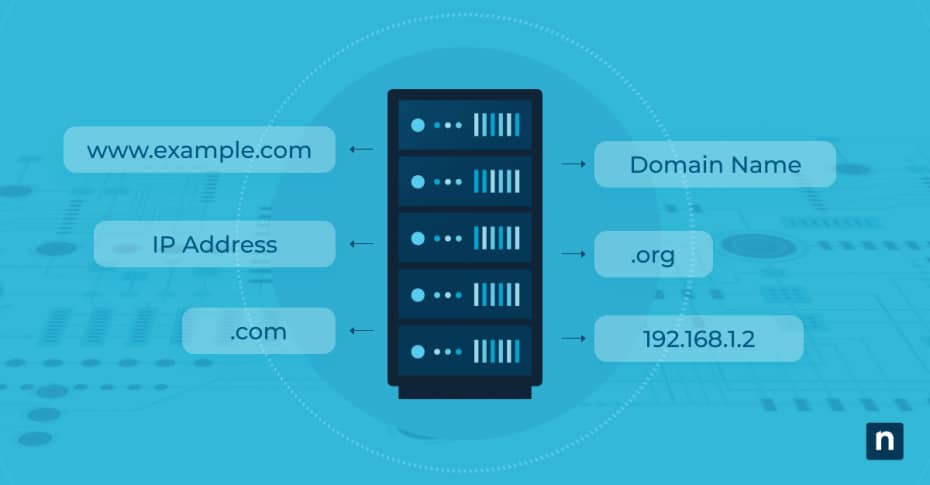
The Domain Name System, commonly known as DNS, is a fundamental component of the internet, yet it remains a mystery to many users. Simply put, DNS is like the phonebook of the internet, translating human-friendly domain names such as www.ninjaone.com into IP addresses that computers use to identify each other on the network.
Without DNS, browsing the web would be a cumbersome process, requiring us to remember complicated numerical addresses for every website we want to visit.
In this article, we will demystify DNS, explaining its importance, how it works, and its critical role in our everyday online activities. Whether you’re a beginner looking to understand the basics or a tech enthusiast seeking deeper insights, this guide will provide you with a comprehensive understanding of the DNS protocol.
What is DNS and why is it used?
The Domain Name System (DNS) is a hierarchical and decentralized naming system used to identify computers, services, and other resources reachable through the internet or other IP networks. Essentially, DNS converts user-friendly domain names into IP addresses, enabling browsers to locate and load internet resources.
For example, when you type “www.example.com” into your browser, DNS translates this domain name into an IP address like “192.0.2.1,” directing your browser to the correct website.
DNS operates through a series of DNS servers:
- DNS resolver: This server receives queries from client machines, such as your computer or smartphone.
- Root name server: This server responds to requests for records in the root zone and directs queries to the appropriate top-level domain (TLD) servers.
- TLD name server: This server handles requests for specific TLDs, such as .com or .org, directing queries to the authoritative name servers for the requested domain.
- Authoritative same server: This server contains the actual DNS records for the requested domain and responds with the IP address corresponding to the domain name.
The evolution of DNS
Before DNS was established, early internet users relied on a simple text file called the HOSTS file, which mapped domain names to IP addresses. This method quickly became impractical as the number of hosts on the ARPANET (the precursor to the modern internet) grew exponentially.
In 1983, Paul Mockapetris proposed DNS as a scalable solution to this problem, and by 1984, DNS was formally implemented in the ARPANET. The introduction of DNS marked a significant milestone, as it allowed the internet to grow without the limitations of manually updated HOSTS files.
Over the years, DNS has evolved to support various advanced features such as DNS Security Extensions (DNSSEC), caching mechanisms, and Internationalized Domain Names (IDNs).
The role of DNS in simplifying internet navigation
DNS plays a crucial role in making the internet accessible and user-friendly. Imagine if, instead of typing “www.google.com,” you had to remember and enter “172.217.16.196” every time you wanted to perform a web search. DNS abstracts these complex numerical IP addresses, allowing us to use easy-to-remember domain names.
Moreover, DNS enables:
- Scalability: By distributing the load across multiple servers, DNS ensures that no single server becomes a bottleneck, thus supporting the vast number of queries generated by billions of internet users.
- Redundancy: Multiple DNS servers provide resilience against failures, ensuring that internet services remain accessible even if some servers go down.
- Load balancing: DNS can distribute traffic across multiple servers hosting the same content, improving performance and reliability.
Still asking “what is DNS needed for?” The simple answer is this: Think of DNS as a cornerstone of internet infrastructure, allowing us to use the URLs and domain names that we all depend on when navigating the internet and sending emails.
How DNS works
So, how does the Domain Name System (DNS) translate domain names into IP addresses? Here’s a detailed breakdown of how DNS works:
The DNS query process
When you enter a domain name (e.g., www.example.com) into your web browser, a series of steps is triggered to resolve this domain name into an IP address:
Step 1: User’s request
- User action: You type the domain name into your browser and press enter.
- DNS resolver: The browser sends a query to the local DNS resolver, usually managed by your Internet Service Provider (ISP).
Step 2: Recursive query
- Recursive resolver: The local DNS resolver acts as a recursive resolver, meaning it will perform a sequence of queries to resolve the domain name fully.
Step 3: Root name server query
- Root server query: The recursive resolver queries a root name server to find out which authoritative server is responsible for the top-level domain (TLD) of the requested domain (e.g., “.com”).
- Root server response: The root server responds with the IP address of the TLD name server.
Step 4: TLD name server query
- TLD server query: The recursive resolver queries the TLD name server specified by the root server to find out which authoritative name server is responsible for the second-level domain (e.g., “example”).
- TLD server response: The TLD server responds with the IP address of the authoritative name server for the domain “example.com.”
Step 5: Authoritative name server query
- Authoritative server query: The recursive resolver queries the authoritative name server to get the IP address of the specific domain (e.g., “www.example.com”).
- Authoritative server response: The authoritative name server responds with the IP address associated with the domain name.
Step 6: Response to user
- Resolver to browser: The recursive resolver returns the IP address to the user’s browser.
- Connection established: The browser uses the IP address to establish a connection with the web server, retrieving the website content.
Components of DNS
- DNS resolver: This is the first point of contact for the user’s DNS query. It is responsible for handling the query and passing it along to other servers if needed.
- Root name server: The root name server is the top-level DNS server that responds to queries for TLDs (e.g., .com, .org, .net) and directs the query to the appropriate TLD server.
- TLD name server: The TLD server manages domain names within the top-level domain. For example, the .com TLD server handles requests for all .com domains.
- Authoritative name server: This server holds the DNS records for specific domains and responds with the IP address or other information related to the domain.
Caching and TTL (Time to Live)
To improve efficiency and reduce load times, DNS employs caching mechanisms:
- Local cache: Both the user’s browser and the DNS resolver cache the DNS responses for a certain period.
- TTL (Time to Live): Each DNS record has a TTL value, specifying how long it should be cached before a new request is made. Lower TTL values result in more frequent updates but higher server load, while higher TTL values reduce server load but may serve outdated information.
Security enhancements
DNSSEC (DNS Security Extensions): DNSSEC adds a layer of security by allowing DNS responses to be verified through digital signatures, ensuring that the responses have not been tampered with.
Load balancing and failover
DNS can also be used for load balancing by distributing traffic among multiple servers hosting the same service, enhancing reliability and performance. For failover purposes, multiple DNS records can be configured to ensure that if one server goes down, another can take its place without disrupting the user experience.
What are the types of DNS records?
DNS relies on various record types to direct traffic appropriately. The most common DNS record types include:
- A Record (Address Record): Maps a domain name to an IPv4 address.
- AAAA Record: Maps a domain name to an IPv6 address.
- CNAME Record (Canonical Name Record): Alias of one domain name to another. Useful for pointing multiple domain names to the same IP address.
- MX Record (Mail Exchange Record): Specifies the mail server responsible for receiving email on behalf of a domain.
- TXT Record: Stores text information related to the domain, often used for security purposes like SPF (Sender Policy Framework) or DKIM (DomainKeys Identified Mail).
Common DNS issues and troubleshooting
DNS server outages
When DNS servers go down due to maintenance, cyber-attacks, or technical failures, users cannot resolve domain names to IP addresses. This results in the inability to access websites, effectively cutting off internet connectivity.
DNS propagation delays
Changes to DNS records (such as changing the IP address of a domain) can take time to propagate across all DNS servers worldwide due to the TTL settings. During this period, some users might get the old DNS information while others get the updated information.
DNS cache poisoning (DNS Spoofing)
Malicious actors can corrupt the DNS cache, causing users to be directed to fraudulent or malicious sites instead of the intended websites. This can lead to phishing attacks, data theft, and other security issues.
Misconfigured DNS records
Incorrect DNS configurations, such as wrong IP addresses or mistyped domain names, can lead to failure in resolving the domain names properly.
Network congestion and latency
High traffic volumes or network congestion can slow down the DNS query process, leading to delayed responses and slower access to websites.
How to diagnose and resolve DNS issues
-
Checking network connectivity
Ensure that your internet connection is stable. A disconnected or unstable network can mimic DNS issues.
Diagnosis tools: Ping, tracert (Windows) or traceroute (Mac/Linux).
Resolution: Fix any network connection problems, such as reconnecting to the network or restarting the router.
-
Verifying DNS server settings
Ensure that your DNS settings are correct and pointing to valid DNS servers.
Diagnosis tools: Command prompt/terminal commands like ipconfig /all (Windows) or cat /etc/resolv.conf (Linux/Mac).
Resolution: Correct any misconfigured DNS server settings in your network or device settings.
-
Flushing the DNS cache
Clear the DNS cache to ensure that outdated or corrupt DNS records are not causing the issue.
Diagnosis tools: None needed.
Resolution: Use commands like ipconfig /flushdns (Windows), sudo dscacheutil -flushcache; sudo killall -HUP mDNSResponder (Mac), or sudo systemd-resolve –flush-caches (Linux).
-
Testing with different DNS servers
Switch to alternative DNS servers, such as Google DNS (8.8.8.8, 8.8.4.4) or Cloudflare DNS (1.1.1.1), to see if the issue is with your current DNS server.
Diagnosis tools: Change DNS settings on your device or router and test.
Resolution: Use reliable and fast public DNS servers if your ISP’s DNS servers are experiencing issues.
-
Using nslookup or dig Commands
Use these commands to manually query DNS records and diagnose issues with specific domains.
Diagnosis Tools: nslookup (Windows) or dig (Linux/Mac).
Resolution: Analyze the output to identify where the DNS query is failing and take appropriate action (e.g., updating DNS records or contacting your DNS provider).
Tools and techniques for DNS troubleshooting
nslookup
A command-line tool for querying DNS to obtain domain name or IP address mapping and other DNS records.
Usage: nslookup www.example.com
dig (Domain Information Groper)
A powerful command-line tool used for querying DNS servers and diagnosing DNS problems.
Usage: dig www.example.com
traceroute/tracert
Tools that trace the path packets take from your computer to the destination, helping identify where the connection is failing.
Usage: tracert www.example.com (Windows) or traceroute www.example.com (Linux/Mac).
Ping
A basic network tool to test the reachability of a host and measure round-trip time for messages sent.
Usage: ping www.example.com
Online DNS tools
Web-based tools like DNSstuff, MXToolbox, and What’s My DNS can provide insights into DNS propagation, lookups, and performance.
Usage: Visit the tool’s website and enter the domain name to diagnose.
Browser developer tools
Most modern web browsers include developer tools that can help diagnose DNS and network issues.
Usage: Open the developer tools (F12 in most browsers), navigate to the “Network” tab, and observe DNS resolution times and any errors.
DNS security and best practices
Common DNS vulnerabilities and threats
DNS spoofing (DNS cache poisoning): Attackers manipulate DNS cache to return incorrect IP addresses, directing users to malicious sites instead of the intended destination. This exposes users to phishing attacks, malware, and data theft.
DDoS attacks on DNS servers: Distributed Denial of Service (DDoS) attacks flood DNS servers with excessive queries, overwhelming them and causing service outages. This results in websites becoming unreachable, disrupting services, and causing potential financial losses.
DNS hijacking: Attackers take control of DNS settings, redirecting traffic from legitimate websites to malicious sites. This leads to compromised user data, financial loss, and damage to brand reputation.
Man-in-the-middle attacks: Attackers intercept DNS queries and responses, altering them to redirect users or steal sensitive information. This results in unauthorized access to user data, breach of privacy, and exposure to further attacks.
DNS tunneling: Exploiting the DNS protocol to tunnel malware or data through DNS queries and responses. This leads to data exfiltration, unauthorized communication channels, and network security breaches.
Implementing DNSSEC (DNS Security Extensions) for enhanced security
DNS Security Extensions (DNSSEC) add a layer of security to DNS by enabling DNS responses to be verified through digital signatures, ensuring data integrity and authenticity. Here are the steps to implement DNSSEC:
Zone signing
- Key Generation: Generate a pair of cryptographic keys (public and private) for your DNS zone.
- Sign the Zone: Use the private key to sign DNS records in your zone, creating a digital signature for each record.
Publishing keys
- Publish public key: Publish the public key in the DNS zone as a DNSKEY record.
- Parent zone update: Update the parent zone with a Delegation Signer (DS) record that contains a hash of your public key, establishing a chain of trust.
Resolver configuration
- DNSSEC-aware Resolvers: Ensure that DNS resolvers are configured to validate DNSSEC signatures by checking the authenticity of the responses using the chain of trust.
Best practices for DNS management and configuration
- Use reliable DNS providers: Choose reputable and secure DNS hosting providers that offer features like DNSSEC, DDoS protection, and robust infrastructure.
- Regularly update DNS software: Ensure that DNS server software is up to date with the latest security patches and updates.
- Implement DNSSEC: Enable DNSSEC for your domains to protect against tampering and spoofing.
- Monitor DNS traffic: Continuously monitor DNS traffic for unusual patterns or anomalies that could indicate an attack.
- Use split-horizon DNS: Implement split-horizon DNS to provide different DNS responses based on the source of the request, enhancing security for internal and external queries.
- Limit zone transfers: Restrict zone transfers to specific IP addresses and use TSIG (Transaction Signature) keys to authenticate zone transfer requests.
- Apply least privilege principle: Ensure that only authorized personnel have access to DNS configuration and management.
- Regularly review DNS records: Periodically audit DNS records to remove outdated or unnecessary entries and to ensure accuracy.
Protecting against DNS spoofing and cache poisoning
- Implement DNSSEC: Deploy DNSSEC as discussed above to validate DNS responses and ensure data integrity.
- Use secure DNS resolvers: Utilize resolvers that support DNSSEC validation and have features to detect and mitigate spoofing attempts.
- Employ DNS filtering: Use DNS filtering services to block access to known malicious domains and IP addresses.
- Enable DNS query rate limiting: Implement rate limiting on DNS queries to reduce the risk of cache poisoning through flood attacks.
- Regularly flush DNS cache: Periodically clear DNS caches to minimize the risk of poisoned entries lingering and affecting users.
- Use randomized source ports and transaction IDs: Randomize source ports and transaction IDs for DNS queries to make it more difficult for attackers to guess and spoof responses.
- Monitor and analyze DNS logs: Continuously monitor DNS logs for signs of suspicious activity, such as repeated queries for the same domain or unusual response patterns.
- Educate users: Educate users about the risks of phishing and the importance of verifying website URLs to reduce the likelihood of falling victim to spoofing attacks.
How to perform a DNS lookup
Performing a DNS lookup involves querying a DNS server to obtain the IP address associated with a domain name. Here is a step-by-step guide:
1. Open a terminal or command prompt: Access the command-line interface on your computer. For Windows, use Command Prompt or PowerShell; for macOS and Linux, use the Terminal.
- Choose a DNS query tool: Select a tool such as nslookup or dig.
- Enter the DNS query command:
- For nslookup, type: nslookup [domain name]
- For dig, type: dig [domain name]
- Press Enter: Execute the command to send the DNS query.
4. Review the results: Analyze the response returned by the DNS server, which includes the IP address and additional DNS information.
Online DNS lookup tools
Several web-based tools are available for performing DNS lookups without needing to use the command line. These options are convenient for quick checks and are accessible from any device with an internet connection. Popular online DNS lookup tools include:
What’s My DNS: Provides global DNS propagation status by checking DNS records from multiple locations worldwide.
MXToolbox: Offers a variety of DNS lookup services, including A, MX, CNAME, and TXT record queries, as well as blacklisting checks.
DNSstuff: Provides comprehensive DNS tools for checking DNS records, propagation, and troubleshooting issues.
DNS Spy: Monitors DNS records and alerts users about changes or potential issues.
These online tools are user-friendly and typically require entering the domain name and selecting the record type to perform the lookup.
Interpreting DNS lookup results
Understanding the results of a DNS lookup is crucial for diagnosing and resolving DNS-related issues. Here’s how to interpret common fields in DNS lookup results:
A Record (Example: www.example.com A 93.184.216.34)
Indicates the IP address associated with a domain name.
MX Record (Example: example.com MX 10 mail.example.com)
Lists the mail servers for a domain, with priority values indicating the order in which servers should be used.
CNAME Record (Example: www.example.com CNAME example.com)
Shows alias records, which point one domain name to another.
NS Record (Example: example.com NS ns1.example.com)
Displays the authoritative name servers for the domain.
TXT Record (Example: example.com TXT “v=spf1 include:_spf.google.com ~all”)
Contains text information for various purposes, such as SPF or DKIM configurations.
SOA Record (Example: example.com SOA ns1.example.com admin.example.com 2024051701 3600 900 1209600 3600)
The Start of Authority record provides administrative information about the domain, including the primary name server, responsible party email, and domain serial number.
Interpreting these results helps in understanding how a domain is configured, identifying potential misconfigurations, and troubleshooting issues related to DNS resolution.
In summary
Understanding DNS (Domain Name System) is crucial for navigating the internet effectively and ensuring secure, efficient access to web services. By following these guidelines, users and administrators can ensure robust DNS configurations, enhancing both the performance and security of their internet experience.