Webroot
Protect your endpoints with Webroot. Deploy, scan, and remediate threats directly in NinjaOne.
NinjaOne Webroot Integration
NinjaOne Webroot Integration Benefits
Seamless Integration
Sync organizations and devices into Webroot Global Site Manager directly from within NinjaOne – you can also use it as the single source of truth for Webroot licensing and provisioning.
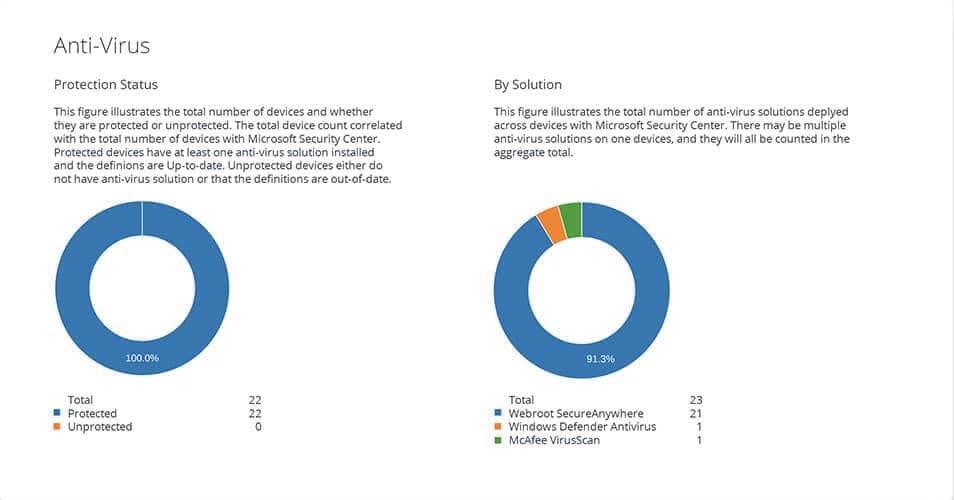
Managed Antivirus
If Webroot identifies threats, you can take remediation actions directly from the NinjaOne console.
Schedule Scans
Schedule security scans directly from the Ninja console – you can also trigger on-demand scanning for a particular device or groups of devices.
Content and URL Filtering
With 85% of malware URLs based on legitimate sites, policing the DNS layer is essential – deploy Webroot DNS Protection in just one click.
Webroot Features that You’ll Love
Endpoint Security
Best in class endpoint protection for Windows and Mac platforms. Webroot protects endpoints with 100% efficacy over a 24-hour period, as shown in independent tests by MRG Effitas.
Do-Overs are Allowed
In the unlikely event that an infected file makes it through multiple layers of protection and actually executes, Webroot allows you to roll back infected devices to a healthy state – without having to reimage the whole drive.
Ultimate Protection through Machine Learning
The Webroot Threat Intelligence Platform is a cloud-based architecture that classifies and scores 95% of the internet 3x per day.
Multi-Vector Protection
Protects against threats across email, browsers, files, URLs, ads, apps, and more, all in real time.
Sophisticated Always-on Watchdog
Uses a layered approach to global threat intelligence to continually refine classification accuracy and to protect against never-before-seen “zero-hour” threats.
DNS Protection
Detect threats at the DNS level, before they even get to endpoints – particularly useful in the “bring your own device” era, where some machines are not tied to one location.
Ready to simplify the hardest parts of IT?