The importance of patch management cannot be overstated. The critical role of patch management metrics transcends mere operational necessity – it is foundational to the evaluation and enhancement of vulnerability management programs.
In the rapidly evolving landscape of cybersecurity, the ability to measure and refine patching processes based on concrete metrics is indispensable. As cybersecurity threats grow more sophisticated and pervasive, the need to promptly and effectively address vulnerabilities through patching becomes a critical defense mechanism.
Patch management is not just about applying updates, it’s about safeguarding information and ensuring the continuity of operations in the face of constant threats.
This process is fundamental to maintaining the integrity, confidentiality, and availability of IT systems and data. The success of patch management is inherently tied to the broader discipline of vulnerability management. Effective patch management serves as a critical component of a comprehensive vulnerability management strategy, enabling organizations to proactively address vulnerabilities before they can be exploited.
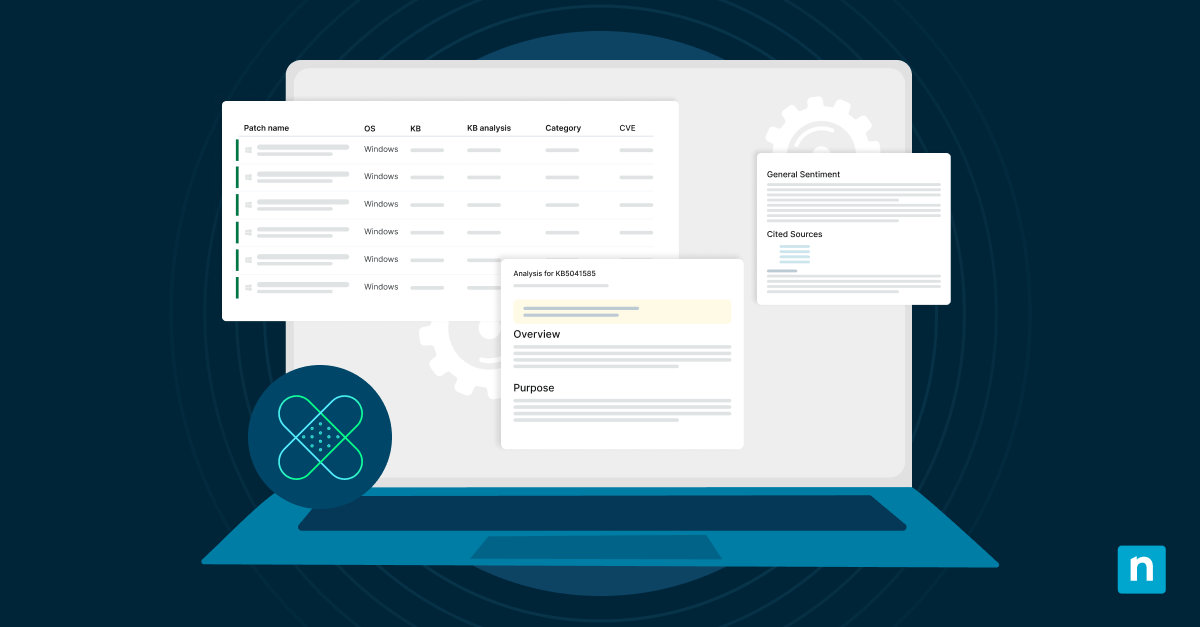
Learn more about NinjaOne Patch Management Reports that provide detailed insights for secure, efficient patching and proactive vulnerability oversight.
Patch management metrics: The need for metrics and KPIs
The establishment of specific metrics and IT Key Performance Indicators (KPIs) is essential for the success of any patch management strategy. Metrics provide a quantifiable measure of performance, allowing organizations to assess the effectiveness of their patch management processes. KPIs, in turn, offer insights into how well these processes align with the organization’s broader security objectives.
Together, these tools form the foundation upon which effective patch management strategies are built, enabling continuous improvement and adaptation to the evolving cybersecurity landscape.
10 essential patch management metrics for success
#1. Patching Cadence
- Definition and significance: Patching cadence refers to the frequency and regularity with which patches are applied within an organization. It is a critical metric for ensuring that systems remain secure and up to date. A well-defined patching cadence helps organizations keep pace with the release of new patches, minimizing the window of vulnerability.
- Importance of regularity: The strategic implementation of a regular patching cadence significantly reduces exposure to vulnerabilities. By systematically updating systems, organizations can mitigate the risks associated with outdated software and protect against potential breaches.
#2. Time to Patch
- Metric measurement: The Time to Patch metric quantifies the interval between the discovery of a vulnerability and the successful deployment of its patch. This metric is pivotal in gauging the responsiveness and agility of an organization’s patch management process.
- Significance in vulnerability management: A swift Time to Patch is indicative of an efficient vulnerability management program. It reflects an organization’s capability to quickly mitigate risks, a key factor in maintaining robust security defenses.
#3. Percentage of Systems Patched
- Measures: Proportion of systems that have been updated with the latest patches. It provides a comprehensive view of the patch coverage across an organization’s IT infrastructure.
- Relevance to vulnerability management: The Percentage of Systems Patched is crucial for assessing the thoroughness and effectiveness of patch management efforts. High coverage ensures that vulnerabilities are uniformly addressed, reducing the overall risk profile.
#4. Failed Patches
- Tracking failures: Monitoring failed patch applications is essential for identifying and rectifying issues within the patch management process. This metric sheds light on the reliability of patch deployments.
- Mitigation strategies: Addressing the causes of failed patches is vital for maintaining system security. By analyzing failures, organizations can refine their patching processes, ensuring higher success rates in future deployments.
#5. Vulnerabilities Re-patched
- Occurrence and implications: Tracking instances where vulnerabilities need to be re-patched is important for understanding the effectiveness of the initial patching effort. This metric indicates the resilience of patches and the need for continuous monitoring.
- Strategic importance: The need to re-patch vulnerabilities underscores the importance of a dynamic and adaptable patch management strategy. It highlights areas for improvement in patch testing and deployment practices.
#6. Patch Compliance Rate
- Ensuring adherence: The Patch Compliance Rate metric evaluates compliance with organizational and regulatory standards for patching. It is a key indicator of how well an organization maintains its security posture in accordance with established guidelines.
- Role in security: High compliance rates are indicative of a secure and well-managed IT environment. Ensuring patches meet compliance standards is crucial for mitigating risks and adhering to best practices.
#7. Critical Vulnerabilities Patched
- Prioritization of efforts: Focusing on the patching of critical vulnerabilities is essential for effective risk management. This metric highlights the organization’s ability to identify and address the most severe threats promptly.
- Influence on strategy: Prioritizing critical vulnerabilities informs the strategic direction of vulnerability management efforts. It ensures that resources are allocated efficiently, maximizing the impact of the patch management program.
#8. End-User Patch Compliance
- Monitoring compliance: Assessing the patching compliance of end-user devices is crucial for ensuring comprehensive security coverage. This metric reflects the success of policies and practices aimed at keeping user systems up-to-date.
- Importance of education: Educating end-users on the importance of regular patching is vital for maintaining security. Awareness initiatives can significantly enhance compliance rates, contributing to the overall resilience of the IT infrastructure.
#9. Patch Testing Success Rate
- Evaluating effectiveness: The success rate of patch testing in a controlled environment is indicative of the reliability and compatibility of patches. This metric is crucial for ensuring that patches do not adversely affect system operations.
- Ensuring quality: A high Patch Testing Success Rate minimizes the risk of disruptions, affirming the quality and efficacy of the patch management process. It underscores the importance of thorough testing before widespread deployment.
#10. Patch rollback Instances
- Frequency and causes: Measuring the instances of patch rollbacks provides insight into the stability and performance of deployed patches. This metric is essential for identifying patches that may cause issues within the IT environment.
- Continuous assessment: Tracking patch rollbacks is crucial for the ongoing evaluation and improvement of the patch management strategy. It enables organizations to quickly address and rectify issues, ensuring the continuous health of IT systems.
Incorporating metrics into a patch management strategy
The ongoing monitoring, evaluation, and refinement of patch management metrics are paramount for maintaining an effective patching strategy. Utilizing these metrics as a feedback loop, organizations can dynamically adjust their security measures in real time.
By continually assessing these metrics, organizations can identify areas for improvement, adapt their processes to meet evolving challenges, and ensure that their patch management efforts are aligned with best practices and security requirements.
Integrating patch management metrics with broader vulnerability management KPIs creates a comprehensive overview of an organization’s security posture. This integration facilitates a unified security vision that is greater than the sum of its parts, enhancing organizational agility in threat detection and response.
This holistic approach enables a more coordinated and effective response to cybersecurity threats, ensuring that patch management efforts contribute significantly to the organization’s overall security strategy.
Learn more about NinjaOne Patch Management Reports that provide detailed insights for secure, efficient patching and proactive vulnerability oversight.
Embracing patch management innovation
In the ever-changing landscape of IT security, the strategic use of these metrics is essential for staying ahead of threats and ensuring the continued protection of digital assets. By providing quantifiable insights into the effectiveness of patch management processes, these metrics enable organizations to make informed decisions, prioritize actions, and adapt strategies to mitigate risks effectively.
Take control of your patch management and enhance IT security with NinjaOne’s Patch Management software. Our solution provides quantifiable insights into the effectiveness of your patch management processes, enabling you to make informed decisions, prioritize actions, and adapt strategies to mitigate risks effectively.