The U.S. Department of Education, in coordination with the Cybersecurity and Infrastructure Security Agency (CISA), recently launched the Government Coordinating Council (GCC) to strengthen cybersecurity across all K-12 educational institutions in the United States. This comes as the U.S. Government Accountability Office (GAO) warned of the alarming rise in K-12 cyberattacks, particularly in phishing emails, ransomware, distributed denial-of-service attacks, and video conferencing disruptions.
It is clear that cybersecurity for schools has become increasingly important in the modern space. While most of us would not equate “cybersecurity” with “education”, the truth remains that threat actors are progressively disrupting our educational system for various reasons.
As highlighted by U.S. Secretary of Education Miguel Cardona in a 2023 press conference, “Just as we expect everyone in a school system to plan and prepare for physical risks, we must now also ensure everyone helps plan and prepare for digital risks in our schools and classrooms.”
Preventing K-12 cyberattacks
Since the 2020 pandemic, K-12 schools and school districts have increasingly adopted remote networking technologies to facilitate learning and make schools more efficient. Despite the numerous benefits of this technological gain, it has also introduced new risks in cybersecurity, especially with how students learn and receive data.
Government institutions, such as the National Institute of Standards and Technology (NIST) and CISA, have made efforts to improve K-12 cybersecurity nationwide, whether by creating a National K-12 Cybersecurity Education Roadmap or an ongoing educational initiative to safeguard K-12 organizations from cybersecurity threats.
The White House also signed the K-12 Cybersecurity Act into law in 2021 as a firm stance against the continuing threats posed by malicious actors in the educational system.
Some ways you can prevent cyberattacks in your school
- Develop a strong cybersecurity plan
CISA encourages education leaders to develop a strong cybersecurity plan that is both cost-effective and practical. While each school is different, some important aspects to consider include deploying online security strategies, such as 2FA, mitigating known exploited vulnerabilities, and creating a disaster recovery plan, which may involve working with a vendor that offers backup for ransomware recovery.
If you’re unsure where to start or what to include in your plan, refer to CISA’s Cybersecurity Performance Goals (CPGs) for more information.
- Regular cybersecurity training
Teachers, students, and their parents (whenever possible) must attend regular cybersecurity training. These trainings need not be overly long or complicated. You can focus on preventative strategies, such as building a culture of security, knowing the common cyber attacks, and developing other healthy cybersecurity habits.
- Work with your existing resources
Some K-12 schools have limited resources—and that’s perfectly okay. Nevertheless, this should not be a reason to disregard your cybersecurity. There are some ways to reduce your IT costs, from partnering with a trusted IT management provider to working with a state-planning committee and being a part of the State and Local Cybersecurity Grant Program.
- Collaborate with other educational institutions
If possible, try to leverage your relationships with other K-12 entities, the MS-ISAC, or K12 SIX, to share resources and help your school prevent and respond to cyber threats more effectively.
Why is K-12 cybersecurity important?
As with any business that needs to protect their networks, devices, and sensitive information from criminal use, schools must proactively safeguard themselves to protect their student privacy, improve school safety, and minimize risks of organizational impact.
With technology steadily permeating every facet of life, cybersecurity can no longer be divorced from traditional safety strategies usually implemented in educational institutions. Schools must take a more holistic approach to keeping children safe, whether that’s their physical safety, online safety, or data safety.
Key takeaways:
- Threat actors are gradually targeting K-12 education organizations.
- These cyberattacks can have a catastrophic impact on students, particularly their online safety.
- Nationwide efforts are being made, but they could still improve.
- Everyone can help in improving cybersecurity in schools.
To better understand the degree to which educators and students are exposed to cybersecurity threats, NinjaOne surveyed 500 educators across various types of schools, including public and private K-12 schools and public and private universities. The survey was conducted on August 28, 2020, with PollFish.

Now is the time for school IT leaders and MSPs that service education clients to take stock of challenges and work hard to institutionalize changes so schools are ready for a digital world.
“As school districts, teachers, parents, and students have no doubt thought endlessly about how this school year will actually play-out, there is potentially one area that has not received enough consideration,” said NinjaOne Chief Security Officer Lewis Huynh. “The average consumer household, with arguably the weakest levels of cyber-security protection, has now collectively become the largest attack surface available to hackers. This makes it extremely critical that IT, Security, and Networking Teams work together on remote connectivity solutions that focus on a trifecta of usability, performance, and protection.”
A Mixed Approach To Device Management And Security
Devices Used Daily
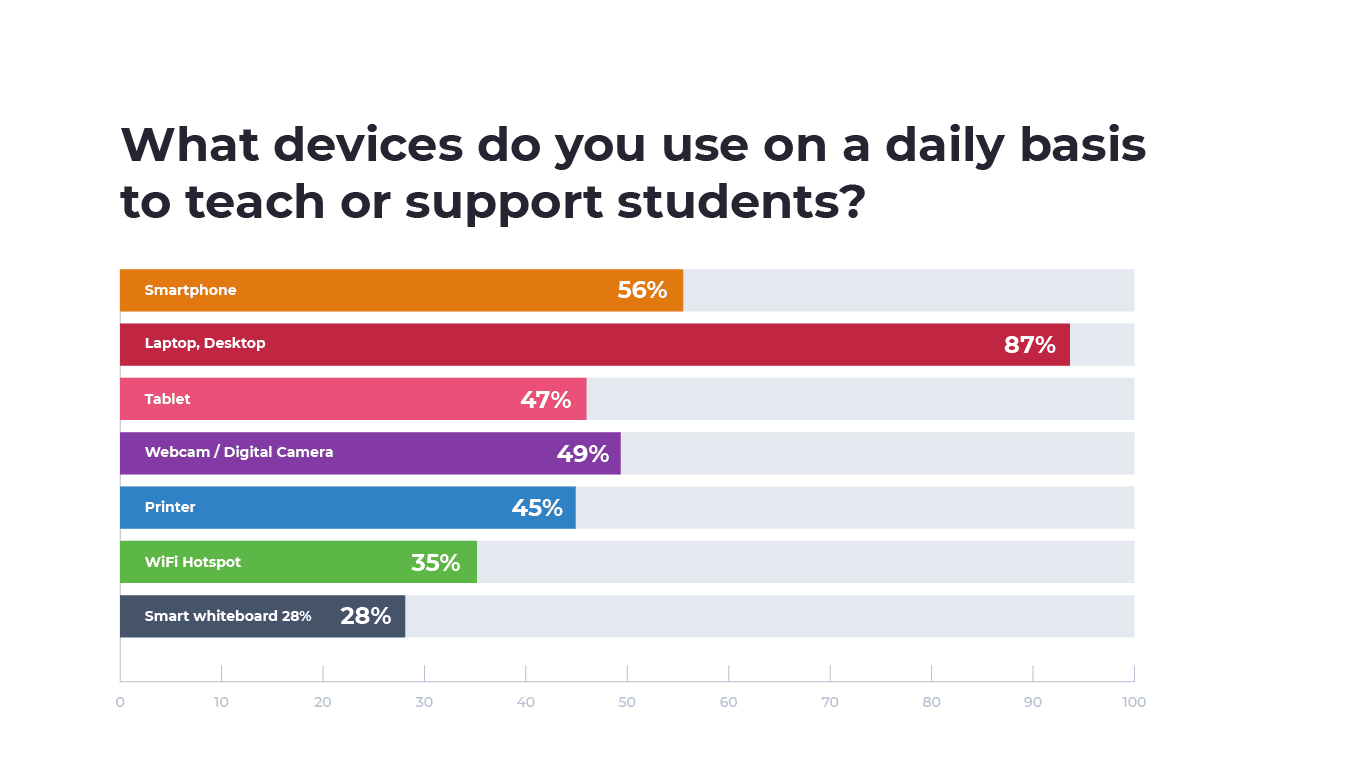
As expected in a remote learning world, mobile devices like laptops, smartphones, and tablets are among the most used devices by educators daily. 56% of educators used smartphones on a daily basis. 56% of educators used smartphones on a daily basis, while 47% used tablets. Perhaps unsurprisingly, 87% of educators were using a laptop or desktop. This finding mirrors recent trends in the increased use of smartphones and tablets in the classroom to enhance lessons and an abundance of apps geared toward educators.

Printers and webcams also ranked highly among remote devices used by educators. These innocuous-seeming devices contain their own risks, such as spyware to record private conversations or steal personally identifiable information from scanned and printed documents.
Security Disparities Between Educators Using Own Devices
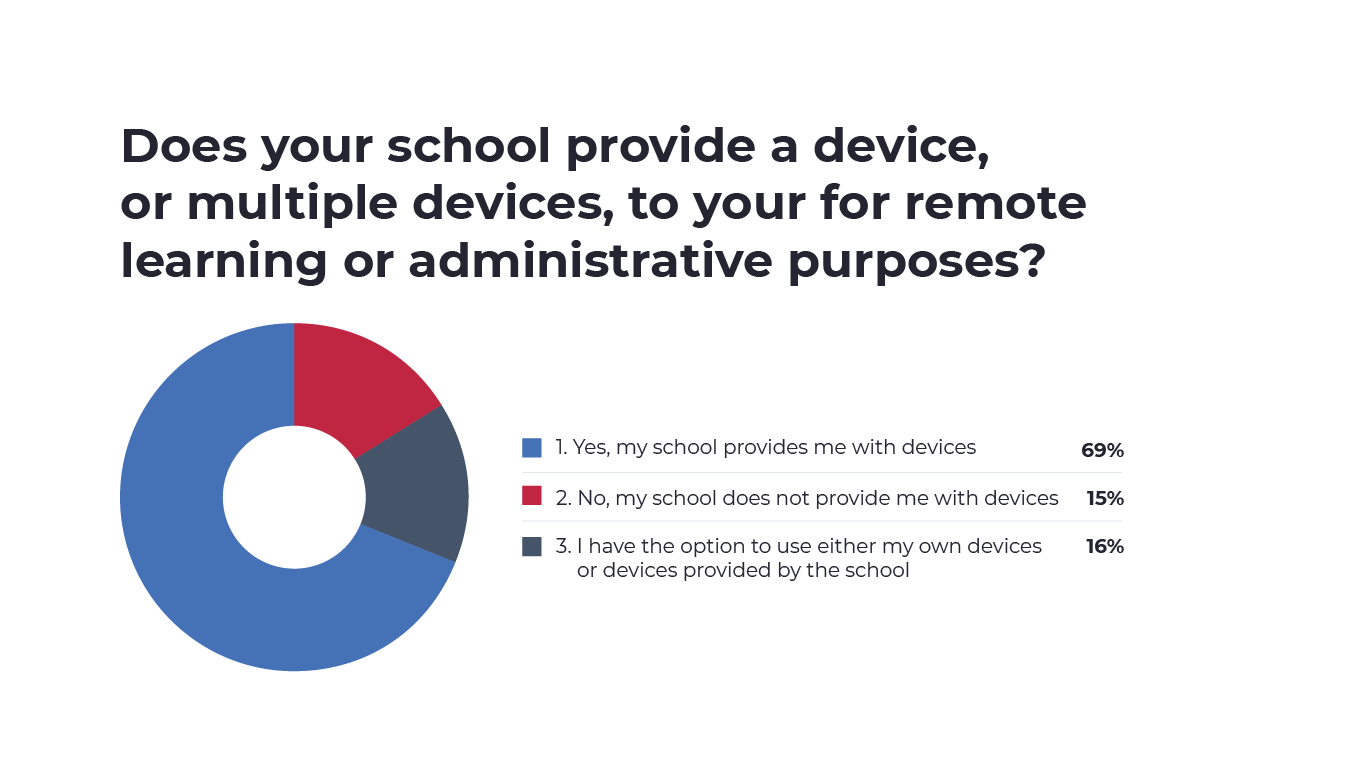
Many educators use their own devices to teach, adding more complexity to the issue. Our survey found that 15% of educators’ schools don’t provide them with devices, while 16% are allowed to use either their own devices or those provided by the school. However, 69% of educators surveyed reported their school did provide them with devices. A BYOD approach introduces additional complexity by raising the risk of a cyberattack or breach, most commonly through phishing attempts.
Key takeaways:
- More K-12 schools are implementing, or are strongly considering, remote classes.
- Mobile devices, such as laptops and smartphones, are progressively being used by students and teachers.
- Most teachers use their own personal devices, increasing their cyberattack risk.
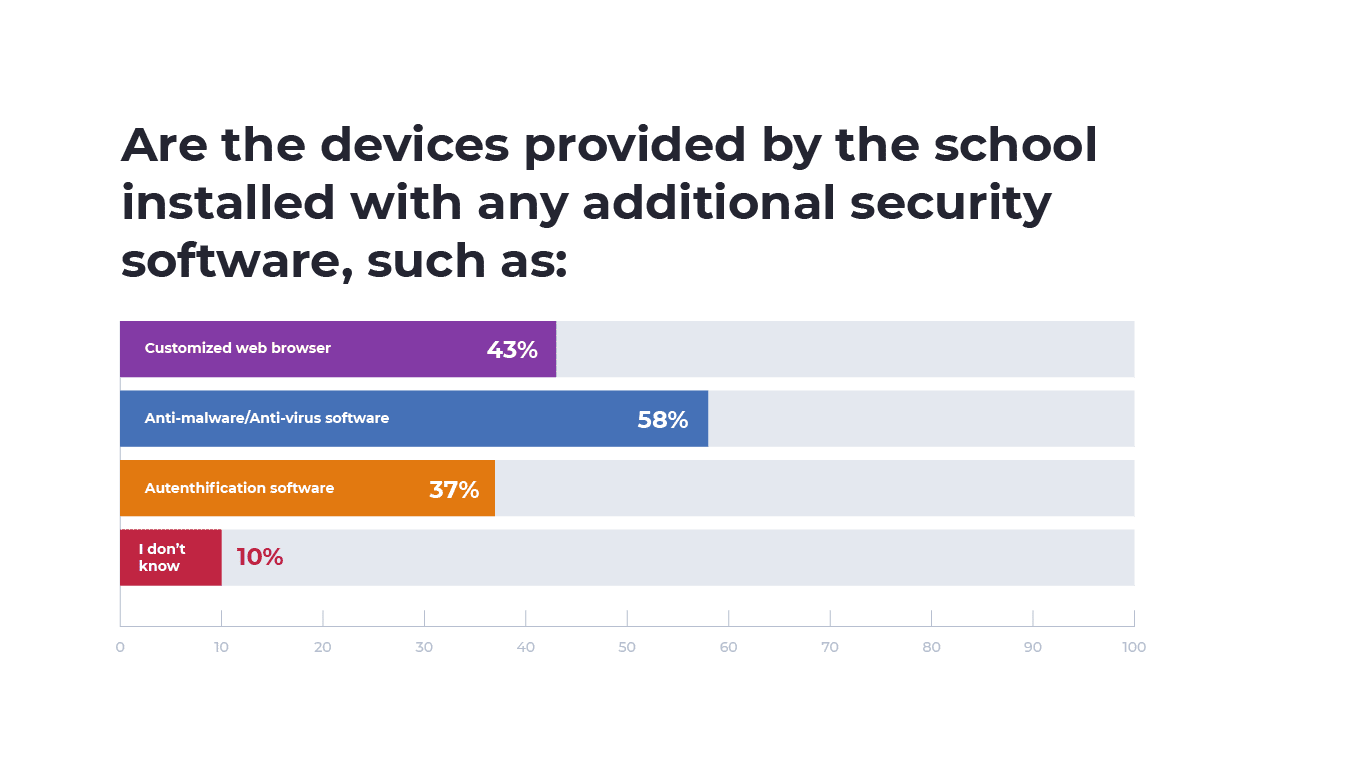
Among those using devices provided by their school, 58% indicated their devices are installed with anti-malware or anti-virus software. Additionally, 43% had a customized web browser installed on their device and 37% indicated they had authentication software installed on their devices. Only 10% didn’t know whether the devices provided by their school contained additional security software.
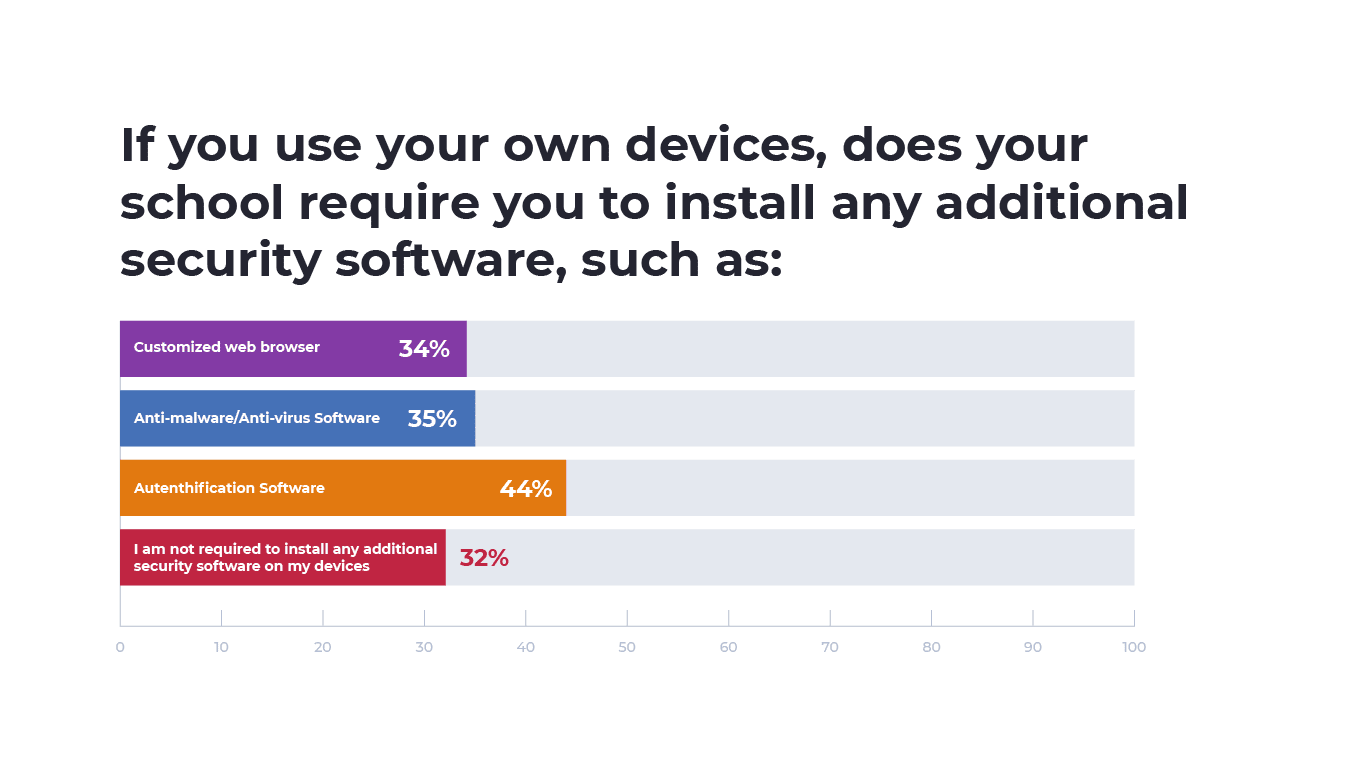
The numbers told a different story for educators using their own devices. 32% of educators who used their devices were not required to install any additional security software. Of the 65% of respondents that were required to install additional security software, 35% installed anti-virus or anti-malware software.
“The lack of authentication protocols on school devices is a liability that multiplies with every additional device connected to the network,” said Coveware CEO Bill Seigel. “Re-used or weak passwords are an ‘oldie, but goodie’ for cybercriminals looking to gain access to a network, and authentication layers, like multi-factor, are the antidote. This will end badly for schools it is just a question of who gets hit, and when.”
Most Network Connections Meeting Industry Standards
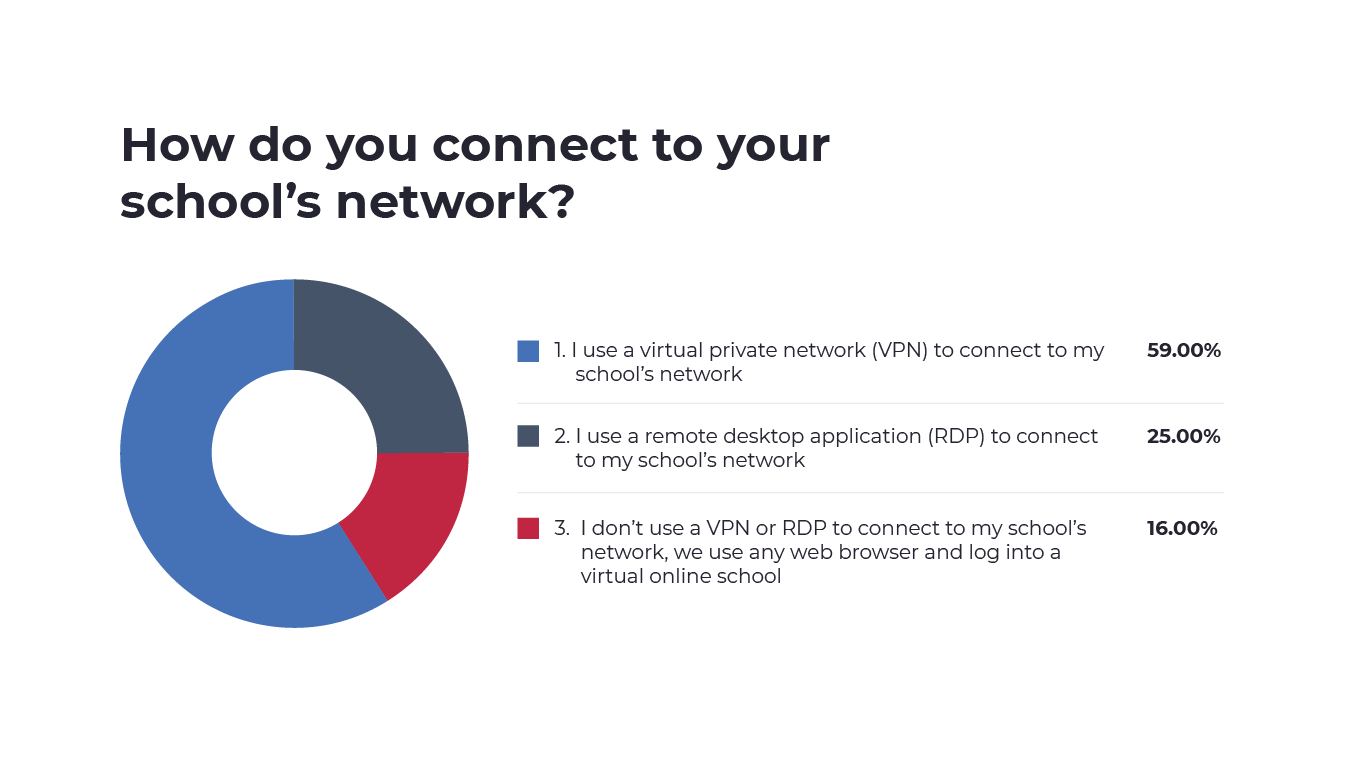
When asked how they connect to their school’s network, 59% of educators reported using a VPN. 25% of respondents used an RDP connection and 16% used neither a VPN nor RDP but instead signed into a virtual school through any browser.
It is concerning that some educators accessing private student data aren’t using a secure connection. This poses a significant security gap that should be at the top of any list of security priorities. Ultimately, the security of connections via VPN or RDP depends on the vendors offering the service. For this reason, IT leaders should carefully analyze the security standards of every vendor they partner with.
Cybersecurity Training Represents Opportunity For Improvement
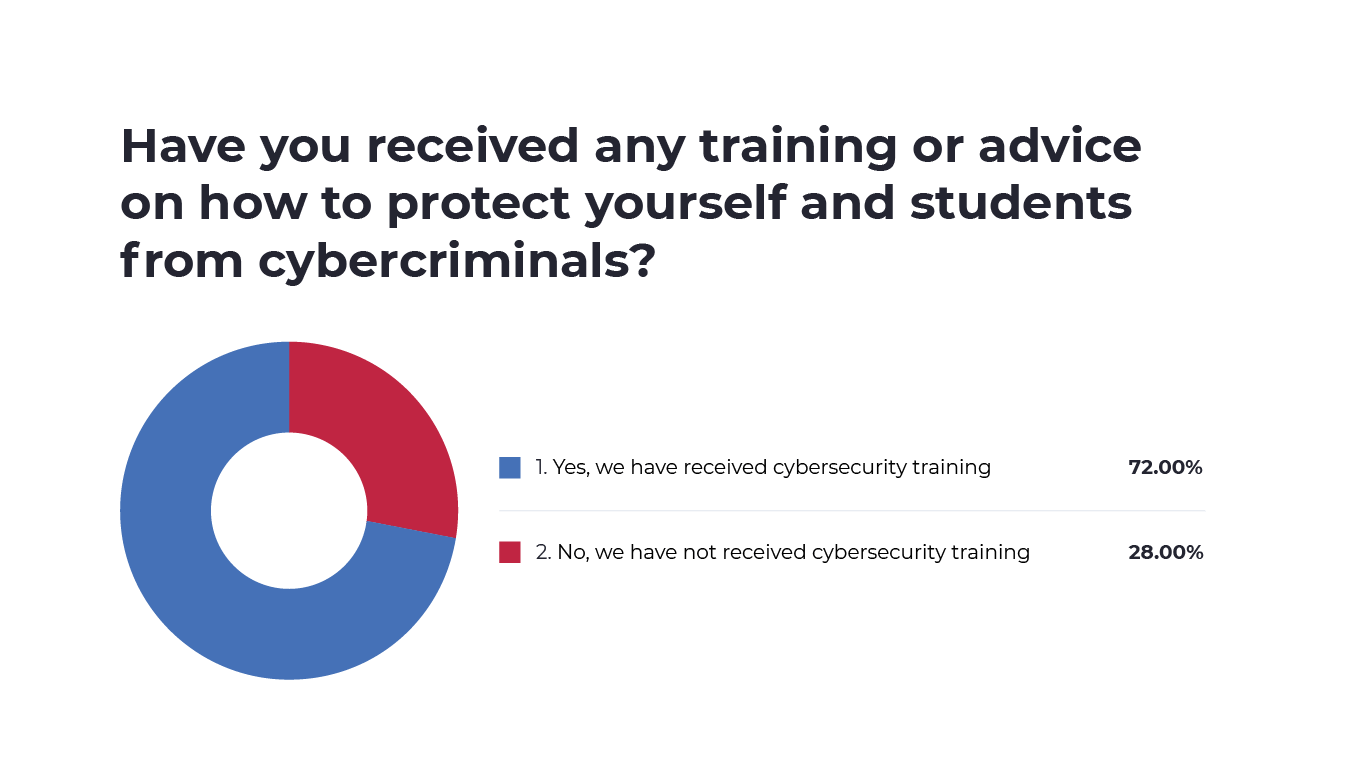
Almost three-quarters of educators surveyed reported having undergone some kind of cybersecurity training. However, 28% had not received cybersecurity training. Routine cybersecurity training is a highly recommended practice that allows leaders to communicate priorities, answer questions and proactively mitigate threats like phishing.
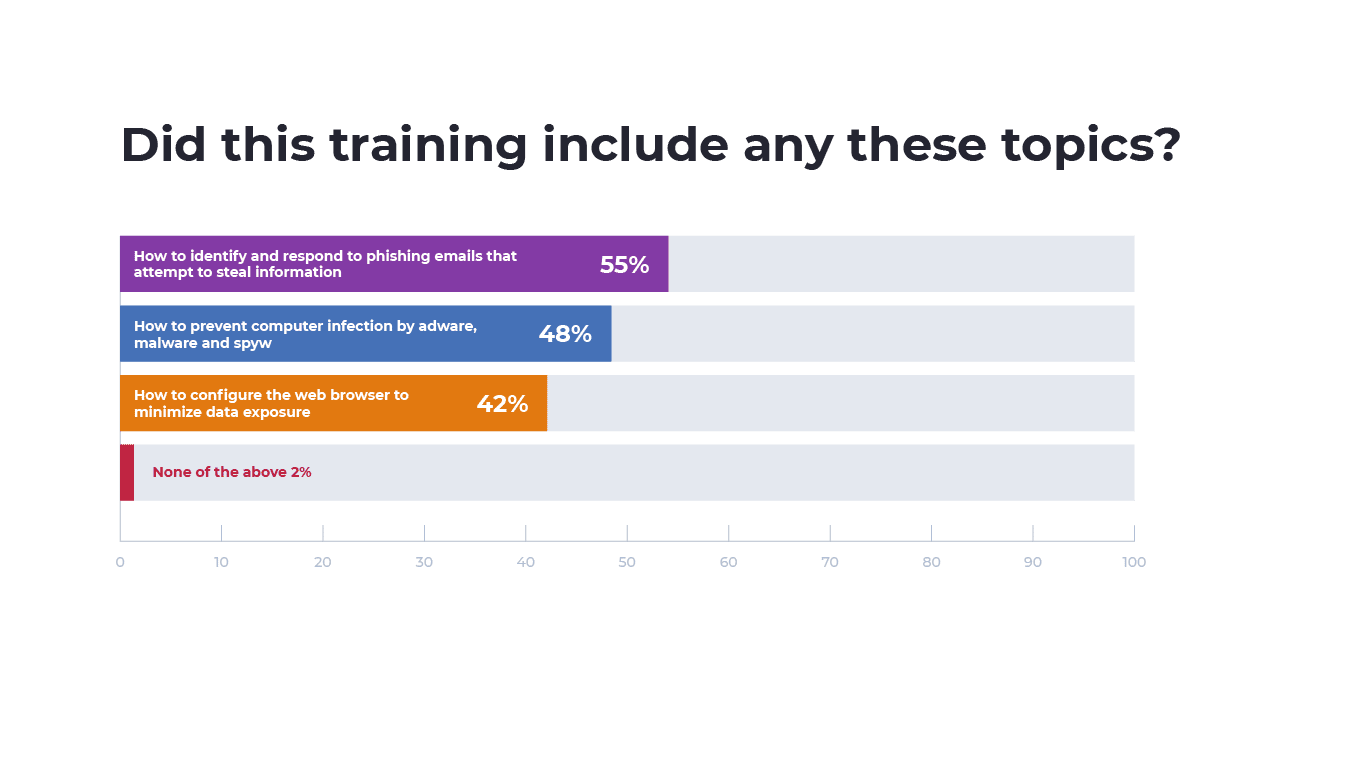
Among those that did receive cybersecurity training, 55% were taught how to identify and respond to suspected phishing attempts, 48% were taught how to prevent computer infection by adware, malware and spyware, and 41% were taught how to configure their web browser to minimize data exposure. Only 2% of respondents did not receive training in any of the scenarios.
Based on these findings, security lapses among educators using their own devices could expose schools to new threats and raise the likelihood of data theft. School IT leaders and MSPs working with clients in this sector should ensure all educators have a unified security policy that covers foundational elements such as anti-virus and multi-factor authentication to access devices and applications educators use.
Key takeaways:
- Many teachers don’t install additional anti-virus software on their devices.
- There is an evident lack of cybersecurity training or protocols among teachers.
- Existing cybersecurity training could be further improved and deemed mandatory for all education professionals.
Student Device Management Practices Similar To Educators
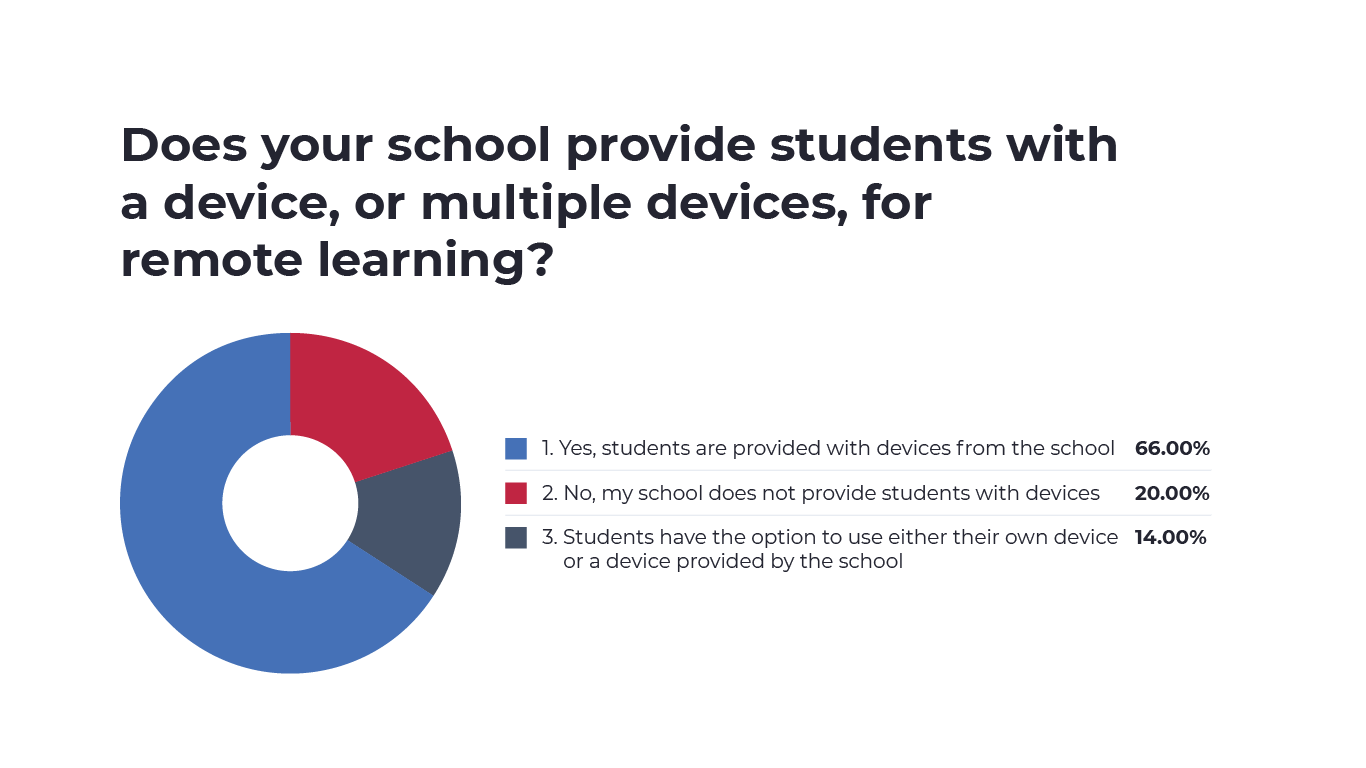
Looking at how schools manage devices among students, we found that 66% of students were supplied with devices by the school, but 20% were not provided with devices, and 14% had the option to use either their own devices or devices provided by the school.
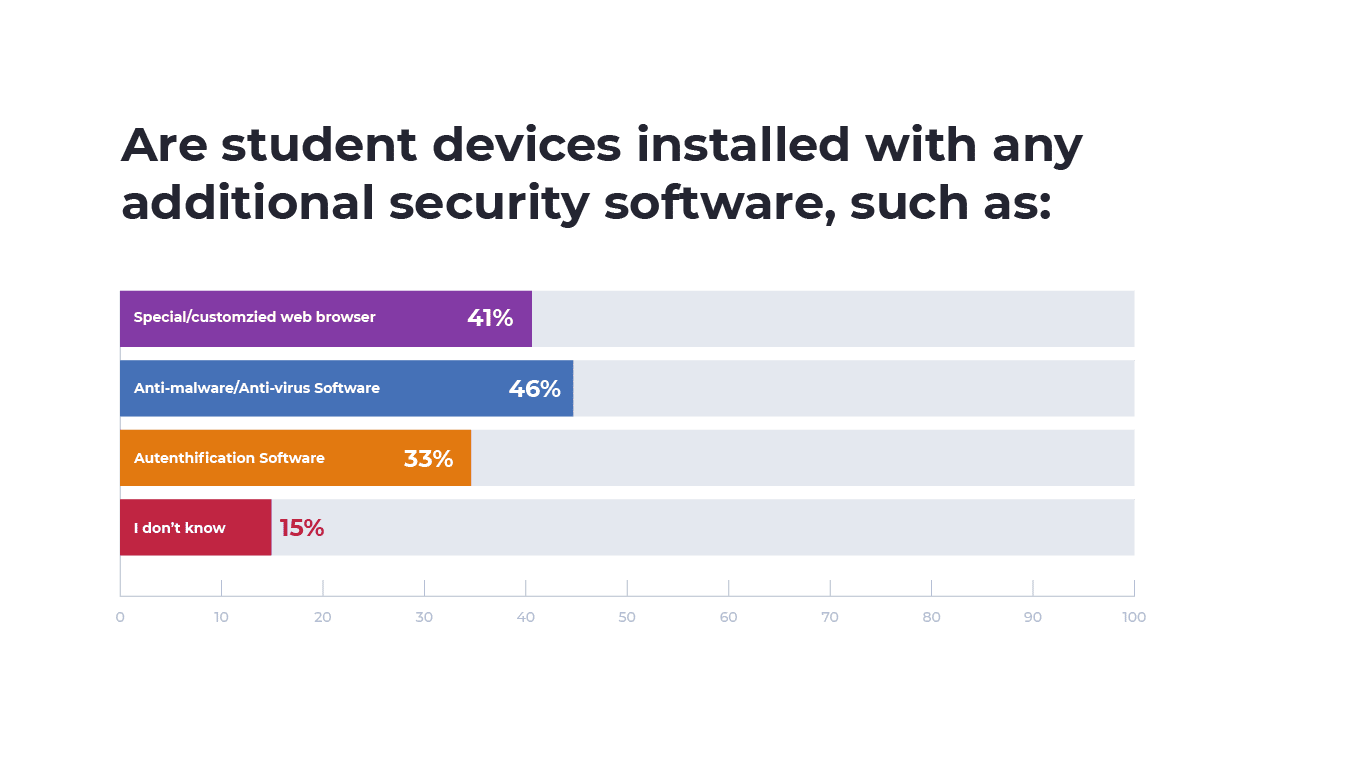
For students who were supplied with devices, 46% of respondents indicated that student devices were installed with anti-malware or antivirus software, 41% of school-supplied devices were installed with a customized browser to limit data leakage, and 35% of devices were installed with authentication software.
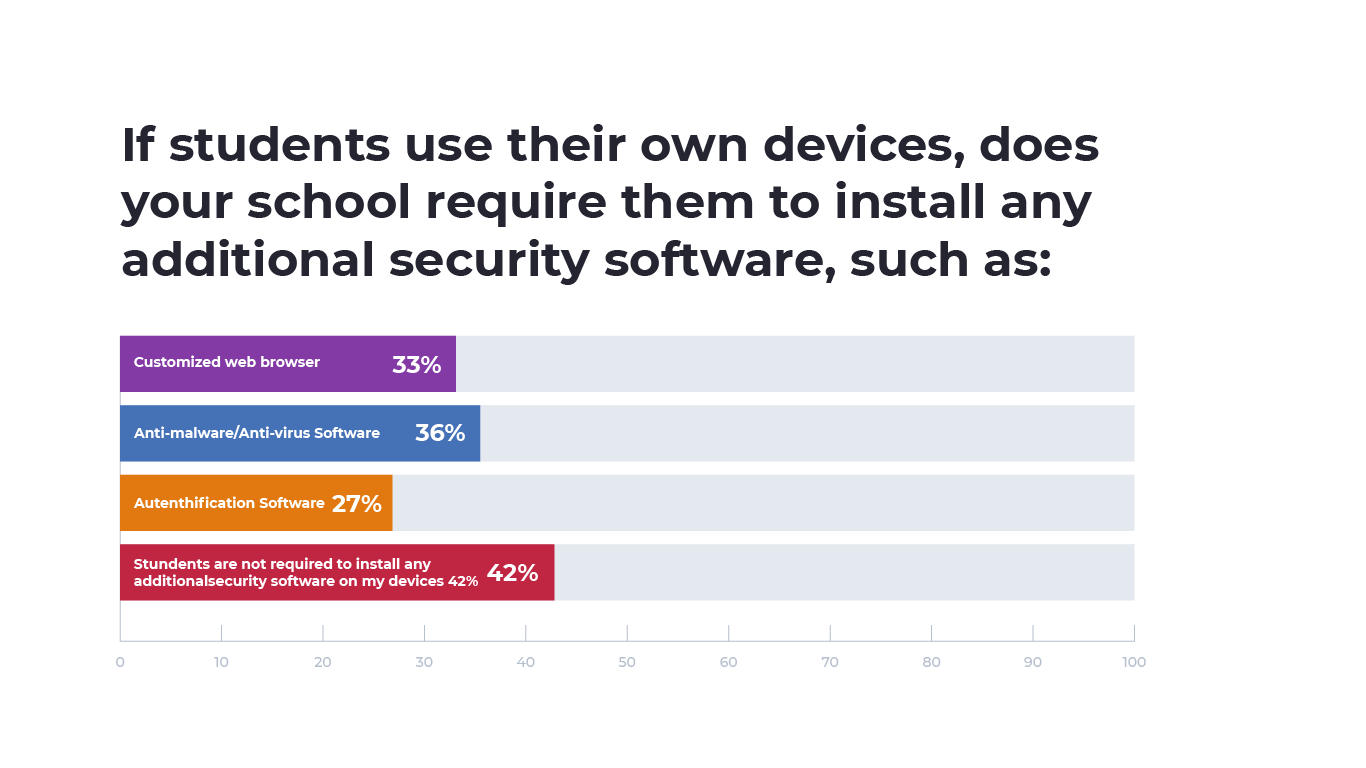
However, for students using their own devices, 42% of respondents indicated that students weren’t required to install any additional security software. Among students who were required to install additional security software on their devices, 36% of respondents indicated students’ personal devices had to be installed with anti-malware or antivirus software, 33% had to install a custom web browser and 27% had to install authentication software.
Overall, student device management and security echoed that of educators. When devices were provided by the school, educators and students were more likely to have basic security software installed on their devices. But for both groups, those that used their own devices had much lower rates of additional security software installed on their devices and many weren’t required to install any additional security software.
With nearly a third of students potentially using their own devices to connect to their school’s network, school IT leaders must prioritize remote endpoint security to protect school networks and student data.
ChromeOS Tops List of Most Used Operating System On School Devices
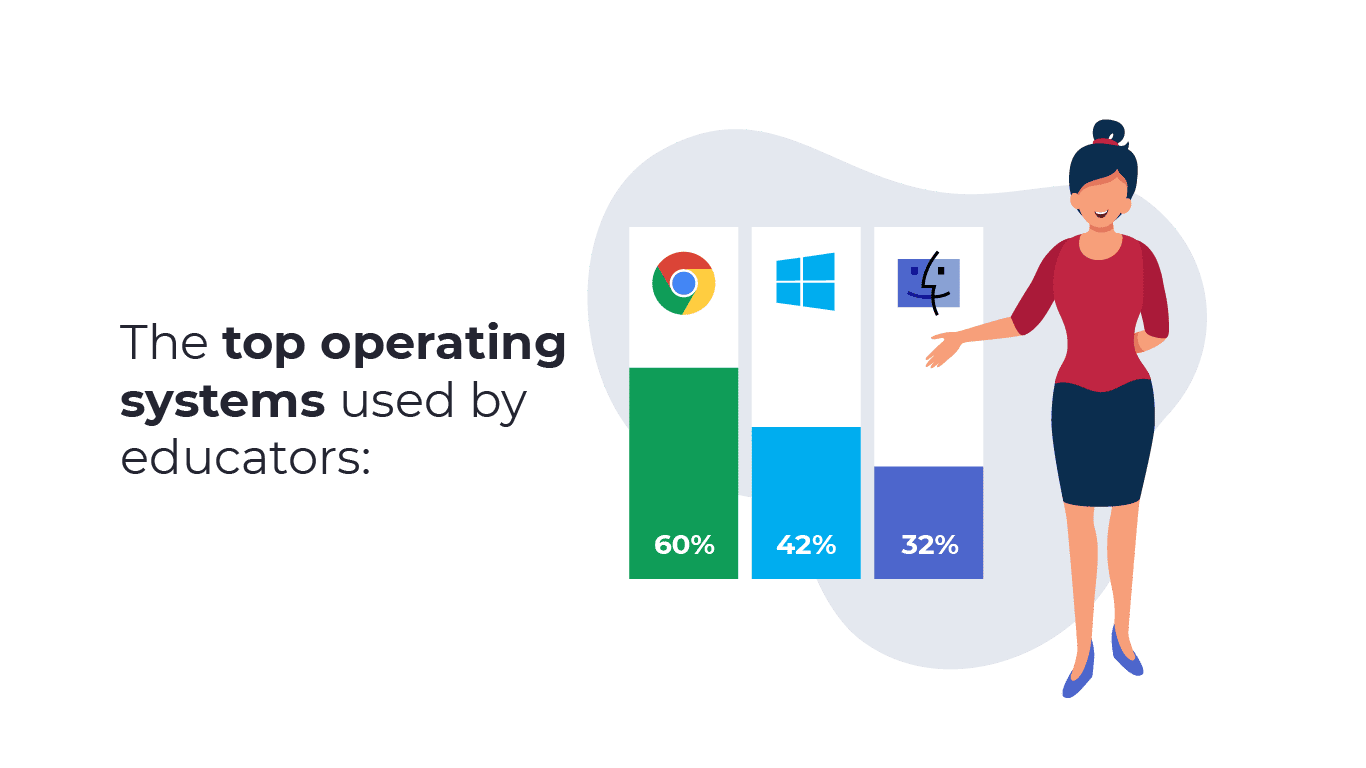
Among respondents using devices provided by their school, 60% reported their devices use the ChromeOS operating system. 42% of respondents indicated their school-supplied devices used the Microsoft Windows operating system, and 32% of school devices used Apple’s iOS or MacOS operating system.
Google’s ChromeOS has surged in popularity among schools thanks to its high security standards and user-friendly design. For school IT leaders, moving all students and educators to more secure devices should be a goal, but additional steps to properly monitor, manage, and secure remote devices must not be forgotten.
Key takeaways:
- Students need to be trained further on better device management strategies.
- Schools are recommended to make regular cybersecurity training mandatory for all students.
Conclusion
Based on these results, many schools appear to lack a consistent device policy that would protect educators, students and school networks. Ransomware, in particular, poses one of the most significant threats to schools and is a heightened risk school IT leaders must protect themselves against in an era of remote learning.
One area in which school IT leaders and MSPs that serve the education sector can make the most difference with the least resources is educating students and staff on basic cybersecurity training and hygiene.
Now more than ever, the benefits of having a remote endpoint monitoring and management platform installed across every device are salient. From the increased agility and intelligence derived from a remote monitoring and management platform, school IT leaders can be more strategic in their actions while reducing costs and increasing the security and performance of remote end users.
Read more of NinjaOne’s original research and insights on our blog. There, readers can access free tools and resources to help you build a better MSP.
Read More:
- What Should You Be Monitoring with Your RMM? 28 Recommendations
- Guide to Managed Services Agreements for Managed IT Services Providers