Security awareness is on the rise in the channel, but, unfortunately, old habits and misconceptions die hard.
This post is a collaboration between:

Jonathan Crowe
Director of Content and Community at NinjaOne
Tom Watson
Channel Chief Advisor at NinjaOne
In a hurry? Watch a 3min video version of this post:
Recently, NinjaOne hosted our second annual virtual MSP Security Summit with the goal of helping MSPs up their game when it comes to security. That goal has only grown in priority since we hosted last year’s event, and this year we were excited to have experts and vendors from a variety of verticals (including a direct competitor) participate and make it a truly channel-wide effort.
As a former MSP owner, Tom came to the event with the goal of identifying key takeaways, and he spent a lot of time thinking about how much has changed when it comes to what is required of an MSP owner today. When he started his MSP business, it was all about technical support. The focus was on hardware and on the software that ran on it. Selling and managing critical items like Microsoft Exchange servers were big business for us, and they required technical skill. As we all know, much of that focus has shifted to the cloud and, overall, the role of the MSP is evolving.
“When it comes to security, gone are the days of installing AV and a firewall and crossing your fingers.”
Tom Watson, Channel Chief Advisor at NinjaOne
We are at a point where MSPs have to embrace the responsibility, be knowledgeable about security, and leverage the right resources to deliver specialized security services to their clients.
That message came up repeatedly during the day’s sessions, which included an in-depth breakdown of recent ransomware campaigns, first-hand lessons from a leading incident response provider, and a walkthrough of how IT services providers can make better use of the tools they already have.
The content and discussion throughout the summit was terrific, but it became clear to us that there are several persistent misconceptions that still serve as stumbling blocks to a large number of today’s MSPs (not to mention their SMB clients). Until these get cleared up, a lack of effective security is going to continue to be an issue, so let’s dive into each below.
Misconception #1: Security expertise is optional
There were numerous wake-up calls throughout the summit, but two of the most memorable came from Alex Fields, author of the popular blog ITProMentor and a Microsoft MVP. Alex made it clear that MSPs need to actively build out their access to security capabilities and expertise for two reasons.
“You can’t outsource your responsibility over IT security.”
Why? For one thing, clients believe everything IT-related falls under your purview. Why should they worry about security? Isn’t that what they hired for you? And to an extent, they have a point. As their provider, you have the keys to the kingdom, and it’s imperative that you take that responsibility seriously. That doesn’t mean you need to take on all that responsibility yourself, directly. Security is a massive field with numerous disciplines, and in many cases, outsourcing particular aspects to trained specialists — incident response, for example — is absolutely the way to go. But that doesn’t remove your responsibility for doing so. Ultimately, the buck stops with you.
“IT support is cost-driven and highly commoditized. It’s a race to the bottom.”
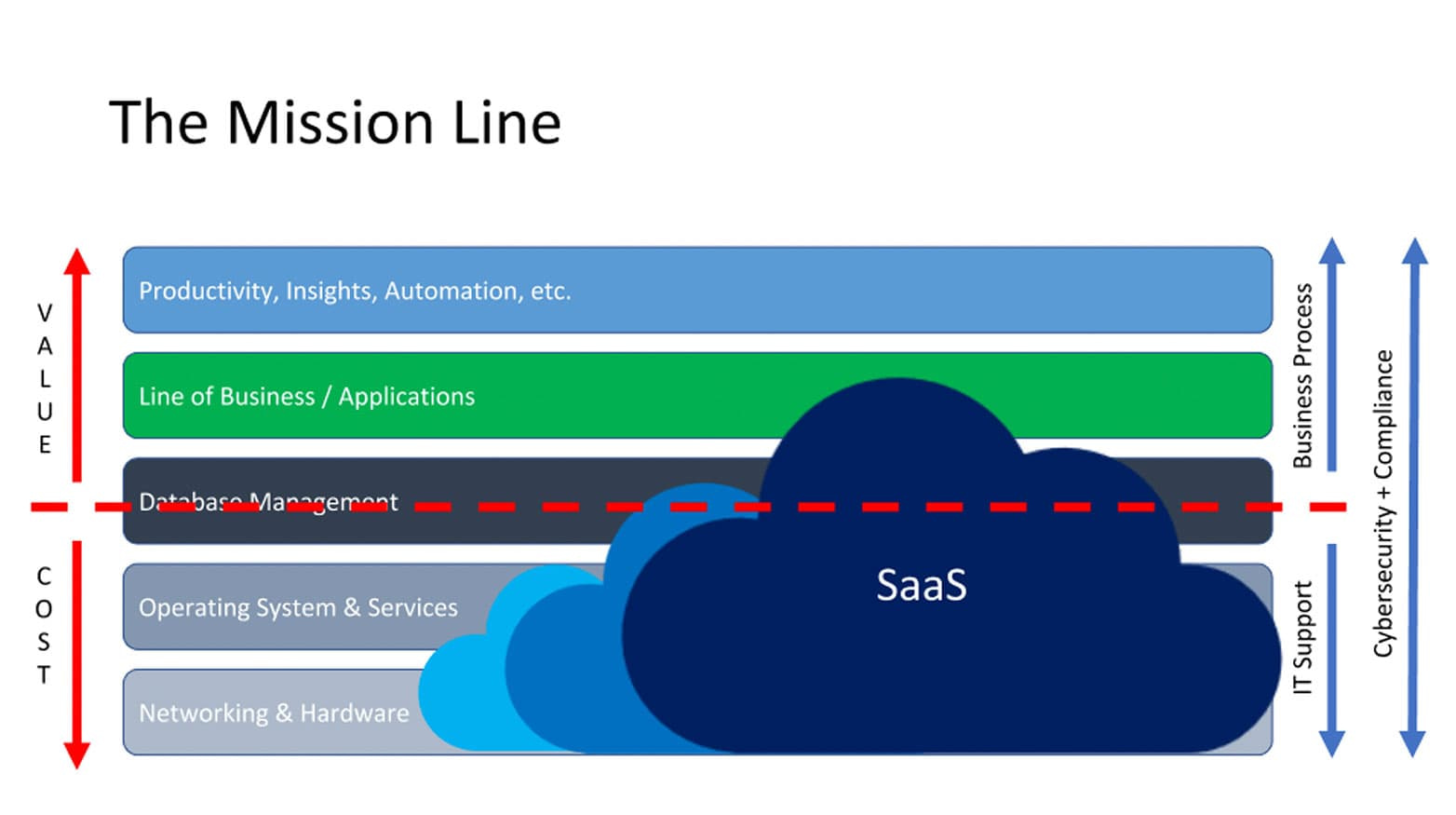
To illustrate that point, Alex shared the following chart, explaining that everything below the “mission line” is tied to traditional IT support, which is viewed by leadership as a cost center. Everything above the line helps the business to fulfill their mission and adds value to the business. Security and compliance requirements exist at each layer and are set to increase over time with the addition of new threats as well as regulations.
Tom’s key takeaway
In order to survive and thrive, MSPs need to find paths towards specializing in managing and securing these areas above the line that are associated with value. If he were starting an MSP today, the standard IT support he provided would be ancillary to his primary offerings, which would be security-focused and tailored to helping businesses scale (automation, productivity, training, etc.).
Misconception #2: Security is purely a technical problem
Speaking of training, we found it interesting that the most technical session of the summit — Huntress Senior Security Researcher John Hammond’s “Analyzing Ryuk” presentation — had this key takeaway:
“User education, while boring and maybe cheesy, is the best we can do right now. You can’t solve this by boarding up the windows and locking the doors. Cybersecurity is not a technology problem. It is a people problem.”
John Hammond, Senior Security Researcher at Huntress
That quote was delivered in the context of John delivering a forensic deep dive into the Ryuk ransomware attack on Universal Health Services (UHS). For all the sophisticated techniques, tactics, and procedures demonstrated during that attack post-exploitation, the initial attack vector was a remarkably common one — a phishing campaign.
While we can and should try to mitigate attacks through software, the fact is many attacks are still coming in through users and lack of enforcement of basic security best practices. We’re talking about shared passwords, users having local admin privileges, lack of MFA and proper network segmentation, exposed RDP and other vulnerable services. The fact is, user education and strong baseline system hardening are just as (if not more) important as managing any security product.
Tom’s key takeaway
If he were running an MSP today, he would put security awareness training very high up in his stack in terms of importance. He would require his employees to be well-versed in best practices, provide them with clear documentation and guidelines, and give them the time and resources necessary to complete required trainings. When it comes to clients, he would make security awareness training and adhering to his company’s security baselines mandatory through his agreements. Failure to comply would be grounds to end a contract. The risk and liability is just too high to both MSPs and their clients to allow for anything less than total compliance when it comes to security protocols.
Misconception #3: The basics are beneath us
We’ve all become conditioned to roll our eyes and shake our heads when we hear another recent ransomware victim was using “admin” as a password or had RDP exposed to the Internet. But we all need to be careful. Arrogance is the kiss of death in security, and as TrustedSec Incident Response Lead Tyler Hudak pointed out, the path to compromises is littered with statements like, “we’re covered there.”
Tyler explained that he has worked on numerous security incidents with MSPs, and on more than one occasion the MSP was adamant that there was no RDP exposed — until a simple scan uncovered that was exactly the case on that one older server that they had simply forgotten about. Making sure is always better than feeling sure, and Tyler recommends routinely checking Shodan to see what is in fact open on your clients’ IP addresses.
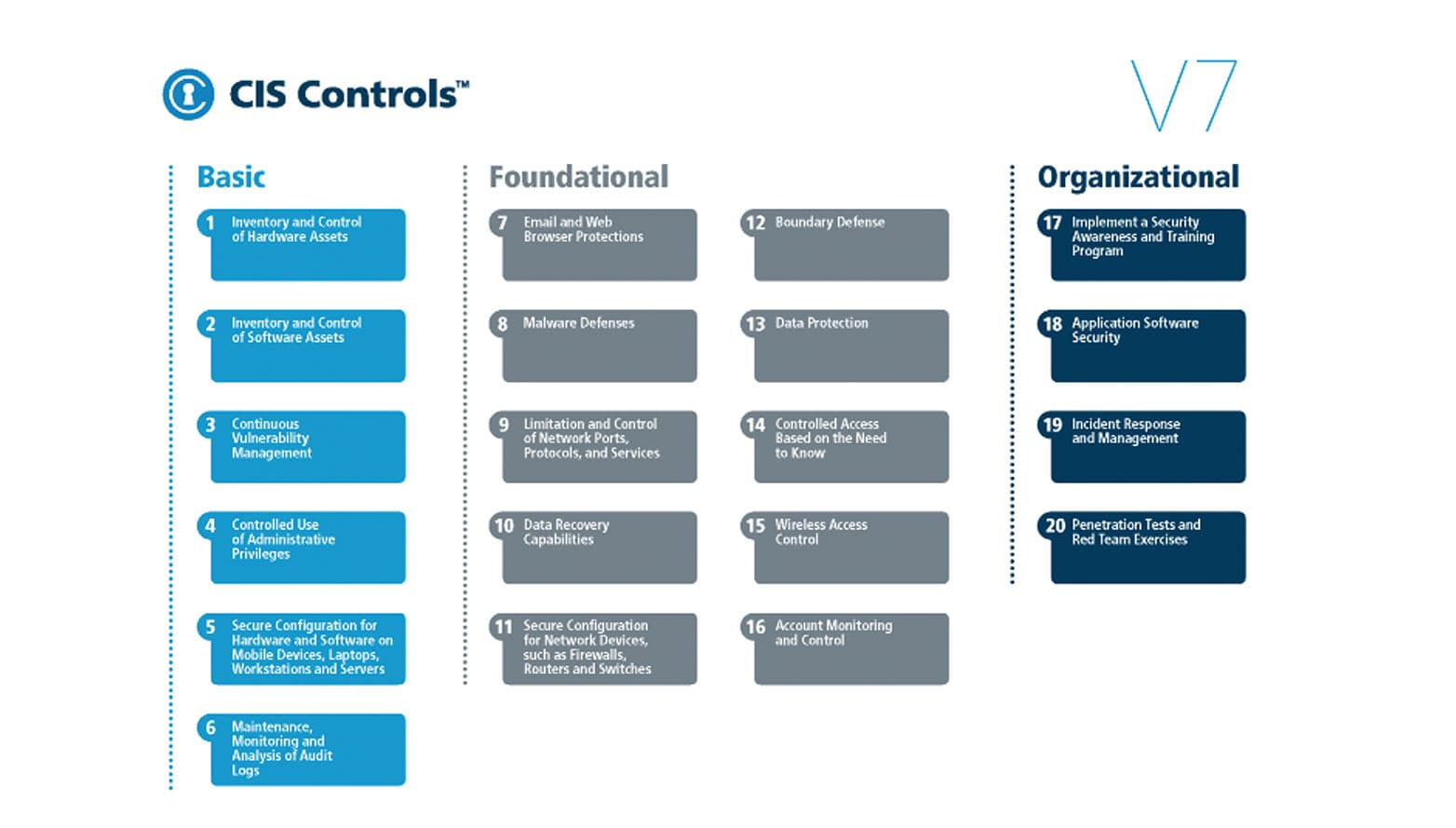
Failing to secure RDP is one of the more egregious examples of failing to cover the basics, but it’s far from the only one. Alex Fields advised that more MSPs need to focus on adopting established standards like the CIS Controls, and that, if you’re not actively addressing at least the first six, you’re bound to have holes that are putting you and your clients at risk.
Tom’s key takeaway
Not only do MSPs need to make the effort to adopt basic CIS Controls standards, they also need to be transparent with their clients and require their buy-in and active involvement, as well.
Misconception #4: Having a plan is enough
Until you’ve experienced one, it’s difficult to fully appreciate how chaotic and stressful an active security incident can be. In his role as an incident responder, Tyler explained that he has often seen both MSPs and internal IT teams be completely overwhelmed. In many of those cases, a lack of policies and procedures means they’re stuck attempting to plan on the fly, which is the last thing you want when the clock is ticking and you’ve got a potential disaster on your hands.
Teams that have incident plans in place can fare better, but even then, if the procedures have never been tested then they, too, can find themselves scrambling to adjust to conditions and scenarios that they hadn’t accounted for.
As Mike Tyson put it, “Everyone has a plan until they get punched in the mouth.”
Incidents will almost always involve unanticipated surprises, but to keep those to a minimum you need to actively work on your preparedness. It’s not enough to have a great playbook. You need to actually practice running the plays and establishing a bit of muscle memory so there’s no hard thinking required in order to act quickly and effectively (even after that initial blindsiding blow).
Tyler recommended that MSPs take the time to conduct tabletop exercises, either on their own or with a dedicated incident response specialist. I realize it is time consuming to run simulations and update “what if” plans, but we are now at a point where we all have to fully embrace the line we deliver to clients and prospects — it’s no longer if you’ll experience a security incident, but when.
Get access to all the MSP Security Summit session on-demand
If you’re interested in hearing more from Tyler, Alex, and John, you can watch recordings of their sessions on-demand here.