Data encryption is one of the many ways IT administrators protect corporate data. In most cases, this equates to activating BitLocker and organizing it to prevent standard users from changing a BitLocker PIN or password without authorization. You can make this configuration using Group Policy Editor, Powershell, or Windows Registry.
BitLocker’s key advantage over third-party security software is its integration into the system. Setting it up and managing it is straightforward, even for individual users. For example, when BitLocker pre-boot authentication is enabled, access to the computer and its files will be restricted behind a PIN. But what if the PIN gets compromised?
Understanding BitLocker PIN and password management
A BitLocker PIN is used for pre-boot authentication. Without the correct PIN, the system will not boot or start. Meanwhile, a password prevents unauthorized access to the drive or volume even after startup. Typically, a PIN is a numerical code with at least four to twenty characters, while passwords have alphanumeric input and are much longer.
Administrators may want to restrict BitLocker password changes on Windows to enforce unified or more complex credentials across the organization. Allowing users to modify the encryption haphazardly can lead to various gaps in security. Likewise, leaving endpoint users solely responsible for regularly updating a PIN or password doesn’t guarantee compliance.
Methods to prevent standard users from changing BitLocker PIN or password
Given the importance of a PIN or password, admins may restrict users from making ill-advised changes that can weaken security levels. Organizing passwords adds an extra layer of protection, making endpoint management more consistent and easier to implement. With that said, here are three ways to prevent BitLocker PIN modification:
Method 1: Using Local Group Policy Editor (GPO)
The Group Policy Editor is a powerful tool for managing your PC’s behavior under specific scenarios. Here’s how you can use Group Policy (GPO) to turn off BitLocker PIN change for non-admin users:
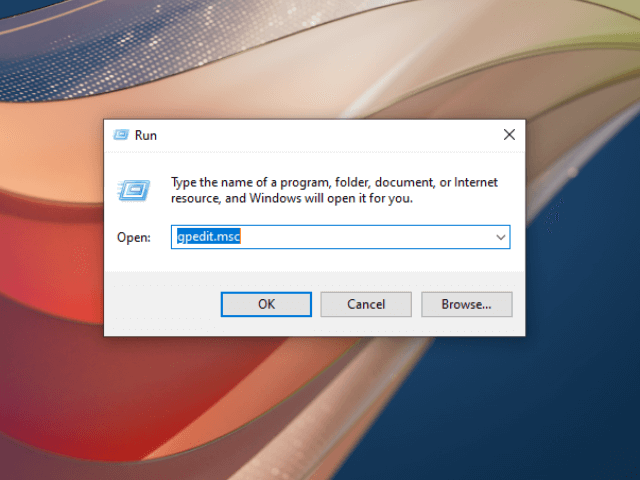
Step 1: Open the Local Group Policy Editor (as administrator):
Before we start, please note that GPO snap-in is only available in Windows 10 Pro, Enterprise, and Education editions. You can skip this method if you don’t have access to GPO.
To open the local group policy editor, press Windows + R to run the dialog box as an admin. Then, type gpedit.msc and press Enter. This action will open the editor to a new window.
Step 2: Navigate to BitLocker drive encryption settings:
From Computer Configuration, go to Administrative Templates and then Windows Components. Next, look for BitLocker Drive Encryption and click Operating System Drive. On the left panel, double-tap on Disallow standard users from changing the PIN or password policy to open its settings.
Then, choose whether to Enable or Disable this policy. Click Apply, then OK to save the changes.
Method 2: Using Command Prompt or PowerShell
Learning Powershell is useful for configuring some BitLocker settings. Here’s the command line for restricting users from changing the BitLocker PIN or Password:
Step 1: Open PowerShell as an administrator
Use Windows Search and type PowerShell. Right-click on Windows PowerShell and run as administrator.
Step 2: Disallow standard users from changing the PIN or Password
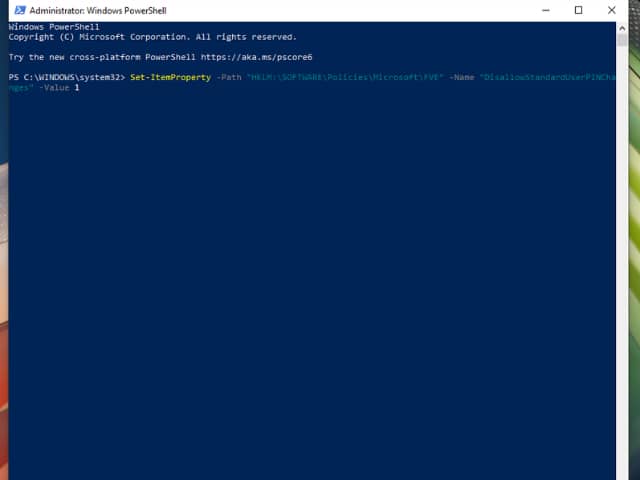
Run the following command to prevent BitLocker PIN modification for non-admin users:
Set-ItemProperty -Path “HKLM:\SOFTWARE\Policies\Microsoft\FVE” -Name “DisallowStandardUserPINChanges” -Value 1
Press Enter to execute the command to create or update a registry key to enforce the restriction.
Method 3: Using Registry Editor (advanced users)
Finally, let’s go through the steps for modifying BitLocker PIN or Password using Registry Editor:
Step 1: Open the Registry Editor
To start, press Windows + R to open the dialog box. Type regedit and press Enter.
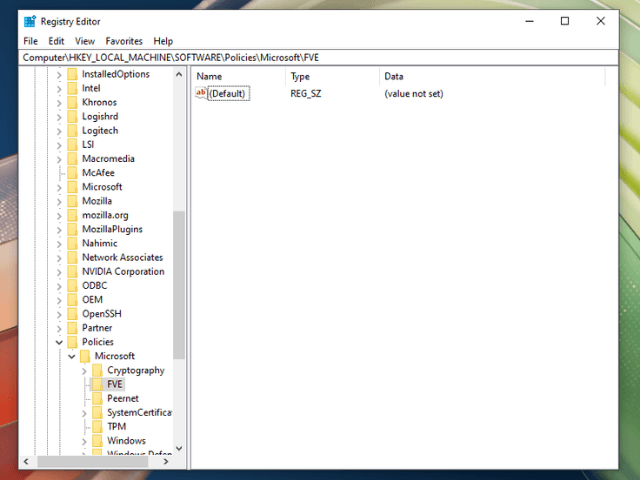
In the Registry Editor, look for the following path: HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\FVE. If there is no FVE key, you must add it manually. Right-click the Microsoft key and create a subkey named FVE.
Step 2: Add DisallowStandardUserPINReset
While selecting the FVE key, right-click a blank area in the right pane, create a DWORD (32-bit) value named DisallowStandardUserPINReset, and set its value data to 1.
Close the Registry Editor.
Before making changes, it’s advisable to back up the registry. Here’s a guide on how to back up and restore the Windows Registry.
Verifying and testing the restrictions
You can manually test if the restrictions have been applied by switching to a standard user account.
- Log in to a standard user account (non-administrator) on the same computer. To create one, go to Settings > Accounts > Family and other users > Add someone else to this PC.
- Open the Control Panel and go to BitLocker Drive Encryption.
- If the restrictions are working, the option to change the PIN should be grayed out. An error message should also be displayed when the user attempts to change the PIN.
Alternatively, you can check Event Logs to confirm the changes.
- Press Windows + R, type eventvwr, and press Enter.
- Check BitLocker events by going to Applications and Services Logs > Microsoft > Windows > BitLocker-API > Management.
- Look for event logs related to BitLocker configuration changes or access attempts.
Additionally, try to change the PIN or password as an administrator to see if the new restrictions have been applied as intended.
Troubleshooting common BitLocker PIN or password issues
If the restrictions are not working, take the following steps:
- Double-check the registry values to ensure they are correct. DisallowStandardUserPINChanges should have a value of 1.
- If you haven’t done so, restart the computer to see if the changes have been implemented.
- Open the Run dialog box again and type gpupdate /force to ensure the policy changes have been deployed.
As a precaution, you may also check if BitLocker is enabled and properly configured. Also, ensure the standard account has not been granted administrative privileges when testing the policy changes.
Additional security considerations for using BitLocker
The local group policy editor isn’t optimal if you have tens or hundreds of assets to configure. Instead, you can use Windows Group Policy in Active Directory to manage devices and policies in bulk.
Even better, you can use NinjaOne’s endpoint management software to gain complete visibility and control of your assets. A centralized solution will enable you to manage and monitor your devices and simultaneously improve security and compliance within the organization.
Enterprises need efficient monitoring policies, including alerts and reports on the overall status of devices and implementations. Hence, it’s common for large entities to unify IT management strategies using third-party software or service providers.
Raise the level of data security with automated monitoring and reporting
BitLocker is a viable option for individual users and small enterprises that need an extra layer of security for their assets. However, companies ready to scale further may find it more challenging to consistently manage and monitor BitLocker and other native data management and protection software. With this in mind, consider a more powerful centralized management solution to automate repetitive tasks, monitor encryption keys, and enforce essential network and data policies.