With cyber attacks rapidly evolving and becoming more damaging, MSPs are actively seeking out fresh ways to level-up their security offerings beyond traditional antivirus (AV). For many, endpoint detection and response (EDR) tools represent a natural next step. But how many MSPs have actually adopted EDR? What about these EDR tools works — and doesn’t work — for MSPs? And how does that compare with the traction EDR solutions are getting in the internal IT world?
We surveyed 160 MSPs, MSSPs, and IT professionals to find out. But before we see what they said, a quick primer.
What is EDR?
At a high level, endpoint detection and response (EDR) is software designed to help organizations identify, stop, and react to threats that have bypassed their other defenses.
To be even more concise, it doesn’t keep bad stuff out. It lets you know when it’s there so you can respond more quickly.
For a more detailed answer, see our blog post, “What is EDR? A Clear Definition of Security’s Hottest Buzzword.”
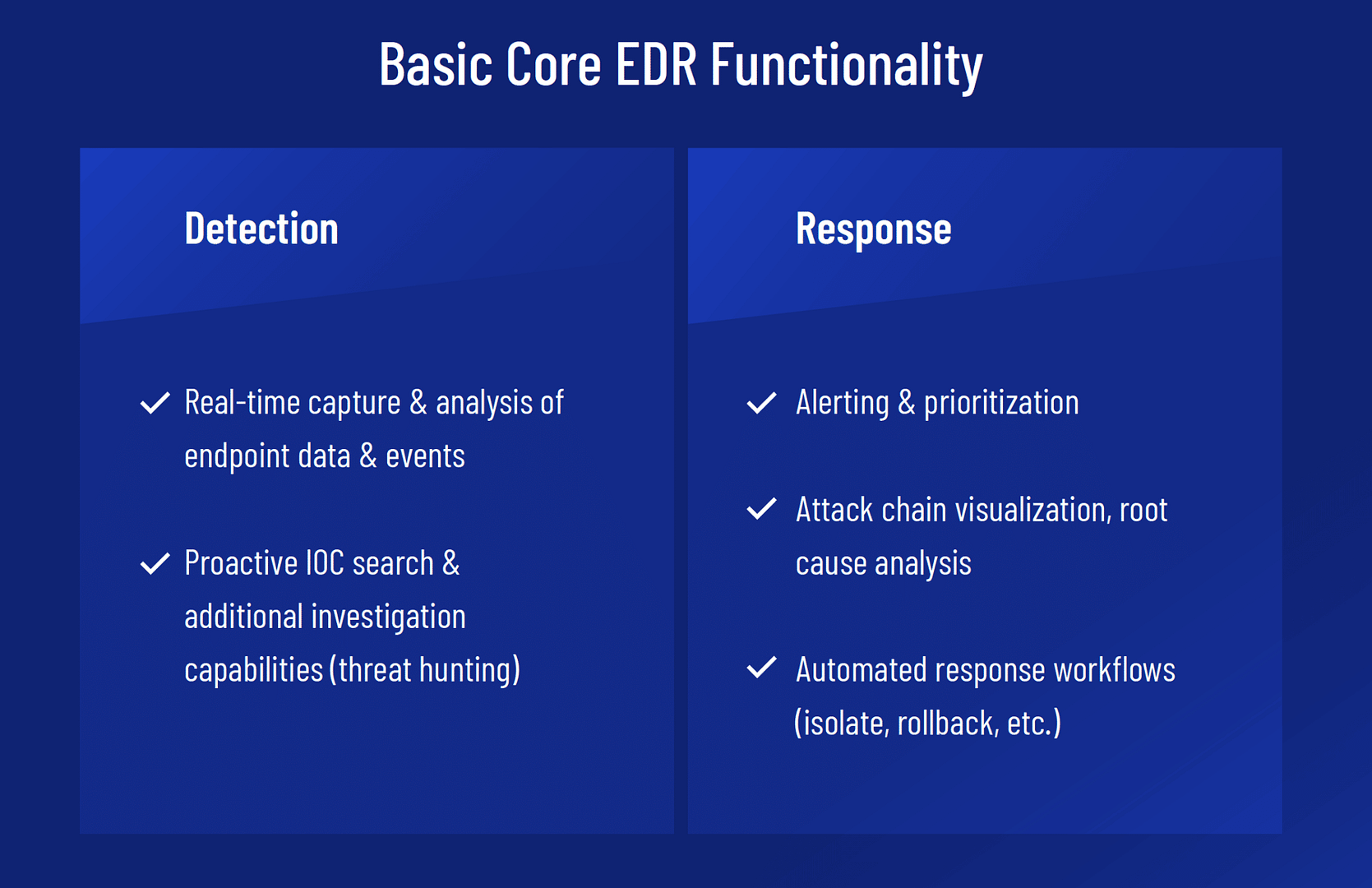
Types of EDR tools
Once strictly limited to large organizations who could afford to retain security analysts, EDR tools have been migrating downmarket. Vendors have made focused efforts to make them more accessible and package them together with other endpoint security solutions to create more appealing all-in-one platforms.
This convergence of solutions geared toward preventing compromises (AVs and NGAVs) and solutions geared toward detecting and responding to compromises (EDR) has made endpoint security an incredibly crowded, competitive, and murky space.
In general, however, the majority of endpoint security vendors now offer EDR in one of three ways:
With that context out of the way, let’s dig into our survey findings.
EDR Survey Findings
Questions we asked:
- Adoption rate: How many MSPs and internal IT pros are utilizing EDR tools?
- How is EDR being added to existing security stacks?
- How many endpoint security tools are respondents currently managing?
- Why are respondents investing in EDR tools?
- What are respondents’ top security priorities and how do those map to EDR?
- How much time are respondents spending managing EDR?
- What challenges are standing in the way of EDR adoption?
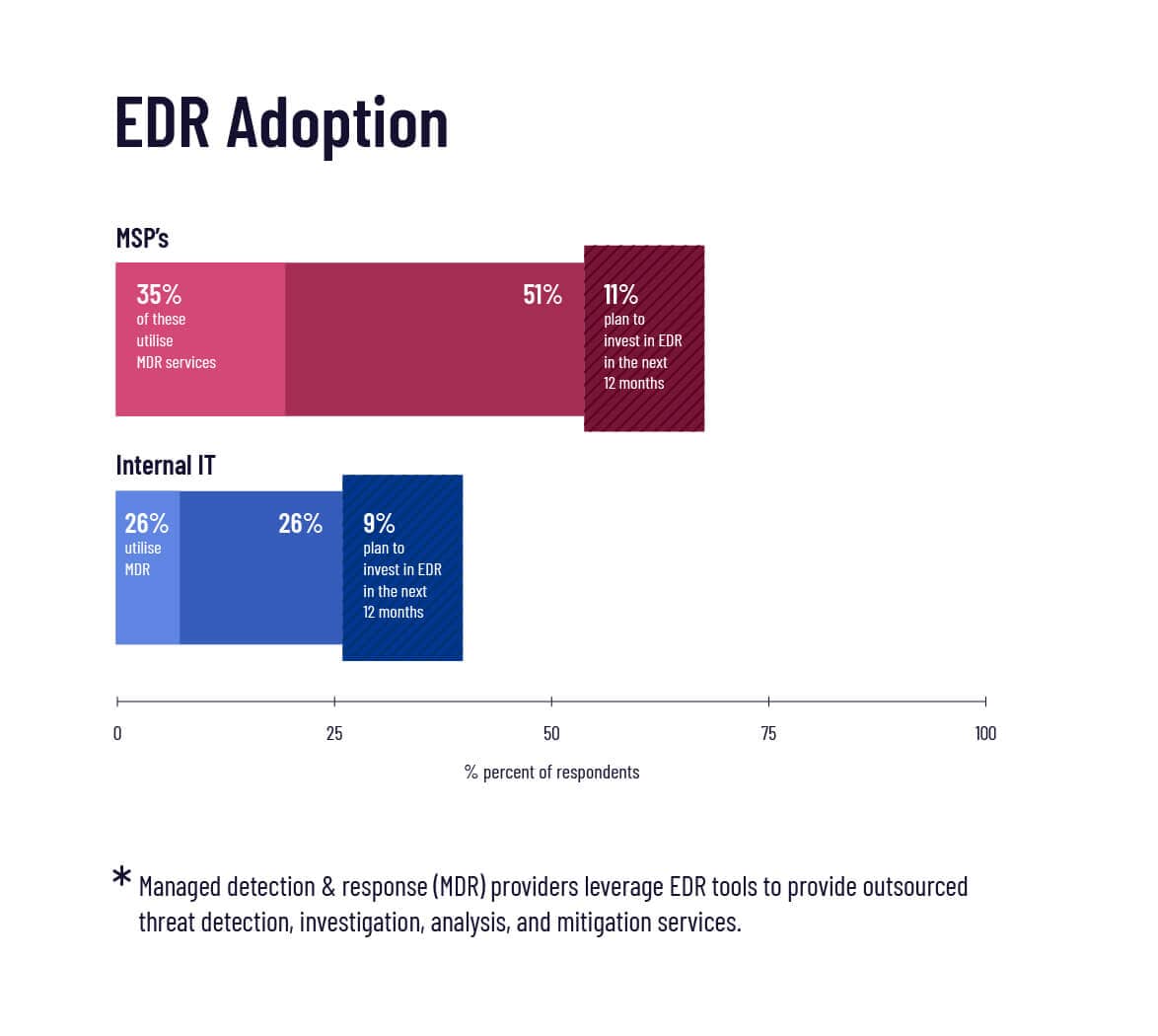
How many MSPs and internal IT pros are utilizing EDR tools?
Half of our MSP respondents indicated they were already utilizing EDR. Of those, a third said they were using a managed detection and response (MDR) provider to help manage it. An additional 11% of MSPs plan on investing in EDR in the next 12 months, which means EDR adoption could be set to reach nearly two thirds of MSPs in 2020.
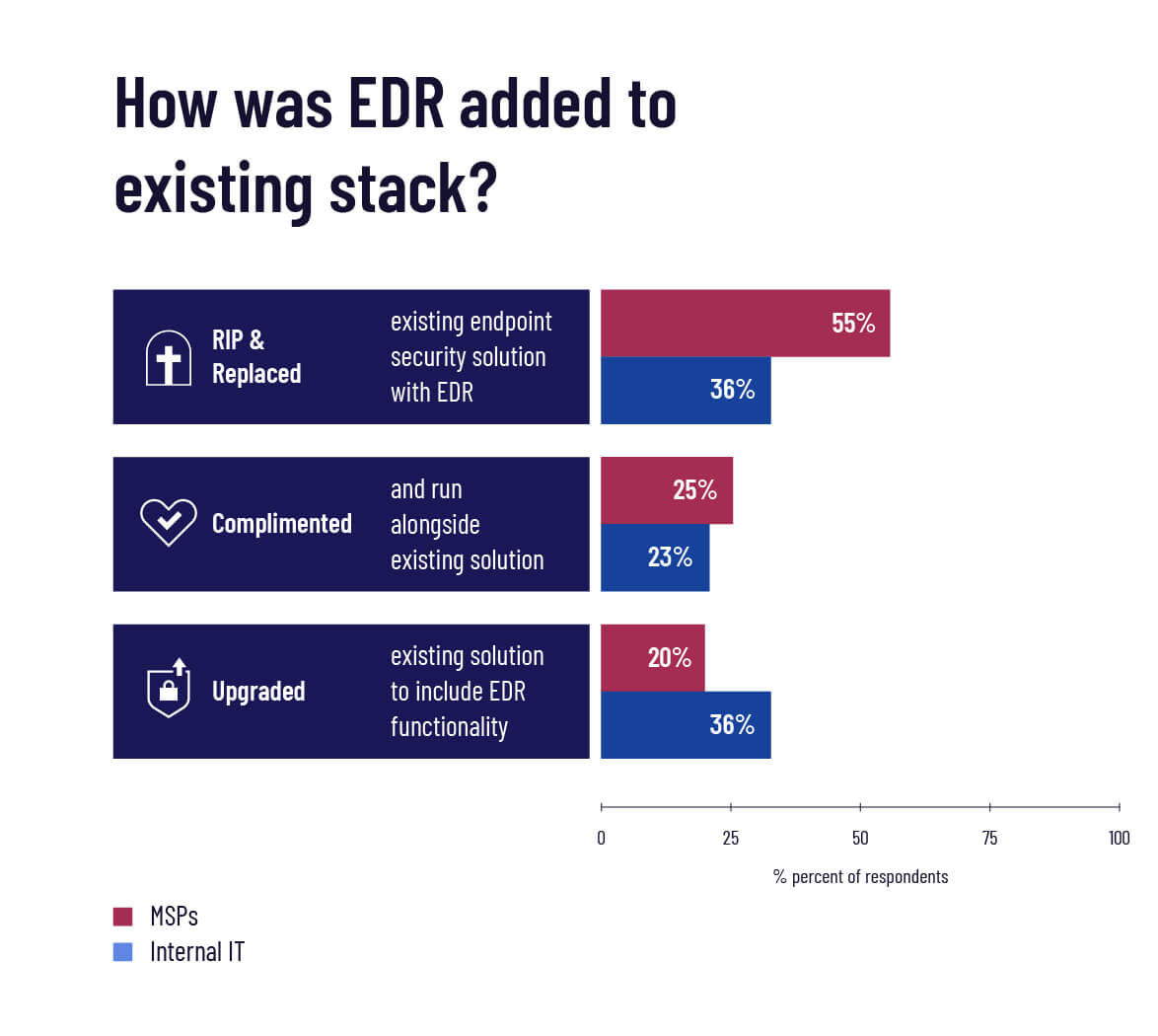
How is EDR being added to existing security stacks?
Here’s a stat that should worry traditional endpoint security vendors:
55% of MSPs who have EDR decided to rip and replace their existing endpoint security solution with it.
That’s one indication of just how brutal the competition in this space is. There’s often no room in a security stack for coming in second.
But what about internal IT pros? Turns out they’re split more evenly between rip and replacing, adding EDR as a complimentary tool, and finding ways to add EDR functionality to their existing solution. So AV vendors can breath a little sigh of relief, right? Well…not quite.
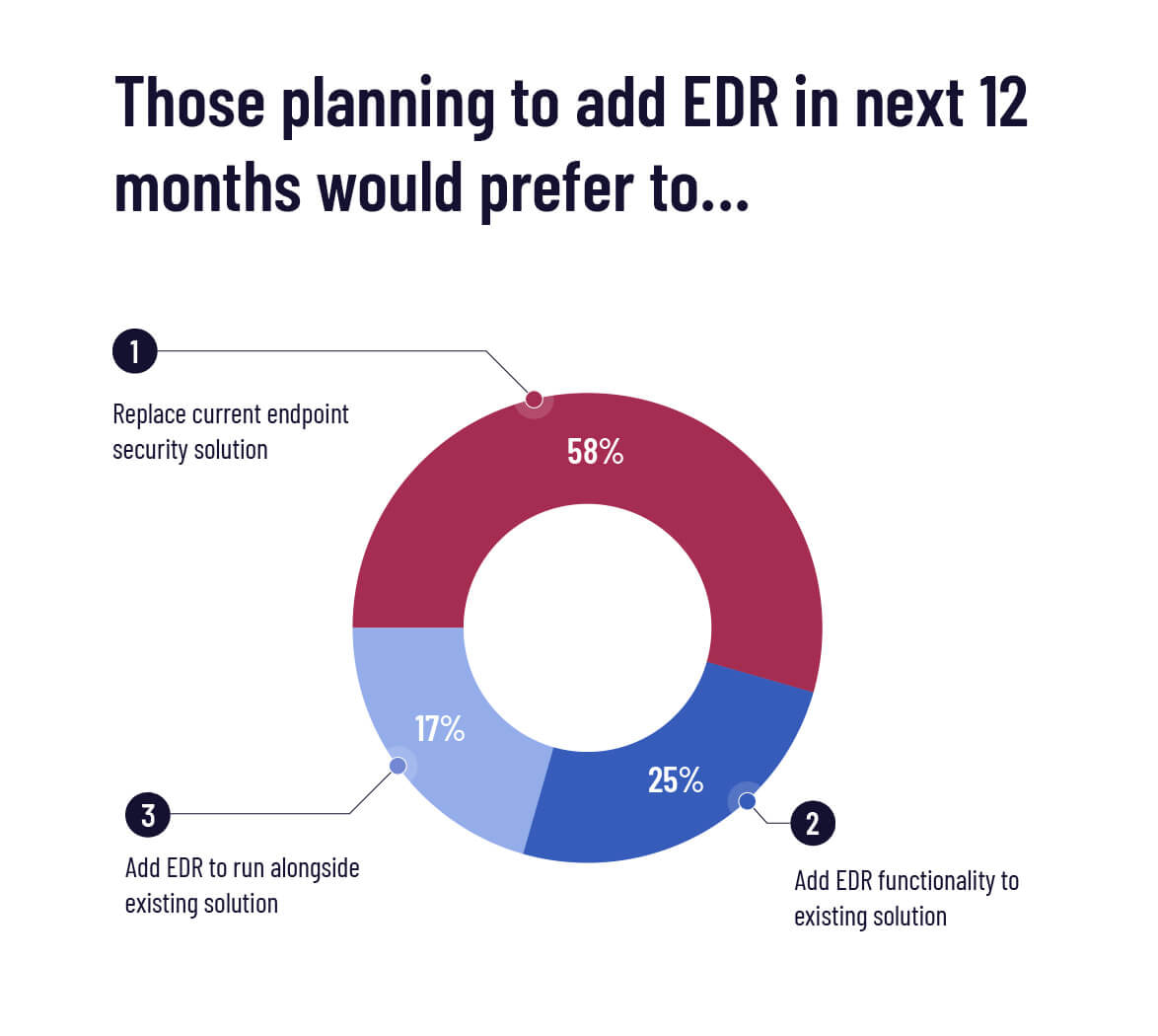
When we asked MSPs and internal IT pros who haven’t yet made the plunge what their ideal scenario would be, the majority said they were leaning towards a rip-and-replace approach.
Seems like many MSPs are looking to take a one-in-one-out approach to managing their stack. That brings us to our next question…
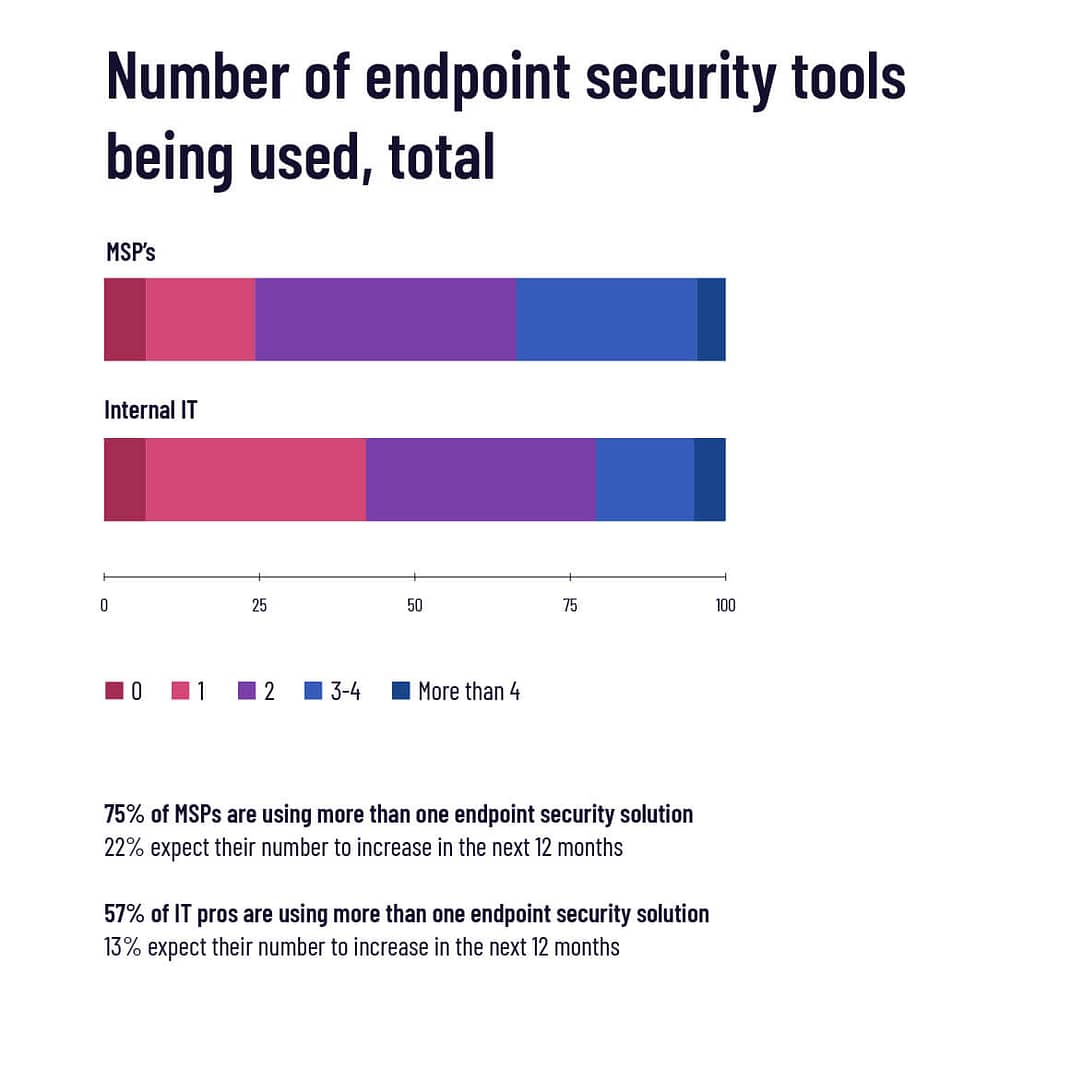
How many endpoint security tools are respondents currently managing?
Perhaps one reason why MSPs in particular are hesitant to simply slap on a layer of EDR is the fact that three out of four are already managing more than one endpoint security solution already. That, and, you know, margins.
Internal IT pros aren’t too far behind, with nearly 6 in 10 saying they use more than one solution.
Few MSPs or IT pros are using more than four solutions, and a relatively small percentage expects the total number of tools they’re managing to grow.
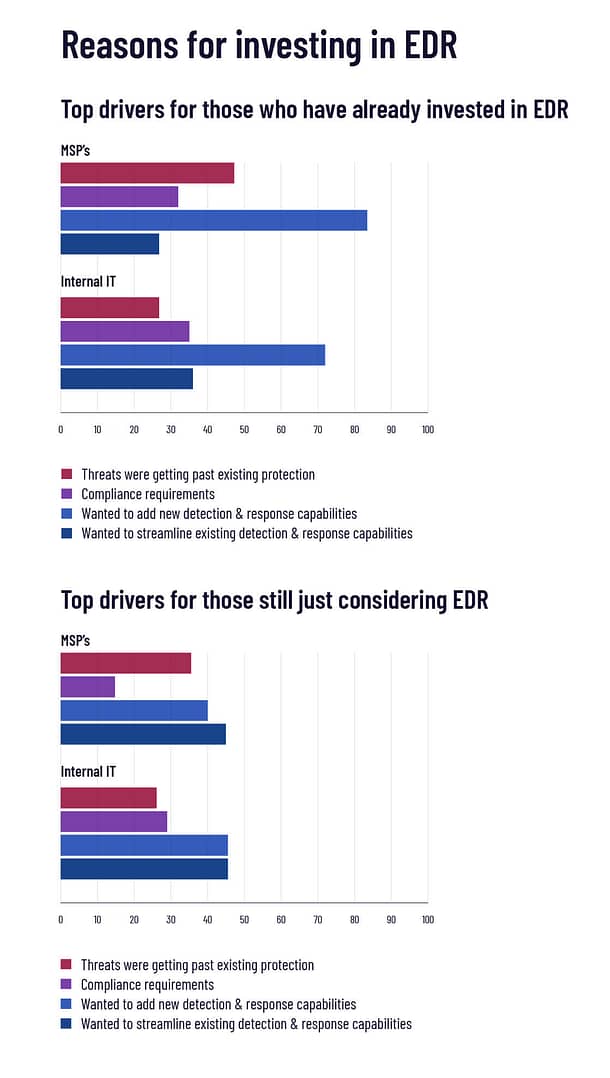
Why are respondents investing in EDR tools?
For both MSPs and IT pros, the top reason for investing in EDR couldn’t be more straightforward — they’re interested in adding detection and response capabilities. But what’s actually interesting is, for MSPs, the second biggest driver was threats bypassing their defenses.
For 45% of MSPs who have EDR, a major driver for adoption was things getting past their AV.
On the face of it, that makes sense, too. Suffer a few infections and the EDR selling point of, “compromise is inevitable” will have you nodding your head. But remember, the majority of MSPs who have invested in EDR didn’t just add it to their stack, they ripped out their existing protection and replaced it with EDR.
This raises another question: are MSPs being drawn to EDR tools for the core EDR functionality — threat investigation and analysis, automated remediation workflows, etc. — or because security vendors are making NGAV functionality a key part of the package?
In other words, are MSPs truly looking for new capabilities, or are they really just looking for a better mousetrap?
Gauging by the next charts — priorities and time spent in EDR tools — there are indications it may often be the latter.
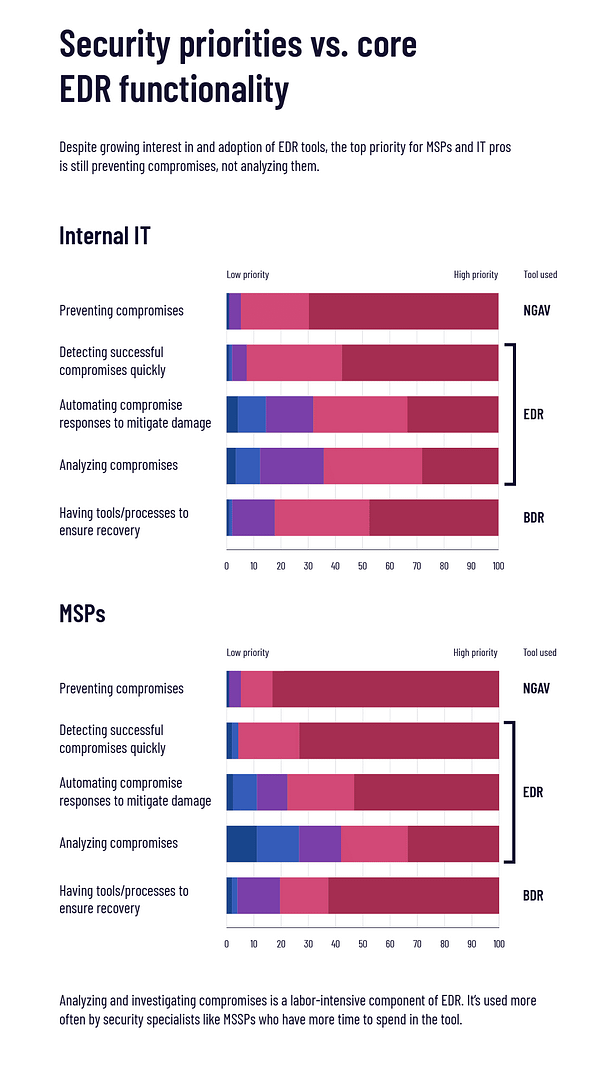
What are respondents’ top security priorities, and how do those map to EDR?
EDR adoption is obviously on the rise, but for now the priority is generally still on preventing compromises (the job of AV/NGAV), not analyzing them (one of the core capabilities provided by EDR).
It’s interesting to note that in addition to being the lowest priority (relatively speaking), analyzing compromises is also the most hands-on and resource-intensive capability on this list, requiring fairly extensive time and expertise to pull off.
Speaking of time…
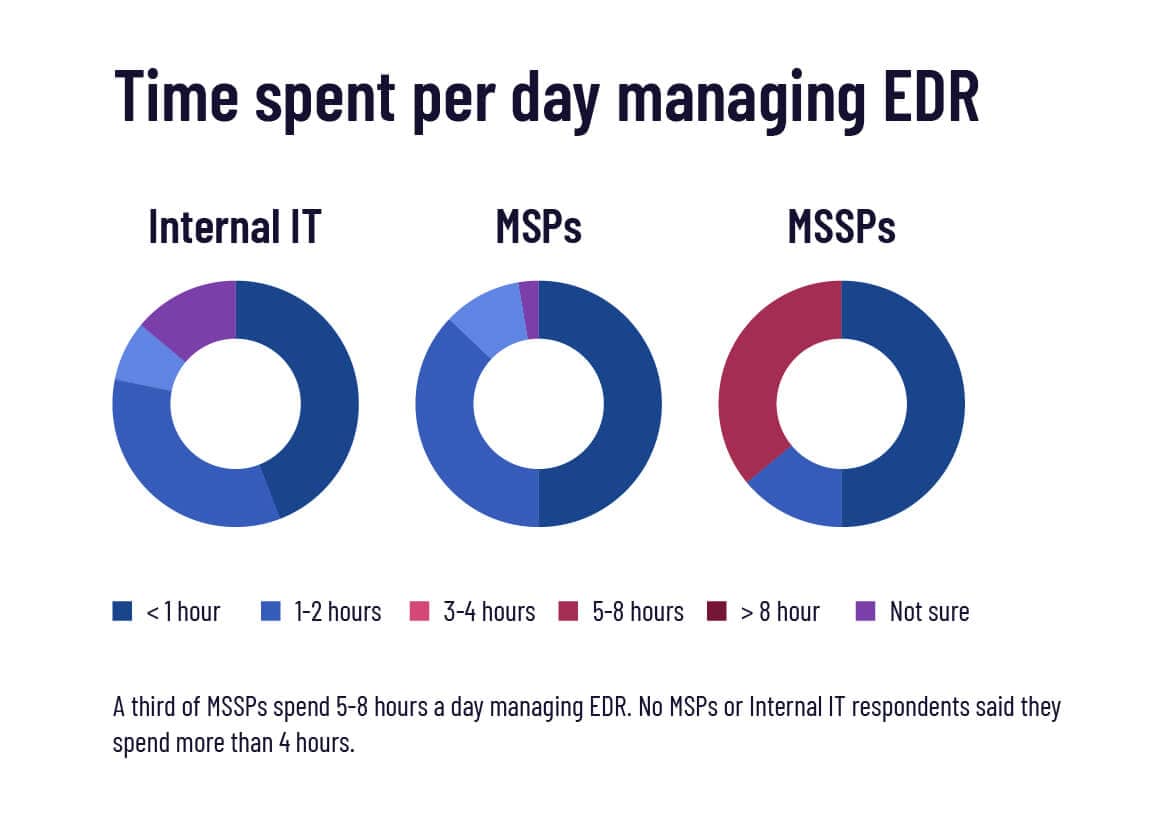
How much time are respondents spending managing EDR?
Very generally speaking, the more security expertise an EDR user has, or the more specialized their role, the more time they devote into fully utilizing it. Case in point: a third of MSSPs spend 5-8 hours a day managing EDR. No MSPs or internal IT respondents said they spend more than 4 hours. Half of the MSP respondents reported they spend less than an hour a day in their EDR.
Maybe no surprise then that only 5% of MSPs said they have a person dedicated to managing EDR. Maybe a little more surprising: 30% of MSPs reported they had no EDR management coverage on nights or weekends.
A third of internal IT respondents said they have a dedicated person managing EDR. 27% said there is no coverage on nights or weekends.
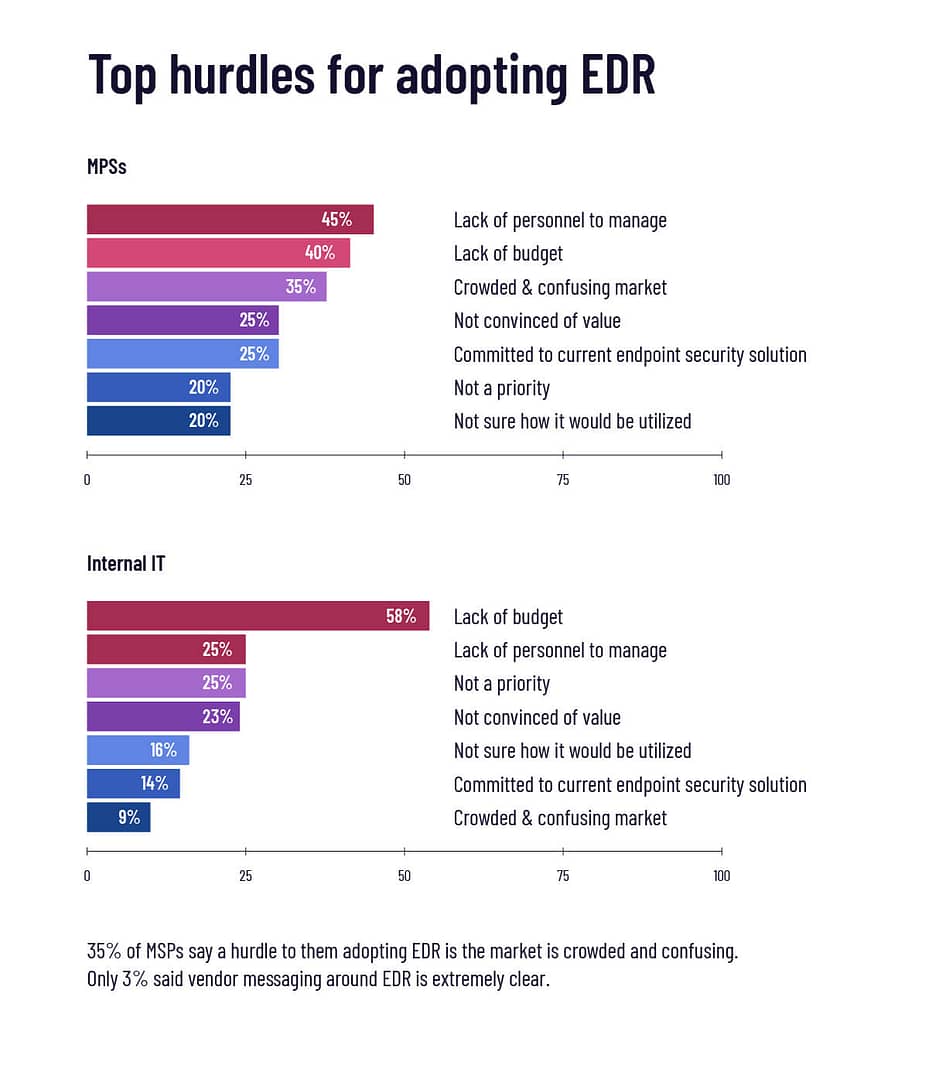
What challenges are standing in the way of EDR adoption?
No surprise that a lack of budget and personnel top the list of speed bumps on the road to EDR adoption. Those things can be challenging to address, but for a third of MSPs a major stumbling block is simply how crowded and confusing this endpoint security market has become.
We can certainly sympathize there. In fact, we’ve put together a free guide to help clear things up.
Want more facts about EDR and tips for evaluating solutions?
Download our free 26-page MSP’s Hype-Free Guide to EDR. It answers all the questions you should be asking about EDR, so when your customers, your boss, or prospects come asking about it, you’ll have answers.