Photo by Bank Phrom
A rise in coordinated Ryuk ransomware attacks represents a major new threat for MSPs and their clients in 2019. Here’s what you need to know.
Ransomware was already at the top of many MSPs’ security concerns. Now attackers are deploying it more strategically, making it an even bigger threat. To understand what’s dangerous about this new trend and what you and your clients need to be doing differently to protect yourselves, let’s dig into two recent high-profile attacks deploying Ryuk Ransomware.
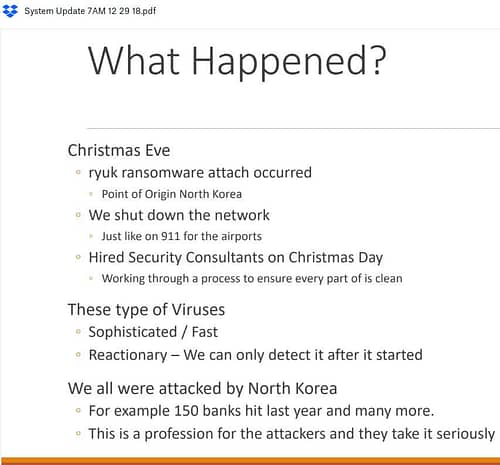
Christmas Eve ransomware infection forces MSP to shut down network
Key details:
- Victim: Data Resolution, a California-based cloud hosting and managed services provider with 30,000 clients worldwide
- Date infected: 12/24/18
- Impact: Company locked out of its own systems, forced to shut down network; clients lost access to email and databases; recovery still ongoing as of January 2
It’s the stuff of MSP and IT admin nightmares — a devastating ransomware attack on a major holiday. As first reported by Brian Krebs, for MSP and Microsoft Dynamics channel partner Data Resolution that nightmare unfortunately became a reality when on their network there arose such a clatter, admins were forced to spring from their beds on Christmas Eve to see what was the matter.
According to a status update shared with affected clients on December 29, the company explained it had been hit with Ryuk ransomware. The source of the infection was a “compromised login” which the attackers were able to successfully leverage to gain control of Data Resolution’s data center domain. As a result, the company found itself briefly locked out of its own systems and was forced to shut down the network.
Image source: Krebs on Security
In a second update delivered on New Year’s Eve, Data Resolution informed clients that their data did not appear to be compromised, but that databases needed to be cleaned before access could be restored.
Image source: Krebs on Security
According to Krebs, another update sent on January 2 informed affected clients that Data Resolution was still working to restore email access and multiple databases, as well as services for clients relying on the company to host installations of Microsoft Dynamics GP.
Security experts were less than impressed with Data Resolution’s updates, particularly the casual attribution of the attack to North Korea and comparisons to the 9/11 terrorist attacks.
Early but strong contender for worst breach notification of 2019.
– Instant attribution to North Korea
– Reference to 9/11 terrorist attacks
– Needless use of “sophisticated”
– Claiming detection wasn’t possible
– Reference other victims to note defense is hard https://t.co/vjFrFPKkRs— Robert M. Lee (@RobertMLee) January 3, 2019
Experts also questioned how the company could be realistically confident that no customer data had been compromised. To be fair, it’s become commonplace for breach victims to hastily declare “no customer data compromised” before such a claim can be realistically verified, so Data Resolutions isn’t alone there. As we’ll see, however, the fact that the ransomware involved in this incident was Ryuk makes that claim especially dubious.
If Ryuk sounds familiar, it’s because it’s the same strain of ransomware implicated in another high-profile incident making headlines this week.
Major newspapers across U.S. also disrupted by Ryuk
Key details:
- Victim: Tribune Publishing
- Date infected: 12/27/18
- Impact: Distribution for weekend editions of LA Times, San Diego Union-Tribune, Wall Street Journal, New York Times, and other papers disrupted
Two days following Data Resolution’s nightmare before Christmas, editors at the San Diego Union-Tribune discovered they weren’t able to successfully transmit pages to the newspaper’s printing facility. The full extent of the problem was uncovered on Saturday, December 29, when it was revealed that Tribune Publishing’s network had been infected with malware.
Because Tribune Publishing shares printing and operations systems with a variety of newspapers, the infection disrupted distribution of the Los Angeles Times, the San Diego Union-Tribune, papers in Florida, Chicago, and Connecticut, as well as the West Coast editions of the Wall Street Journal and the New York Times.
The malware was later identified as Ryuk ransomware, which has been actively infecting various targets since last August.
What is Ryuk ransomware?
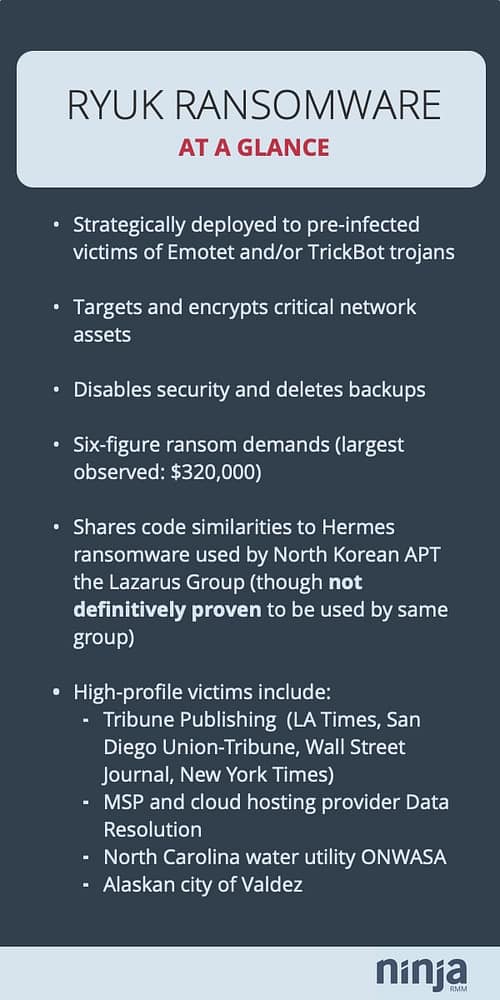
Ryuk is a strain of ransomware used in targeted attacks. High-profile victims of the ransomware include Tribune Publishing, cloud hosting provider Data Resolution, North Carolina water utility ONWASA, and the city of Valdez, Alaska. Deployment of the ransomware is manual and strategic. It is typically preceded by malware infections involving the Emotet and/or TrickBot trojans, which lay the groundwork for network-wide compromise and the encryption of critical network assets. As a result, Ryuk infections can be incredibly disruptive. Ransom demands have often been in the six-figures.
What makes Ryuk ransomware attacks different?
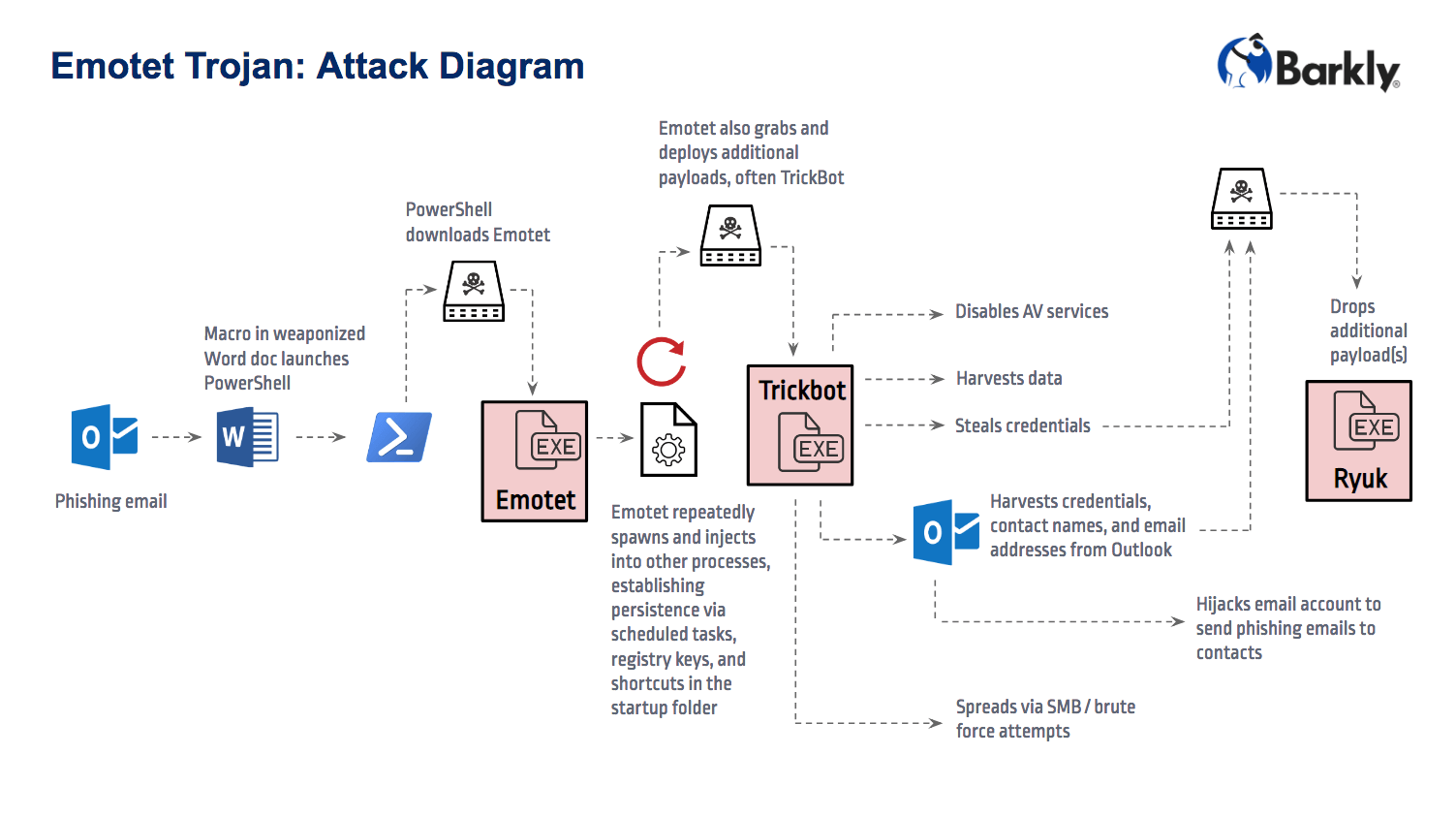
Ryuk stands out from other ransomware in several key ways. First, unlike the majority of variants delivered during ransomware’s 2016-2017 heyday, Ryuk is not deployed via large, indiscriminate spam campaigns. Instead, it appears to be being selectively deployed to organizations that have been previously infected with Emotet and/or TrickBot.
I can confirm the deployment of #Ryuk #ransomware on high-value targets through #Emotet loader -> #TrickBot as well; this is the only confirmed initial attack vector I can vouchhttps://t.co/BGw37EByfO
— Vitali Kremez (@VK_Intel) January 1, 2019
Emotet and TrickBot were two of the most active trojans of 2018, responsible for disrupting scores of victim networks with infections that are notoriously difficult to contain and remove. The two often arrive in tandem, with Emotet arriving via malicious email attachments and establishing an initial foothold on the system before downloading TrickBot, which then quickly goes to work spreading itself throughout the victim’s network.
Despite infections reaching epidemic proportions, causing US-CERT to issue an alert calling Emotet “among the most costly and destructive malware,” Emotet and TrickBot have failed to garner the same mainstream attention that ransomware receives. Now that victims infected with the trojans are getting hit with Ryuk that may be about to change.
While details concerning the Data Resolution and Tribune Publishing infections are still scarce, two attacks that occurred last year offer a more complete picture of the Emotet –> TrickBot –> Ryuk infection cycle.
Image source: Barkly
The first is a Ryuk ransomware attack on North Carolina water utility ONWASA, which made national news thanks in part to the fact that the county the utility served was still actively recovering from Hurricane Florence. That timing combined with Ryuk’s similarities to Hermes, a ransomware strain used by North Korean APT the Lazarus Group, caused ONWASA CEO Jeffrey Hudson to characterize the infection as a targeted attack designed to conduct maximum damage in the wake of a natural disaster.
What many news outlets failed to report, however, was that ONWASA had identified an Emotet infection nine days prior to Ryuk appearing. In fact, the deployment of the ransomware appeared to be triggered by attempts to remove and remediate the original infection.
Similar scenarios played themselves out in the Alaskan towns of Matanuska-Susitna (Mat-Su) and Valdez (you can read a detailed report from Mat-Su’s IT Director documenting that incident here). While the ransomware in both cases was initially identified as Bitpaymer, it was later clarified that Valdez had been infected with Ryuk. In that case, the city acknowledged paying a ransom of nearly $2customer-count to recover access to their systems.
Compared to other Ryuk victims, Valdez appears to have gotten a deal. As Check Point researchers note, the typical Ryuk ransom demand can be six figures, with the largest observed amount being $320,000. Even more disturbing, victims are actually paying. Several Bitcoin wallets used by the attackers have over 50 Bitcoins ($188,000) in them, each (example here and here). The total extorted is estimated to be north of $640,000.
Key takeaways for MSPs and clients
1) Ransomware may indicate you have an even bigger problem
Ransomware is the three-alarm fire of malware. It presents an immediate, tangible problem and typically sends responders scrambling into action. But Ryuk’s deployment to Emotet/TrickBot-infected machines underscores how important it is to treat other, sneakier types of malware infections seriously. Not only can they install backdoors and lay the groundwork for more actively damaging attacks, they can also silently siphon off sensitive information.
Yep. Both Emotet and Trickbot have *huge* reach inside western organisations with ongoing infected PCs inside firewall boundaries. Orgs have traditionally not given much focus to why PCs got infected, just relying on AV to remediate low level threats. May backfire. https://t.co/EAumlzLjWW
— Kevin Beaumont ON A BREAK (@GossiTheDog) January 2, 2019
Data Resolution may be quick to say Ryuk didn’t compromise customer data, but if Emotet or TrickBot did in fact precede the ransomware that claim becomes much more dubious. Both trojans have extensive credential harvesting capabilities, and Emotet is capable of exfiltrating 180-days worth of sent/received emails. The trojans have also been known to actively hijack victim email accounts in order to send more malware-laden spam emails to the victim’s contacts.
2) Don’t ignore early warning signs
The good news is, despite what the Data Resolution notice said, infections can be detected before ransomware actively comes into play. Warning signs can include suspicious account log-in attempts and lockouts, unusual registry modifications and scheduled task creation, and more. You can find a list of specific things to look out for associated with Emotet infections, specifically, here.
3) Antivirus and backup may not always be enough
AV and backup are both core components companies should be utilizing to protect themselves, but they’re not silver bullets. TrickBot and Ryuk are both capable of scanning for and disabling a variety of AVs. To combat that threat, you should ensure you’re utilizing tools that provide you with crisp visibility into your clients’ networks, and can inform you with alerts when suspicious activity is underway like RMM software.
As part of its strategic deployment, the attackers behind Ryuk also often make it a point to seek out and delete accessible backups, too. That means it’s important to ensure not only that you have backups, but that you have copies that are isolated.
4) This is a chance to help your clients get more proactive
If you have clients who feel satisfied that they’re fully protected from ransomware simply following the basics, this is a good opportunity to remind them that attack techniques are constantly evolving. There’s a lot they can accomplish by hardening their systems against the latest malware like Emotet, TrickBot, Ryuk, and others. That can involve anything from helping them configure their Active Directory more securely to making sure they have RDP secured to adjusting their Microsoft Office settings to disarm malicious Office docs.
Not only can you position yourself as more of a security expert and mentor, you can also cut down on the probability of you getting a frantic call for help.
5) Revisit your own security and incident response plan
Ryuk isn’t just a threat to your clients. Consider what happened to Data Resolution a cautionary tale and take this opportunity to reevaluate things on your end, as well. Are you as locked down as you should be? Do you have a clear disaster recovery / incident response plan? If so, when’s the last time you reviewed it? Does it include a clear checklist for notifying and responding to clients?
When malware hits things can unravel in a hurry. Make sure you’re ready for the worst.