Malware as a Service (MaaS) is a direct replica of the Software as a Service (SaaS) business model you’re already familiar with. In the same way that SaaS customers are able to purchase software via rapid and scalable licensing, online communities of threat actors have paved the way toward a highly efficient, distributed malware economy of their own.
Malware distribution used to be direct – usually from the same attacker or group as those that created it. Take one of the early mass botnets, Bredolab. Infecting 30 million Windows systems by 2009, an Armenian malware author was singularly responsible for the malware that would take over victims’ devices to send out fresh barrages of spam.
Only two years after Bredolab, one of the earliest MaaS schemes would be discovered in the wild. The Andromeda botnet operated almost identically to its predecessor, with the added functionality of an optional second-stage form of malware.
Through this, malware gangs could pay the relevant Andromeda botnet operator to implant their own ransomware and spyware on an already-vulnerable device. Deploying malware was suddenly far easier – these botnets could suddenly provide a direct link to the victim.
MaaS today
Nowadays, modern MaaS platforms offer a staggering range of customizable options. The owners of these platforms are paid by the attackers and are able to amass illicit profits with far less risk. Actively deploying malware onto a victim’s device now takes less skill and time – meaning anyone can administer attacks.
MaaS providers sometimes even offer malware directly for hire, with customers simply choosing from their ranges of infected devices and the malware on offer.
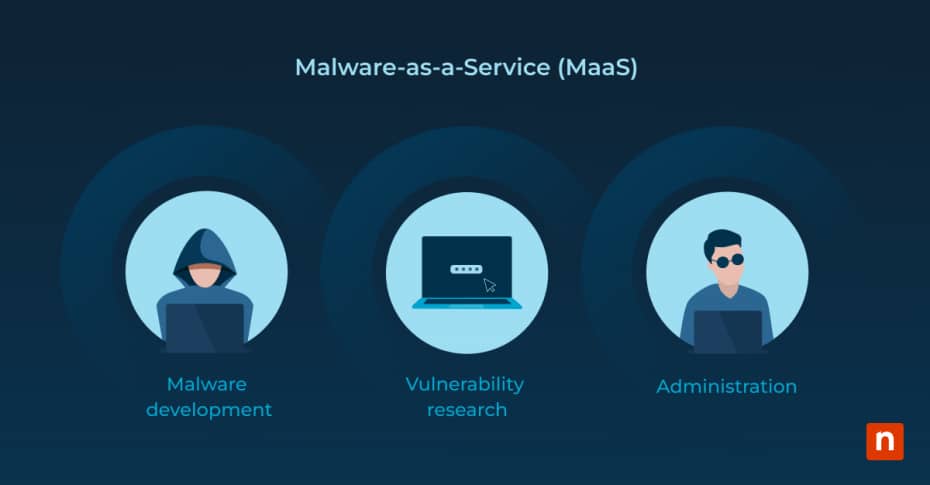
The MaaS ecosystem can be broken down into a few key components. Developers are the ones that research and discover oversights in legitimate operating systems or applications, and create and license their own strains of malware.
A customer will often find their malware or botnet of choice via a dark web market or by word-of-mouth recommendations in the right circles. Payment models can vary from one-off purchases to monthly subscriptions, or paying a portion of the profits gained.
Assuming the user isn’t interacting with a scammer, their purchase can also include instructions on how to adapt the malware to meet the specific demands of its deployment.
Some others are botnet handlers that offer control over established botnets. Access brokers offer a wider degree of paid access – they often sell off infected networks alongside the malware. Affiliates who purchase access to compromised systems often remain indifferent to the methods used to breach these systems initially.
Their primary use of these systems is as “jump servers” to facilitate further activities within a network. While access brokers may provide details about the networks for sale, affiliates typically focus more on the opportunities these networks offer for monetization rather than the specific network characteristics themselves.
A dive into today’s RedLine MaaS
Some of the largest and most sophisticated MaaS campaigns are financially motivated. Recent warnings around the RedLine Stealer malware have spiked, thanks to the ongoing evolution of the tool. After a break throughout 2022 – where the developers presumably took the time to re-code large pieces of the codebase – the end of 2023 saw a new flood of RedLine activity.
Securing illicit profit is fairly accessible with data stealers such as RedLine. Able to rapidly and efficiently break into systems, high-value data can then be exfiltrated and used to extort the victim further. Now, RedLine is thought to be reliant on other malware and exploit kits.
TrendMicro’s mid-2023 report detailed one avenue of attack, in which malicious advertisements for AI tools such as Midjourney led victims to download strains of RedLine. This goes some way to showing how MaaS economies are complex and interconnected: RedLine customers are able to purchase device access through the malvertisement operators, providing a way in for their newly-purchased tooling.
After the victim goes ahead with the malicious Midjourney installer, a fake download window is shown while a Powershell installation occurs in the background. Once executed, RedLine exfiltrates as much sensitive information as possible, including browser cookies, crypto wallet info, passwords, and more.
The latest RedLine variants have made an even greater effort to reduce the malware’s discoverability. Excluding the PowerShell process is only example thereof: a further focus on automation could also allow savvy attackers to bypass any victim interaction at all. Alongside this is an automation ability to delete files the malware creates, helping conceal the cyberattack.
Ultimately, RedLine is so dangerous precisely in the same way it excels as a MaaS superstar: its multifaceted distribution strategies present a severe headache for antivirus solutions and security professionals. Its decentralized architecture means it can fit in with a host of different approaches, from phishing to zero days – further letting it pave the way for wider attack campaigns.
How MaaS affects business security
MaaS makes the barrier of entry for cybercrime incredibly low. Novice attackers no longer need the skills and experience to start side-stepping the decades’ worth of defenses your organization may have. In the case of RedLine, the business security repercussions are significant.
Upon first installation, RedLine attempts to detect any firewall and antivirus software installed on the Windows machine. From there, it checks any processes currently running before honing in on a few particularly important ones.
Querying the Outlook app’s registry keys allows it to retrieve login information, which is sent back to the attackers – alongside the OS version you are running on, your mail data, and any cryptocurrency wallet locations. Browser data is particularly valuable for attackers, and RedLine pilfers any cookies and session data it can get its digital hands on.
Due to the various unique strains of MaaS software, some infections present with slightly different goals: this is why screen and key-log capture activities are reported in some infections but not all.
As a result, MaaS victims are left battling major holes in business security. The data exfiltrated in these attacks is rapidly used or sold to further empower more attacks. This snowball effect must be prevented at the source by analyzing MaaS defensive strategies.
Defensive strategies against MaaS
When something suspicious has been found on an employee device, it’s not necessarily the end of that attack. If an attack’s specific techniques are identified, attackers might still remain within the network, leveraging other gathered insights to circumvent security measures.
Often, attackers trial their techniques directly within the target’s environment, deploying common malware or other tools from a concealed position. When these are thwarted by antivirus solutions, attackers typically switch tools, alter their malware, or interfere with the security measures they face.
Because of this, safeguarding against MaaS attacks in the first place becomes critical. This demands much the same strategies as you’re likely already familiar with. Phishing links and out-of-date software are the two most common paths of attack, making them key areas of defense.
Employees need to be supported with regular, actionable intel on the latest phishing threats, and your organization’s tech stack must be maintained to the highest possible standard.
Microsoft’s deep-dive into ransomware-as-a-service takes great pains to highlight the vulnerabilities that can stem from misconfigured security products. Often, the initial point of entry for these attacks is a legacy system lacking robust antivirus or Endpoint Detection and Response (EDR) solutions.
Due to the highly privileged credentials being held, a single oversight can be all an attacker needs to execute malware without detection. Some access brokers even market this capability as a selling point, highlighting the ease of exploiting these security gaps.
It’s critical that your organization keeps its security tools configured for optimal protection – regular network scans help verify that all systems, including servers, are adequately monitored and secured by appropriate security products. If it is not feasible to monitor all systems effectively, it’s crucial to isolate legacy systems either physically, using a firewall, or logically, by preventing any credential overlap with other systems.
Learn more about ransomware-as-a-service.
MaaS into the future
Darktrace’s 2023 End of Year Threat Report issued a grave threat to the future of MaaS: while the creation of the malware gig economy is seeing a rapidly increasing rate of attacks, there’s also an underlying evolution taking place. Many malware strains are becoming increasingly cross-functional, with Remote Access Trojans seeing heavy combination with spyware.
Together, these two jointly-occuring shifts are ratcheting up the threat level of every organization across the globe. With suites of AI tooling already fueling higher malware deployment, it is critically important to be aware of the MaaS economy and assess your own preparedness.