Although IT teams and MSPs continue to ramp up their security efforts, ransomware attacks show no signs of slowing down. According to some statistics, cybercrime is expected to cost the world $10.5 trillion annually by 2025. Yes—you read that right. Ten and half trillion dollars. To put that into perspective: If cybercrime were measured as a country, then it would be one of the largest economies in the world, right behind China and the US.
Yup: We’re definitely not talking about peanuts here.
In this post, we’ll talk about some ransomware facts that forever changed today’s cyber threat landscape before diving into some 2024-2025 ransomware statistics.
NinjaOne helps MSPs and IT teams to counteract data disruption and extortion.
Learn more about NinjaOne Ransomware Recovery
How common is ransomware?
No discussion about ransomware statistics would be complete without first answering the question, “How often do ransomware attacks occur?”
The answer is simple but requires more explanation. The latest ransomware attack statistics suggest that there are 4,000 ransomware attacks per day, or around an attack every 2 seconds.
But we need to analyze the “why” of these statistics. Sure, that’s a lot of attacks to consider, but why do these statistics of ransomware still exist? Everyone and their mothers have probably heard of ransomware, but few truly appreciate how much of a threat they really are. So, here are some ransomware facts to consider.
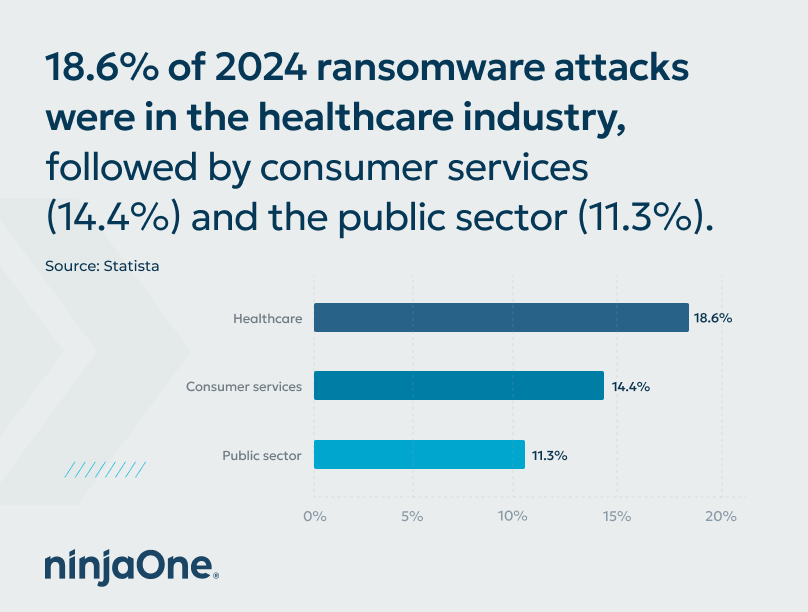
In 2023, roughly 7 in 10 reported cyberattacks worldwide were ransomware, with more than 317 million attempts recorded. And sadly, the United States remains one of the favorite targets for threat actors. In the third quarter of 2024 alone, healthcare was the most impacted industry in the US, with 18.6% of annual attacks targeting the sector.
And that’s just what’s been recorded and published online. IT experts agree that 2025 will see more cybersecurity threats to all types of organizations across all industries. So while the concept of “ransomware” may not be new, it continues to be a major threat to companies all around the world.
How did ransomware evolve?
At the center of ransomware’s evolution was a major shift away from high-volume, low-return campaigns (think mass spam and exploit kit campaigns) in favor of low-volume, high-return attacks specifically targeting businesses and organizations that a) have the funds/insurance coverage necessary to pay large ransom demands; and b) are especially sensitive to downtime (and therefore more likely to pay).
In addition, bad actors got smart. As organizations began to leverage new technologies such as AI and machine learning, so did they. Cybercriminals began researching their targets, exploiting unpatched vulnerabilities, and targetting various team members who are more susceptible to clicking on a malicious email or link (otherwise known as spear phishing).
The security company CrowdStrike dubbed this approach “big game hunting,” and it’s a model being proliferated by many active ransomware operations to this day. We discuss this further in our article about the 2024 cybersecurity statistics in the US & UK.
Let’s examine the two leading (and recent) ransomware variants that have shaped our current perspective on and design of cybersecurity strategies.
Akira
Akira ransomware was first launched in March 2023. It began gaining attention for its unique “retro aesthetic” applied to its attacks. Cybercriminals used multi-extortion tactics and hosted a TOR-based website where they posted personally identifiable information (PII) of exploited individuals and their organizations.
Victims of these attacks would then be contacted for ransom, often reaching hundreds of millions of dollars. At the start of 2024, Akira threat actors had already exploited over 250 organizations and claimed approximately $42 million in ransomware proceeds, contributing to current ransomware statistics.
Akira ransomware is so persistent that even the Cybersecurity & Infrastructure Security Agency (CISA) released special guidelines to detect, prevent, and remediate it.
BlackCat
BlackCat, also known as Noberus or ALPHV, is a special type of malware linked to DarkSide and BlackMatter, two now-defunct ransomware groups. It first appeared in 2021 but gained notoriety in 2024 because of how expansive it became. Particularly, BlackCat successfully compromised Change Healthcare and received a hefty ransom—something we discussed in detail in our IT horror stories.
BlackCat is now one of the most active forms of ransomware, and experts are attempting to catch its new variations before they can compromise other industries.
The tricky part of detecting BlackCat is that it works in numerous ways. Threat actors using BlackCat can access your environments through compromised credentials, human error, and other types of security vulnerabilities. This has also contributed to why recent ransomware statistics have exponentially increased in only a few years.
Ransomware statistics for 2023 to 2025
Ransomware attack statistics 1: The average ransomware payment
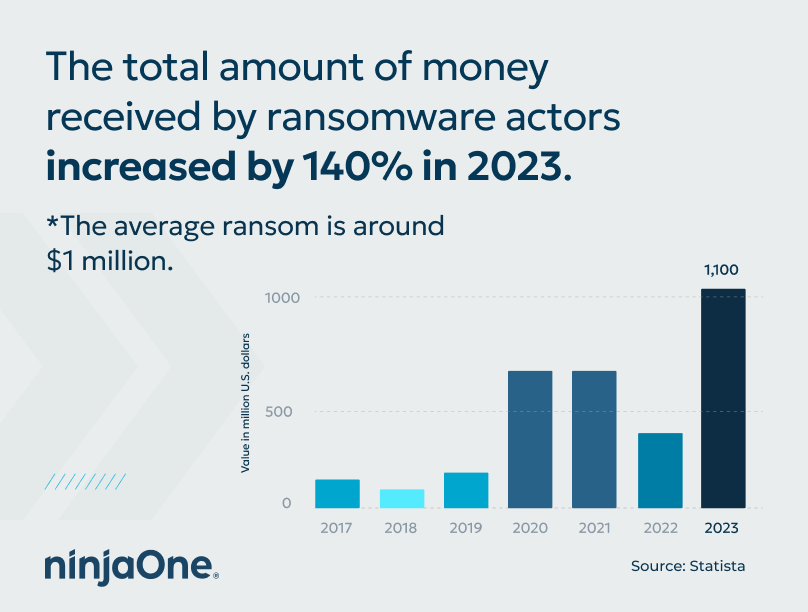
In the latest Statistica report, it was found that the total amount of money received by ransomware actors in 2023 amounted to $1.1 B, a 140% increase from the year prior.
But, recall what we mentioned in our introduction. By next year, that amount is expected to reach $10.5 TRILLION by 2025. That’s a 954,000% increase. These ransomware statistics represent a new peak in global ransomware activity, which can be partly explained by the pandemic. As more people stayed at home and were online, threat actors exploited vulnerabilities, creating a massive surge in ransomware statistics by year.
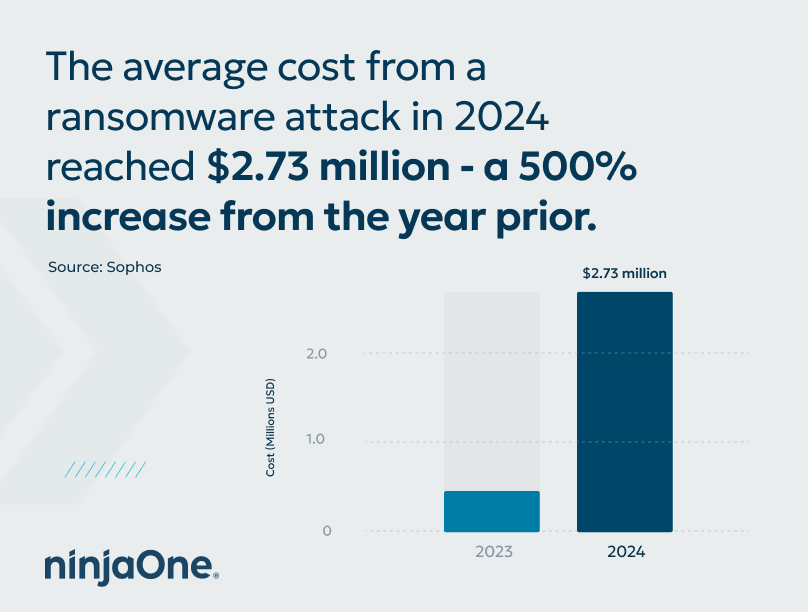
Demands from cybercriminals have likewise skewed ransomware statistics, with the average ransom being a million dollars or more (Sophos), but the average cost of recovering being $2.73 million. That translates to roughly $3 million at minimum to recover your data and once again become operational.
The amount of money being funneled back to these criminals to fund future attacks is deeply troubling. The size and quantity of ransoms being paid have led to the global cyber insurance market being worth $13 billion in 2023, almost double its estimated size back in 2020.
Why are attackers so successful at convincing organizations to pay? The primary answer is downtime.
Ransomware attack statistics 2: Average downtime
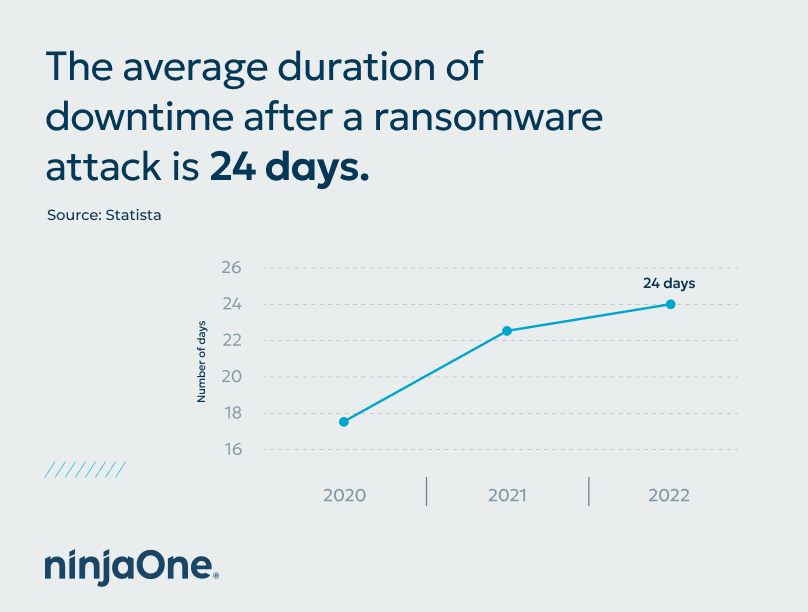
Beyond the jaw-dropping increase in ransom amounts, another extremely significant number pertaining to current ransomware attacks is 24 — that’s the average number of days US companies are experiencing infection-related downtime (according to Statistica), although some reports suggest this number is actually 21 days.)
It’s no surprise, then, that the costs associated with ransomware-related downtime are also going up.
As mentioned earlier, recent statistics of ransomware show that the global average cost of recovery from a ransomware attack in 2024 reached $2.73 million. This number includes downtime, lost revenue, and any recovery efforts. That’s a 500% increase from 2023 (Sophos).
These figures are sobering. How many businesses (especially SMBs) can afford to lose millions of dollaes and experience weeks (if not months) of downtime and disruption?
They’re also prompting organizations (and their insurance providers) to consider all options, especially when working backups aren’t available. Even when working backups are available, however, there have been cases where organizations have determined that paying the ransom and taking a chance with decryption keys is potentially less costly than the time and effort it would take to restore their systems on their own.
Other ransomware attack statistics
- More than 317 million ransomware attempts were recorded in 2024 (Statistica).
- 32% of attacks started with an unpatched vulnerability (Sophos).
- 70% of attacks resulted in data encryption (Sophos).
- 24% of companies that pay hand over the amount originally requested, and 44% report paying less than the demanded ransom (Sophos).
- 94% of organizations hit by ransomware in 2023 said cybercriminals attempted to compromise their backups (Sophos).
- Ransomware attacks on manufacturing companies have cost around $17B in downtime since 2018 (Infosecurity Magazine).
- Ransomware costs schools around $550,00 per day in downtime (Campus Technology).
- 76% spike in data theft victims named on the dark web (CrowdStrike).
- 75% of attacks were malware-free (CrowdStrike).
- 56% of organizations say that are more likely to be a target of ransomware attacks in 2024 (Ransomware.org).
- 15% of organizations say they are unprepared for multi-vector attacks (Ransomware.org).
Unfortunately, this list of ransomware statistics can go on and on, but one trend is clear: ransomware is still very much a threat today as it was before, and the threat is increasing on many fronts. Since the number of ransomware attacks and the cost for businesses is rising, IT teams need to prioritize security to protect themselves from this ever-growing threat.
Statistics of ransomware: Which businesses are targeted by ransomware?
For 2024, healthcare was the most impacted by ransomware attacks in the United States, accounting for 18.6% of annual attacks (Statistica). Consumer services followed at 14.4% and the public sector at 11.3%.
The government has taken the initiative to help these industries build more cybersecurity measures. CISA, in particular, continues to release guidelines for the healthcare and public health sector and is currently working closely with the FBI to present ransomware targeting education institutions.
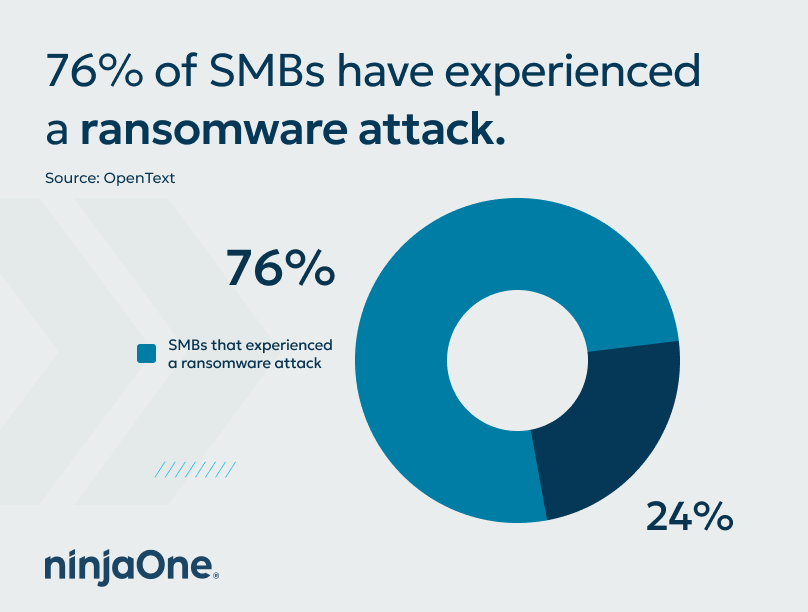
For SMBs, it truly is a matter of not “if” but “when,” with 76% of them reporting they’ve already experienced an attack in the past year alone (OpenText).
Learn how our customer, H.E.R.O.S., was able to quickly bounce back from a ransomware attack with minimal downtime and lasting damage.
“NinjaOne saved our business,” said Raffi Kajberouni, President and General Manager. “I never thought that we would be a victim of ransomware. With the support of the team lead, we were able to restore our entire computer network in four days.”
Read more NinjaOne customer stories.
Ransomware statistics and MSPs
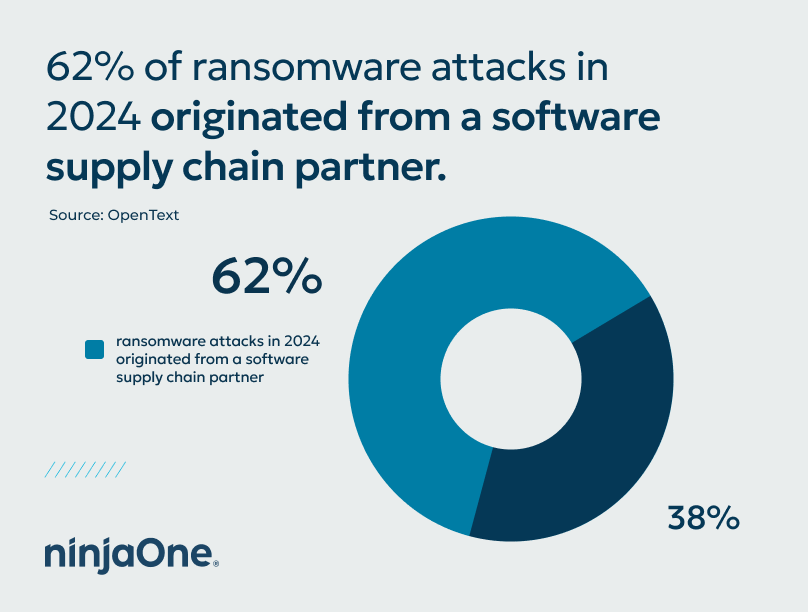
An especially concerning trend for those of us in the MSP space is the spike in attacks specifically targeting managed services providers. According to OpenText, 62% of ransomware attacks in 2024 originated from a software supply chain partner.
Additionally, 74% of organizations that experienced a ransomware attack in 2023 have a formal process for assessing the cybersecurity practices of their software suppliers. This leaves an astonishing 26% who are currently managing their cybersecurity with a “live and let die” attitude. (Pro tip: Cybersecurity experts don’t recommend this.)
We covered the trend in detail in our webinar with Huntress Labs, “How MSPs Can Survive a Coordinated Ransomware Attack” and published a free e-book, “Ransomware: The Perils of Waiting to Back up”.
The allure of compromising MSPs is obvious — doing so potentially gives attackers access to their powerful remote management tools and by extension, all of their clients. The MSP community is fighting back, however. MSPs and vendors across the space are proactively stepping up their game, calling for increased security from their peers, and are coming together to share vital threat intel.
What can you as a provider or customer of an MSP do to protect yourself?
Minimize vulnerabilities by reducing your attack surface with NinjaOne endpoint management solution.
How IT teams and MSPs can prevent ransomware attacks
The good news is that, despite these ransomware statistics and the growing maturity and sophistication of ransomware operations, the vast majority of attacks are preventable by doing five things:
- Secure RDP: Don’t expose it to the Internet! Lock it down (how-to here).
- Disable Office macros (when feasible): Same goes for OLE and DDE (here’s how)
- Enable MFA on everything: This helps prevent account takeovers and tool hijacking.
- Invest in email and DNS filtering: The goal is to protect end users by stripping out as much of the bad stuff as possible before it reaches them.
- Invest in patch management: Automate things as much as possible with a solution that can apply both Windows and third-party updates.
And of course, utilize a properly configured backup solution — and actually test recovering from backups at scale. Having multiple restore points and offsite replication is key. Remember Shrodinger’s Backup: “The condition of any backup is unknown until a restore is attempted.”
This is just the tip of the iceberg as far as defensive activities are involved, but with the vast majority of ransomware being delivered by RDP compromise and emails (typically with malicious Office documents attached), doing even just these five things will drastically reduce your risk.
How NinjaOne addresses these ransomware statistics
It helps to have an RMM and IT management solution, such as NinjaOne, that allows you to set the foundation for a strong IT security stance. With automated patch management, secure backups, and complete visibility into your IT infrastructure, NinjaOne RMM helps you prevent ransomware attacks from the start.
If you’re ready, request a free quote, sign up for a 14-day free trial, or watch a demo.