Updated March 16, 2021.
On Tuesday, March 2, Microsoft announced that it had detected a string of four 0-day vulnerability exploits being actively used to attack versions of on-premises Exchange Server. Patches are available, and organizations are being strongly advised to identify, update, and verify vulnerable systems as quickly as possible.
We’ve created this post to collect related resources and information and will be updating it regularly.
Contents
- Overviews
- Threat intel from security firms
- What are the vulnerabilities?
- What versions of Exchange are affected?
- How widespread are attacks?
- How to patch
- Identifying vulnerable servers
- How to identify and investigate compromises
- Video: Get up to speed fast with John Hammond from Huntress
Overviews
The following are great summaries and threads to follow to get up to speed:
- HAFNIUM targeting Exchange Servers with 0-day exploits (Microsoft)
- Includes attack details, specific CVE info, mitigation recommendations, and list of indicators of compromise (IoCs)
- CISA Alert: Mitigate Microsoft Exchange Server Vulnerabilities
Threat intel from security firms
Huntress
Mass exploitation of on-prem Exchange servers (thread on r/msp)
Rapid response thread from Huntress geared specifically towards MSPs, including threat intel and findings from examining their own partner base. Huntress is actively updating as new information becomes available.
Huntress also hosted a webinar on March 4 at 1pm ET and provided a summary of their research and observations so far. Watch on-demand here.
One of the first to identify (January 6!) and report on this activity. This post provides more details on how the vulnerabilities are actually being exploited as well as a short list of observed post-exploitation tactics, techniques, and procedures (TTPs). It also provides additional IoCs.
FireEye
Detection and Response to Exploitation of Microsoft Exchange Zero-Day Vulnerabilities
Also confirms observing abuse in January and contains another nice technical breakdown of the attacks. Contains additional tips for investigating potential compromises (see below).
Red Canary
Microsoft Exchange server exploitation: How to detect, mitigate, and stay calm
Provides a breakdown of the post-exploitation threat activity that Red Canary has identified, along with practical detection opportunities and remediation advice.
CrowdStrike
Falcon Complete Stops Microsoft Exchange Server Zero-Day Exploits
If you can get past the title and sales angle, this post provides additional technical details, IoCs, and a nice threat discovery and hunting recap.
What are the vulnerabilities?
Microsoft has identified four vulnerabilities being actively exploited, but the company’s out-of-band security update also address three additional remote code execution (RCE) vulnerabilities that were not associated with the active attacks.
Initial access
CVE-2021-26855
CVSSv3: 9.1
A server-side request forgery (SSRF) vulnerability in Exchange which allows remote attackers to send arbitrary HTTP requests and authenticate as the Exchange server.
According to security firm Volexity:
This vulnerability is remotely exploitable and does not require authentication of any kind, nor does it require any special knowledge or access to a target environment. The attacker only needs to know the server running Exchange and the account from which they want to extract e-mail.
Successfully exploiting this vulnerability gives an attacker the opportunity to exploit the three additional vulnerabilities below.
Post-authentication remote code execution (RCE)
CVE-2021-26857
CVSSv3: 7.8
According to Tenable, the flaw resides in the Exchange Unified Messaging Service, which enables voice mail functionality in addition to other features. It allows to run code as SYSTEM on the Exchange server, but requires administrator permission or another vulnerability to exploit.
CVE-2021-26858
CVSSv3: 7.8
If attackers are able to authenticate with the Exchange server (either by exploiting CVE-2021-26855 or by compromising a legitimate admin’s credentials) then they could use this vulnerability to write a file to any path on the server.
CVE-2021-27065
CVSSv3: 7.8
Ditto.
Notes on post-exploitation activity
As FireEye, Volexity, and others have reported, attackers have abused these vulnerabilities to drop web shells, including variants of China Chopper. These give the attackers the ability to set the stage and perform a variety of post-exploitation activity.
Observed TTPs include:
- Credential theft using ProcDump (legitimate Windows Sysinternals tool) to dump LSASS process memory
- Data exfiltration, including Exchange offline address books
- Exporting mailbox data via Exchange PowerShell Snap-ins
- Establishing remote access via PowerCat and other attack frameworks
For more info on post-exploitation threat activity, see Red Canary’s research.
“Bonus” unrelated vulnerabilities
In addition to these zero-day vulnerabilities, Microsoft also patched the following unrelated RCE flaws:
- CVE-2021-26412 (CVSSv3: 9.1)
- CVE-2021-26854 (CVSSv3: 6.6)
- CVE-2021-27078 (CVSSv3: 9.1)
What versions of Exchange are affected?
As Huntress succinctly put it during their webinar: all of them.
- Exchange Server 2010
- Exchange Server 2013
- Exchange Server 2016
- Exchange Server 2019
Note: Microsoft has confirmed that Exchange Online is NOT affected.
How widespread are attacks?
Despite Microsoft initially describing attacks as being “limited and targeted,” subsequent findings from other vendors and researchers indicate activity has been much more widespread and indiscriminate.
Update: Estimated at least 30,000 U.S. organizations compromised
On Friday, March 5, Brian Krebs reported that multiple sources were estimating hundreds of thousands of organizations had been compromised worldwide, with 30,000 organizations compromised in the U.S. alone.
Wired journalist Andy Greenberg later confirmed:
Confirming @briankrebs reporting that Chinese group Hafnium has now exploited Microsoft Exchange zero-days to hack tens of thousands of networks. One researcher says 30k servers in the US alone, hundreds of thousands globally. “China just owned the world.” https://t.co/C1FkmBVLNI
— Andy Greenberg (@a_greenberg) March 6, 2021
The U.S. Computer Emergency Readiness Team (US-CERT) characterized exploitation as widespread, and emphasized all organizations across all sectors should follow mitigation guidance.
CISA urges ALL organizations across ALL sectors to follow guidance to address the widespread domestic and international exploitation of Microsoft Exchange Server product vulnerabilities; see CISA’s newly released web page for details. https://t.co/VwYqAKKUt6. #Cyber #InfoSec
— US-CERT (@USCERT_gov) March 9, 2021
Compromised organizations include local governments, wide variety of SMBs
According to Huntress Senior Researcher John Hammond, compromised victims they’ve identified include small hotels, an ice cream company, a kitchen appliance manufacture, multiple senior citizen communities and other “less than sexy” mid-market businesses. Huntress has also observed many city and county government victims, healthcare providers, banks/financial institutions, and several residential electricity providers.
Out of roughly 2,000 Exchange servers they investigated, nearly 200 had been compromised with web shell payloads present.
Multiple threat actor groups are actively abusing the vulnerabilities
While Microsoft attributed the campaign it observed with high confidence to China-based threat actor HAFNIUM, ESET has reported seeing seeing other groups getting into the mix.
ESET telemetry shows that (at least) CVE-2021-26855 is actively exploited in the wild by several cyber-espionage groups. Among them, we identified #LuckyMouse, #Tick, #Calypso and a few additional yet-unclassified clusters. 2/5
— ESET research (@ESETresearch) March 2, 2021
Update: ESET has released new research indicating at least 10 APT groups are actively exploiting the vulnerabilities.
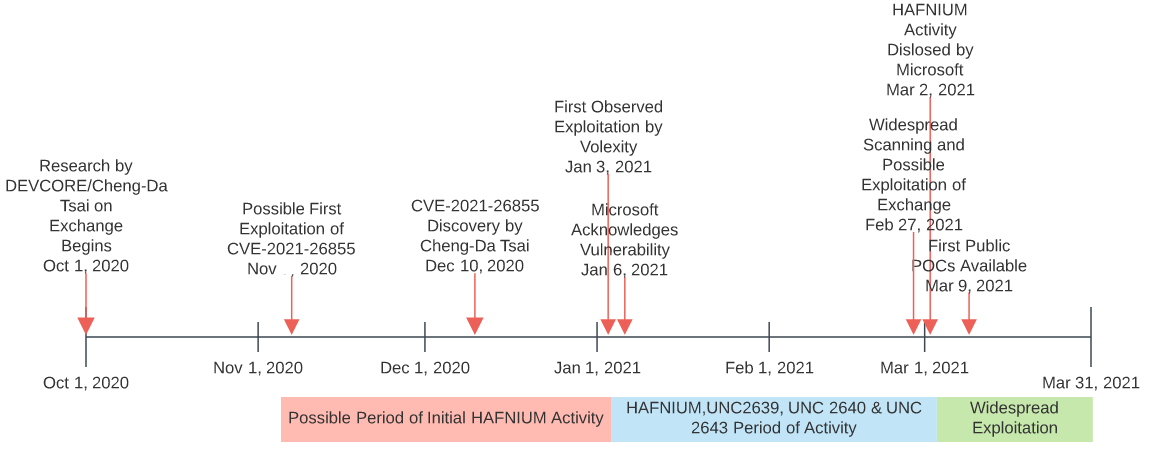
Earliest attacks identified on January 6, 2021
Brian Krebs has put together a high-level timeline that indicates Microsoft was notified of one of the vulnerabilities on January 5. One day later, security firm Volexity identified attacks in the wild.
- Jan. 5: DEVCOR alerts Microsoft of its findings.
- Jan. 6: Volexity spots attacks that use unknown vulnerabilities in Exchange.
- Jan. 8: DEVCOR reports Microsoft had reproduced the problems and verified their findings.
- Jan. 11: DEVCOR snags proxylogon.com, a domain now used to explain its vulnerability discovery process.
- Jan. 27: Dubex alerts Microsoft about attacks on a new Exchange flaw.
- Jan. 29: Trend Micro publishes a blog post about “Chopper” web shells being dropped via Exchange flaws.
- Feb. 2: Volexity warns Microsoft about active attacks on previously unknown Exchange vulnerabilities.
- Feb. 8: Microsoft tells Dubex it has “escalated” its report internally.
- Feb. 18: Microsoft confirms with DEVCOR a target date of Mar. 9 (tomorrow) for publishing security updates for the Exchange flaws. That is the second Tuesday of the month — a.k.a. “Patch Tuesday,” when Microsoft releases monthly security updates (and yes that means check back here tomorrow for the always riveting Patch Tuesday roundup).
- Feb. 26-27: Targeted exploitation gradually turns into a global mass-scan; attackers start rapidly backdooring vulnerable servers.
- Mar. 2: A week earlier than previously planned, Microsoft releases updates to plug 4 zero-day flaws.
- Mar. 3: Tens of thousands of Exchange servers compromised worldwide, with thousands more servers getting freshly hacked each hour.
- Mar. 5: KrebsOnSecurity breaks the news that at least 30,000 organizations in the U.S. — and hundreds of thousands worldwide — now have backdoors installed.
- Mar. 5: Wired.com confirms the reported number of victims. White House expresses concern over the size of the attack. Former CISA head Chris Krebs tweets the real victim numbers “dwarf” what’s been reported publicly.
- Mar. 6: CISA says it is aware of “widespread domestic and international exploitation of Microsoft Exchange Server flaws.”
- Mar. 7-Present: Security experts continue effort to notify victims, coordinate remediation, and remain vigilant for “Stage 2” of this attack (further exploitation of already-compromised servers).
Timeline created by Brian Krebs
Update: New research indicates exploitation could extend all the way back to November 2020.
Source: Examining Exchange Exploitation and Its Lessons for Defenders by Joe Slowik
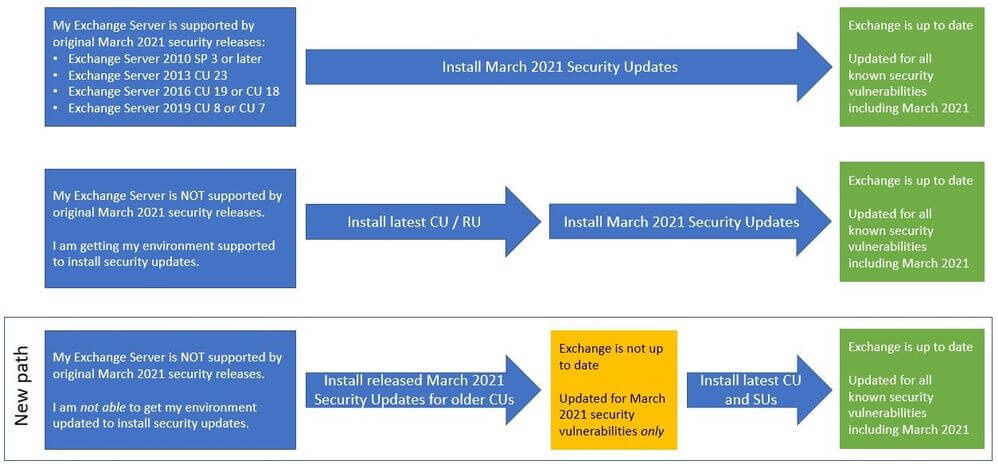
How to patch
Chart from Microsoft illustrating three paths for applying Exchange updates
Security updates addressing these vulnerabilities are available for the following specific versions of Exchange:
- Exchange Server 2010 (update requires SP 3 or any SP 3 RU – this is a Defense in Depth update)
- Exchange Server 2013 (update requires CU 23)
- Exchange Server 2016 (update requires CU 19 or CU 18)
- Exchange Server 2019 (update requires CU 8 or CU 7)
Note: If you’re installing these manually you need to do so as an admin. Otherwise, there is a known issue. As Microsoft security researcher Kevin Beaumont points out, there has been some confusion around the need to have servers running one of the last two Cumulative Updates (CU).
Lots of confusion on this – the Exchange vulnerability applies to all versions.
You’re only protected if you’re on the latest Cumulative Update (CU) AND install the new Security Update (SU). https://t.co/i9QPBJaOZA
— Kevin Beaumont (@GossiTheDog) March 3, 2021
Microsoft provides more clarity here:
These fixes can be installed only on servers that are running the specific versions listed previously, which are considered up to date. If your servers are running older Exchange Server cumulative or rollup update, you will need to install a currently supported RU/CU before you can install the security updates.
Need help finding the right CU to install?
Michel de Rooij is a hero and has download links for Cumulative Updates listed by Exchange versions that also includes build numbers and release dates.
Update: On an out-of-support CU and can’t get the latest updates?
Microsoft has started providing security updates (SUs) that can be applied to some older, unsupported CUs. These updates only contain fixes for the 0-day CVEs and are available only through the Microsoft Download Center (not Microsoft Update). You can find more details and installation instructions here.
Note: Microsoft stresses these SUs are, “intended only as a temporary measure to help you protect vulnerable machines right now. You still need to update to the latest supported CU and then apply the applicable SUs.”
** If you can’t patch immediately, do this as a temporary mitigation **
For organizations unable to patch, Microsoft has provided the following recommendation as a stopgap mitigation:
Implement an IIS Re-Write Rule and disable Unified Messaging (UM), Exchange Control Panel (ECP) VDir, and Offline Address Book (OAB) VDir Services
- These mitigations have some known impact to functionality described below in detail.
- These mitigations are effective against the attacks we have seen so far in the wild but are not guaranteed to be complete mitigations for all possible exploitation of these vulnerabilities.
- This will not evict an adversary who has already compromised a server.
- This should only be used as a temporary mitigation until Exchange servers can be fully patched.
Details and PowerShell scripts provided by Microsoft here.
** Note: Neither patching nor these mitigations will address compromises **
As Microsoft stresses, these are not a remediation if your Exchange servers have already been compromised. For help determining that, see below.
** Update: Microsoft releases “1-click mitigation tool” designed for orgs w/o internal IT or security teams **
Microsoft has released a new, one-click mitigation tool to help customers who do not have dedicated security or IT teams to apply the Exchange security updates
1⃣ Applies CVE-2021-26855 mitigation
2⃣ Runs MSERT scan
3⃣ Reverse any changes made by identified threats pic.twitter.com/UEhNQC8NEM
— Tanmay Ganacharya (@tanmayg) March 15, 2021
Details for the tool can be found via Microsoft here.
Identifying vulnerable servers
Due to the volume of active scanning and exploitation, combined with the risk involved, Huntress and other security providers are advising to trust but verify. Patches should be validated and MSPs should actively scan their client networks to ensure there’s not a surprise server that’s been forgotten. All it takes is one.
Kevin Beaumont has developed a simple Nmap script you can utilize here.
I made a quick and dirty nmap script which can be used to find potentially vulnerable servers in your environments.
I would strongly encourage orgs to assess their Exchange on prem footprint, in particular if it is internet facing. https://t.co/8MCOrhIjQ5
— Kevin Beaumont (@GossiTheDog) March 2, 2021
Note: If you used the above script to scan environments with Exchange 2013 prior to March 7, you should scan again.
Researchers at Rapid7 identified a flaw in the script that was causing it to report false negatives for Exchange 2013 servers, specifically.
The script has since been updated and the issue resolved.
If you’re a paying Shodan Monitor customer you can even automatically get a notification if a vulnerable server is detected.
We added detection for the recent Microsoft Exchange vulnerabilities. If you’ve configured Shodan Monitor (https://t.co/pVAnB0gecF) then you will automatically get a notification. pic.twitter.com/Sbi2VVAFKh
— Shodan (@shodanhq) March 4, 2021
Identifying and investigating compromises
Update: Microsoft has updated its Microsoft Support Emergency Response Tool (MSERT) to detect and remove malware associated with compromise.
Microsoft Defender has included security intelligence updates to the latest version of the Microsoft Support Emergency Response Tool (MSERT) to detect and remediate the latest threats known to abuse the Exchange Server vulnerabilities disclosed on March 2, 2021.
— Tanmay Ganacharya (@tanmayg) March 6, 2021
That’s great news as it provides protection for organizations with servers that don’t have Defender for Endpoint installed.
Microsoft has also outlined a variety of detection opportunities, and has created a script you can use to scan Exchange log files for them.
You can also find lists of IoCs here:
- Hashes and paths from Microsoft
- IoCs from Volexity
- Inventory of China Chopper ASPX web shells from Huntress
In addition to providing IoCs, FireEye also recommends checking the following for potential evidence of compromise:
- Child processes of C:WindowsSystem32inetsrvw3wp.exe on Exchange Servers, particularly cmd.exe.
- Files written to the system by w3wp.exe or UMWorkerProcess.exe.
- ASPX files owned by the SYSTEM user
- New, unexpected compiled ASPX files in the Temporary ASP.NET Files directory
- Reconnaissance, vulnerability-testing requests to the following resources from an external IP address:
- /rpc/ directory
- /ecp/DDI/DDIService.svc/SetObject
- Non-existent resources
- With suspicious or spoofed HTTP User-Agents
- Unexpected or suspicious Exchange PowerShell SnapIn requests to export mailboxes
** If you suspect a server has been compromised **
- Initiate your incident response plan / contact an incident response provider (don’t hesitate to get help from experts if you don’t have IR experience in-house)
- Isolate the server
- FireEye recommends preserving the following artifacts for forensic analysis
- At least 14 days of HTTP web logs from the inetpubLogsLogFiles directories (include logs from all subdirectories)
- The contents of the Exchange Web Server (also found within the inetpub folder)
- At least 14 days of Exchange Control Panel (ECP) logs, located in Program FilesMicrosoftExchange Serverv15LoggingECPServer
- Microsoft Windows event logs
- Restore Exchange to before the first-known incident (current reports indicate January 5)
- Patch or apply stopgap mitigations
- Conduct a full audit to check for the following:
- New users and privileged users (use your RMM and PowerShell)
- Password change dates
- Forwarding for mailboxes
- Forwarding/redirects on inbox folders
- Change domain passwords
- Stay vigilant and up-to-date on new threat intel
Video: Get up to speed fast with John Hammond from Huntress
I had the chance to talk with John about his team’s research, hear what’s surprised him, and get his recommendations for how MSPs should respond.
Transcript
Jonathan: Hey everybody. I’ve got John Hammond with me from Huntress. And of course the topic that we’re talking about is Microsoft Exchange and the zero day vulnerabilities being actively exploited. It’s been a crazy week. John you’re running on like pure adrenaline and fumes at this point. You guys have been up for days. You started a Reddit thread and have been all over this from the get-go, constantly updating it with the things that you’re finding. How you doing? How you hanging in there?
John: Thanks Jonathan. I’m doing all right. We are kind of running on fumes. I was kidding with you earlier. I’ve got my energy drink here. Just keeping me up to date. But we’re staying busy. We’re trying to update indicators of compromise. We’re trying to produce a webinar that we’re going to be going live with this afternoon at 1:00 pm ET. So we’re just trying to educate the community and spread the awareness.
Jonathan: Yeah. Absolutely. I’m going to include a link to that Reddit thread because you guys have done an amazing job including what you said IOCs also just updates of what you found on your end and it’s really been through the night you were calling Partners at 2 am to help them figure this stuff out and we’ve seen a lot of questions going around and at this point, I think it’s safe to say that a lot of people have taken initial steps. There’s some tools out there that people have shared around scanning just to discover vulnerable servers. There’s patches from Microsoft, but there’s a lot of questions around. Okay, if I have found IOC’s what do I do now? Do you have any suggestions for kind of what you’ve seen first of all with those IOCs, and then mitigation steps?
John: Yeah. So the immediate obvious is patch. Once you’ve done that actually if you could validate your patch that’s kind of the next step. Kevin Beaumont has put out a great Nmap scripting engine just a utility you can use with Nmap to externally validate and make sure hey you were no longer vulnerable and after that do your typical necessary restoration response. Restore your Exchange Server if you can to prior the first known incident. Review your domain. Users and computers, make sure there aren’t any changes or any modifications, new administrators in the Exchange groups. That is critical. And change all those domain passwords. We say that all the time but you just have to. Rinse and repeat, flush things out, and then monitor for these IOC’s, stay up-to-date with the threat intelligence. And if you happen to see anything new if you happen to see, oh, I’ve got a different webshell that uses a different argument where I see a different IP address being communicated. Yes, we realize that’s bad, but please please please tell the community. Tell the rest of us so we can kind of continue the hunt because that’s what we’re all about.
Jonathan: You guys have been such great contributors to the community doing this, taking the lead and really sharing a lot of this information. Is there anything new in that regard that you’re seeing in terms of IOCs or new activity now that the cat is kind of out of the bag?
John: Absolutely. So we’ve been fighting this for as much as we can, right. When we’re sharing this information it is is nice and wonderful to see some others trust in Huntress. So as we’re seeing new partners and new individuals kind of get to know our dashboard. Our inventory of Exchange servers is going up, so over this past day. we’ve seen like an addition of a thousand new Exchange servers so that brings our number up to what 3,000 or so, and the number of compromises also goes up. Now we’re up to about 300 or so and we’re keeping tabs of okay, what versions are out there? How many have patched? I think we have about 900 out of that 3,000 pool, but it’s incredible to see the statistics. It’s incredible to see the data but it goes to show that this threat is still out there. The infected hosts are still being infected. The attackers are scanning the Internet and this hasn’t come to an end just yet.
John: To that point, going back quickly to Microsoft’s announcement. They stress that this was at least when they announced a limited targeted exploitation. They were seeing and of course now, you’re your findings kind of indicate that maybe this is a little bit more broader. I mean you’re seeing a variety of victims here, seems like this is kind of indiscriminate. Maybe not early on but at least at this point.
John: I tend to agree. Truthfully, that mention from Microsoft is hey, this is limited and targeted attacks. Truthfully, we disagree. We’re seeing this at a bit of a larger scale between the whole gamut, right? This is all across the board ice cream shop, small hotels, the mom-and-pop shop down the corner all the way up to government, city and county government organizations financial and banking institutions, health care providers and even electrical providers. This has kind of been everywhere from what we’ve seen. And it’s caused a ton of pain obviously with with clients and then with MSPs. I mean, this has been a frantic week for a lot of folks even if a lot of MSPs who have migrated the majority of their clients and have those handful of servers that are still out there.
Jonathan: Another question that comes up: post exploitation activity. What were these guys trying to do? There’s a lot of questions around this in terms of people have found webshells. Is there any other activity? We’ve seen Microsoft reference some other attack tools Procdump being one of them, a couple of exploitation frameworks being dropped in some cases. Have you guys seen those things any and any other indication of further activity that you can share?
John: We haven’t ourselves personally been able to dive into the whole post exploitation or what the attackers have been doing next truthfully. We just focus and kind of zoom in on like hey, it’s bad. We know it’s bad. We got to get it out of there, but from the other from the threat intelligence in the community. We are seeing those Procdump instances or it’ll try and grab credentials or hashes out of memory. We’re seeing kind of the utility of the net.exe, the Windows command line tool, some living off the land binary to add and remove administrators, or some Powersploit tools or Powercat to be able to kind of get connections back and forth. We’re seeing reverse shells through PowerShell. There’s certainly been more to this but we don’t exactly know. Where is it going to go next? They have command control. They have remote access RCE with this webshell. Is that going to mean ransomware? Is that going to mean data exfiltration? Is that going to mean cryptocurrency mining? We aren’t quite sure yet, but we’re still in the fight.
Jonathan: Well, John, thank you so much for joining in. You guys are going to be going over a ton of what you found and much further detail today at 1:00 pm ET for your webinar. We’ll drop a link for people to register it. Thank you so much for taking the time and thank you so much for you and everybody else at Huntress for what you guys do. We super appreciate it.
John: Thanks so much Jonathan.