app compatibility) from changing system settings and breaking their machines or disabling critical features such as firewalls or antivirus.
- Prevent users from accessing mail clients or other potential malware vectors while logged in as an administrator.
How to effectively manage Windows Group Policy for multiple devices
Administering a fleet of Windows devices requires central management over a network so that each device is properly configured, changes can be enforced, and so that each device doesn’t have to be manually set up. Windows Group Policy in Active Directory allows you to configure and oversee thousands of Windows machines and users and apply group policies depending on a device’s location, type, or the user’s role.
While Windows’ built-in management tools are robust and proven to be reliable, you can further guarantee the security of your Windows networks by implementing remote management and endpoint protection. This is increasingly critical in the modern cybersecurity landscape: you cannot leave gaps in your network and device configuration that can be exploited.
NinjaOne is a comprehensive end-to-end endpoint management solution for Windows domains. It includes a unified management interface for deploying and managing Windows 11 devices and integration with endpoint protection that helps you manage group policies and ensures that they are fully deployed across your Windows infrastructure.