Virtual Local Area Networks, or VLANs, are a fundamental component of network design, serving as a tool for optimizing network segmentation and security. Whether you’re a network administrator looking to enhance your understanding or a curious tech enthusiast eager to explore the intricacies of VLANs, this article will provide a comprehensive overview.
We’ll define what VLANs are, explore their primary purpose, and examine the numerous advantages they offer, helping you fully understand the significance of VLANs in the dynamic world of networking.
What this article will cover:
- What is a VLAN?
- VLAN vs. LAN
- How does VLAN work?
- The purpose of VLANs in networking
- VLAN types and variations
- VLAN benefits
- Setting up and configuring a VLAN
- Example of VLAN implementation
What is a VLAN?
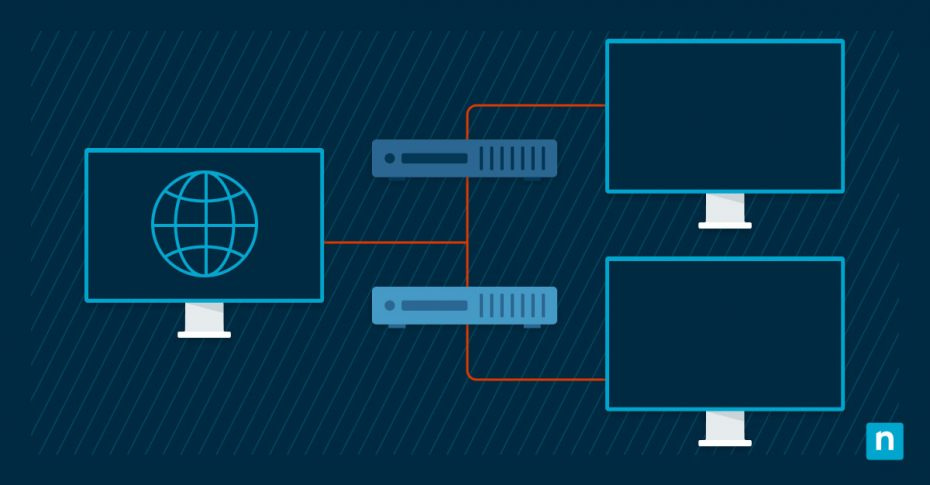
Virtual Local Area Networks, commonly known as VLANs, are a fundamental concept in modern networking. At its core, a VLAN setup is a logical, software-based segmentation of a physical network.
Unlike traditional LANs, where endpoint devices are physically connected to the same network segment, VLANs enable the creation of isolated, virtual networks within a physical network infrastructure. Each VLAN acts as an independent, self-contained network with its own set of rules, security policies, and broadcast domains.
NinjaOne RMM solution allows you to monitor VLAN-connected devices easily.
Logical network segmentation
The VLAN in networking is designed to provide a flexible and efficient means of network segmentation by grouping devices together based on factors such as department, function, or security requirements. By grouping in this way, VLANs effectively create separate communication domains within a shared physical infrastructure.
This logical separation ensures that devices within the same VLAN can communicate with each other as if they were on the same physical network, while communication between devices in different VLANs is regulated by routing and access control mechanisms. This segmentation enhances network management, improves security, and optimizes traffic management, ultimately leading to better network performance.
VLAN vs. LAN
One of the key differentiators between VLANs and traditional physical LANs lies in their flexibility and scalability. Physical LANs require dedicated cabling and hardware for each network segment, making them less adaptable to changes and often leading to inefficient use of resources.
In contrast, VLANs are purely software-defined and can be reconfigured or expanded with ease. This virtualization of network segments allows for a more dynamic and cost-effective network design. VLANs are also free from the constraints of physical proximity, enabling devices in the same VLAN to be dispersed throughout the physical network while still behaving as if they are connected to the same local network switch.
This versatility makes VLANs an invaluable tool for network administrators seeking to optimize network management, security, and performance in an ever-evolving digital landscape.
What is a VLAN trunk?
A VLAN trunk is a network link or connection that can carry multiple VLANs simultaneously and is typically established between network devices (such as switches or routers) to transport traffic for multiple VLANs over a single physical connection.
What is VLAN tagging?
VLAN tagging is a method used to identify and distinguish different VLANs on the same physical network infrastructure and involves adding a small piece of metadata (see below) to the Ethernet frame header, indicating the VLAN to which the frame belongs.
What is a VLAN ID?
A numerical value assigned to a VLAN to uniquely identify it within a network. Each VLAN is associated with a specific VLAN ID, which is a 12-bit value (ranging from 1 to 4095) embedded in the VLAN tag added to the Ethernet frame header.
How does a VLAN work?
VLANs operate by segmenting a single physical network into multiple logical networks, each with its own VLAN membership. Devices that belong to a particular VLAN share a common membership, meaning they can communicate with one another without restrictions, just as if they were part of the same physical LAN.
This membership is determined by specific criteria, often based on factors like device type, location, department, or function. As a result, VLANs effectively isolate broadcast domains, reducing the broadcast traffic that can congest a network. Broadcast traffic is contained within each VLAN, preventing unnecessary network congestion and enhancing overall network efficiency.
Trunk ports and their role in VLAN communication
To facilitate communication between VLANs and ensure that data can flow smoothly from one virtual network to another, network switches use special ports known as trunk ports. Trunk ports are the highways that carry data between VLANs. They are configured to carry traffic from multiple VLANs, effectively acting as multiplexers for inter-VLAN communication.
By tagging each data packet with a VLAN identifier (known as a VLAN tag), the switch can distinguish which VLAN the packet belongs to, allowing it to route the data to the correct destination VLAN. Trunk ports are essential for connecting switches and routers that serve multiple VLANs within a network, creating a cohesive and interconnected network infrastructure.
Inter-VLAN routing for facilitating communication between VLANs
While VLANs provide a means of segmenting network traffic, there are times when devices in different VLANs need to communicate with each other. This is where inter-VLAN routing comes into play. Inter-VLAN routing allows data to traverse between VLANs with the assistance of routers or Layer 3 switches.
These devices serve as gateways between the VLANs, enabling the routing of data packets between different virtual networks. By controlling the flow of traffic between VLANs, network administrators can implement security policies, access controls, and Quality of Service (QoS) rules, ensuring that cross-VLAN communication is both secure and efficient.
The purpose of VLANs in networking
VLANs serve a multi-faceted purpose in networking. They bolster security by isolating sensitive data, streamline network administration by reducing broadcast domains, and provide flexibility in network design and expansion. Their ability to segment and compartmentalize network traffic is a fundamental tool for modern network architects, enabling them to build agile, secure, and efficient network infrastructures that can meet the demands of contemporary businesses and organizations. Let’s explore these functions in detail:
Isolating sensitive data and creating secure network segments
One of the primary purposes of VLANs is to enhance network security by isolating sensitive data and creating secure network segments. By segregating devices into different VLANs based on their roles or security requirements, organizations can ensure that critical information remains isolated from less sensitive parts of the network. For example, a finance department’s VLAN can be kept separate from a guest network, preventing unauthorized access to confidential financial data. This isolation minimizes the risk of data breaches and unauthorized access, as well as reducing the potential attack surface within the network.
Streamlining network administration and reducing broadcast domains
VLANs play a pivotal role in simplifying network management and optimizing network performance. Traditional LANs often suffer from broadcast storms, which occur when broadcast traffic floods the network and degrades performance. By isolating broadcast domains within each VLAN, these issues are contained, reducing network congestion and improving overall efficiency. Moreover, network administrators can define and apply policies, such as Quality of Service (QoS) rules and access controls, more effectively within each VLAN, tailoring network management to the specific needs of each segment. This fine-grained control streamlines network administration and enhances the user experience.
Providing flexibility in network design and expansion
VLANs offer remarkable flexibility in network design and expansion. Unlike traditional LANs, which require significant physical infrastructure changes to accommodate network growth or reconfiguration, VLANs are purely software-defined. This means that network architects can easily adapt and extend their network structure without the need for additional hardware investments. Whether it’s adding new departments, accommodating remote employees, or adapting to changes in business needs, VLANs enable network architects to scale and redesign the network infrastructure swiftly and cost-effectively.
VLAN types and variations
Understanding these various VLAN configurations and their specialized roles is essential for designing and maintaining a robust and efficient network that caters to the specific needs of diverse applications and devices.
Port-Based VLANs vs. Tag-Based VLANs
In the realm of VLANs, two primary approaches are employed: port-based VLANs and tag-based VLANs. Port-based VLANs assign a specific physical port on a network switch to a particular VLAN, segregating devices based on the physical connection they use. Tag-based VLANs, on the other hand, rely on 802.1Q or similar protocols to add a VLAN tag to each data packet, designating its membership to a particular VLAN. This method allows multiple VLANs to coexist on the same physical port, permitting more flexibility and efficient use of network resources. Tag-based VLANs are commonly used in more complex network setups, while port-based VLANs are simpler and often preferred in smaller-scale deployments.
Voice VLANs for prioritizing VoIP traffic
Voice VLANs are specialized configurations designed to optimize Voice over Internet Protocol (VoIP) traffic within a network. In VoIP systems, it’s critical to ensure high-quality, real-time communication. Voice VLANs prioritize and separate voice traffic from data traffic, enabling consistent and low-latency voice communication. Devices such as IP phones or VoIP gateways are typically placed in a Voice VLAN, which is configured to provide the necessary Quality of Service (QoS) settings to guarantee reliable voice communication.
Management VLANs for network administration
Management VLANs serve as dedicated segments for network administration tasks. These VLANs are designed to separate network management traffic, such as accessing network devices for configuration, monitoring, and maintenance. By isolating management traffic in its own VLAN network, administrators can enhance security, minimize the risk of unauthorized access, and prioritize network management operations, ensuring the efficient operation of the network.
Default VLAN and Native VLAN
The Default VLAN is a fundamental concept in VLAN configuration, usually identified as “VLAN 1.” In many cases, devices are placed in the Default VLAN by default when they are not explicitly assigned to a specific VLAN. It’s essential to note that VLAN 1 has special significance and should be handled with care to avoid potential security vulnerabilities.
The Native VLAN, on the other hand, is a critical component of tag-based VLANs. It is the Virtual LAN that carries untagged traffic between switches in a tagged VLAN configuration. This untagged traffic often includes control and management traffic between switches, and the Native VLAN should be consistent across interconnected devices to ensure proper communication between them.
VLAN benefits
Virtual Local Area Networks (VLANs) offer a wide range of benefits that make them an indispensable tool in modern network design and administration. Here are some of the key advantages of using VLANs:
- Enhanced network security
VLANs provide a powerful means of isolating sensitive data and securing network segments. By logically segregating devices into separate VLANs, organizations can control access and prevent unauthorized users from infiltrating critical parts of the network. This added layer of security reduces the risk of data breaches and enhances overall network protection.
- Optimized network performance
VLANs help streamline network administration by reducing broadcast domains. Traditional LANs can be prone to broadcast storms, which congest the network and degrade performance. By isolating broadcast domains within VLANs, this issue is contained, resulting in more efficient network traffic management and improved performance.
- Improved traffic management
VLANs enable network administrators to define and apply Quality of Service (QoS) rules, access controls, and routing policies specific to each VLAN. This granular control allows for the prioritization of critical traffic, ensuring that important data, such as voice or video, receives the necessary bandwidth and low latency for reliable communication.
- Efficient resource utilization
VLANs can help organizations make more efficient use of network resources. Rather than requiring separate physical network infrastructures for different departments or functions, VLANs allow multiple virtual networks to coexist on the same physical infrastructure. This versatility reduces hardware costs and simplifies network monitoring and management.
- Scalability and flexibility
VLANs are highly adaptable and easily scalable. Network architects can create new VLANs or reconfigure existing ones without the need for significant changes to the physical infrastructure. This flexibility is particularly advantageous in dynamic business environments where networks must evolve rapidly to accommodate changes in demand or organization.
- Isolation of problematic devices
VLANs allow network administrators to isolate problematic devices, reducing the impact of network issues. If a device within a VLAN experiences network problems or exhibits malicious behavior, it won’t affect the performance of other VLANs, providing enhanced network stability and reliability.
- Effective multi tenancy support
In scenarios where multiple organizations or clients share the same physical network infrastructure, VLANs can be used to create separate virtual networks for each entity. This approach facilitates secure multitenancy and ensures that each entity’s data remains private and isolated.
- Simplified network management
VLANs simplify network management by logically grouping devices based on their roles, which makes it easier to apply consistent network policies and configurations. This simplification can reduce the complexity of network administration and lower the risk of misconfigurations.
Setting up and configuring a VLAN
Setting up and configuring a VLAN can be a crucial task in managing your network’s security and performance. Here’s a short guide on how to set up and configure a VLAN:
Step 1: identify your VLAN requirements
Before you start configuring a VLAN, identify the specific needs and goals for your network segmentation. Consider which devices or groups of devices need to be isolated or grouped together. Determine whether you need separate VLANs for security, traffic management, or other purposes.
Step 2: access your network equipment
Access the network equipment, such as switches, routers, or Layer 3 switches, that will be used to configure the VLANs. Ensure you have administrative access to these devices.
Step 3: create VLANs
- Log in to the network device’s management interface.
- Navigate to the VLAN configuration section, often found in the device’s settings or administrative menu.
- Create new VLANs by specifying a unique VLAN ID and a meaningful name or description for each VLAN. VLAN IDs are typically numbers, and they should be unique for each VLAN on your network.
Step 4: assign ports to VLANs
- After creating VLANs, assign the relevant switch ports to each VLAN.
- Select the switch ports to be included in a particular VLAN and associate them with the corresponding VLAN ID.
- Save your changes to apply the configuration.
Step 5: configure trunk ports (if necessary)
If you’re using tag-based VLANs and need to connect switches to one another, configure trunk ports to carry tagged traffic between switches. Ensure that you define the same Native VLAN on interconnected devices to allow them to communicate properly.
Step 6: implement Inter-VLAN routing (if necessary)
To enable communication between different Virtual LANs, configure inter-VLAN routing on your router or Layer 3 switch. This involves creating sub-interfaces for each VLAN on the router and assigning IP addresses to them. Configure routing rules to direct traffic between these sub-interfaces.
Step 7: test and monitor
- Test the VLAN configuration to ensure that devices within the same VLAN can communicate and that traffic isolation is functioning as intended.
- Monitor the network and use tools like network management software to keep an eye on VLAN performance and address any issues that may arise.
Step 8: document your configuration
Maintain clear documentation of your VLAN configuration, including VLAN IDs, descriptions, assigned ports, and any relevant IP addresses. This documentation will be valuable for troubleshooting and future management.
Step 9: Regularly review and update
Periodically review your VLAN configuration to ensure it meets the evolving needs of your network. As your organization grows or changes, you may need to add, modify, or remove VLANs.
Example VLAN implementation (enterprise network segmentation)
In this example, we will demonstrate how to set up VLANs for network segmentation in a company. The company, Example Corporation, has three departments: Sales, Marketing, and Research & Development. They wish to segment their network to improve security and optimize network performance.
Step-by-step process:
Step 1: identify the VLAN requirements
- Determine the VLAN needs: Sales, Marketing, and Research & Development.
- Allocate unique VLAN IDs (e.g., VLAN 10, VLAN 20, VLAN 30) and assign descriptions to each VLAN.
Step 2: access network equipment
Log in to the company’s core switch, which is the central networking device that manages VLANs.
Step 3: create VLANs
- Navigate to the VLAN configuration section on the core switch.
- Create VLANs as follows:
- VLAN 10: Sales
- VLAN 20: Marketing
- VLAN 30: Research & Development
- Save your changes.
Step 4: assign ports to VLANs
- Associate the switch ports used by each department with their respective VLANs:
- Ports 1-12: Sales (VLAN 10)
- Ports 13-24: Marketing (VLAN 20)
- Ports 25-36: Research & Development (VLAN 30)
- Save your changes.
Step 5: configure trunk ports (if necessary)
- If you have multiple switches and need to connect them, configure trunk ports to carry tagged traffic between switches.
- Ensure that the Native VLAN is consistent on all interconnected devices.
Step 6: implement inter-VLAN routing (if necessary)
- On your router or Layer 3 switch, create sub-interfaces for each VLAN.
- Assign IP addresses to these sub-interfaces, e.g., 192.168.10.1 for Sales, 192.168.20.1 for Marketing, and 192.168.30.1 for Research & Development.
- Configure routing rules to enable traffic between these sub-interfaces.
Step 7: test and monitor
- Verify that devices within the same department’s VLAN can communicate but are isolated from other VLANs.
- Monitor network performance and ensure that each VLAN operates efficiently without interference.
Demonstrating VLAN isolation and efficiency
To demonstrate how VLANs isolate traffic and enhance network efficiency:
Connect a device from the Sales department to a port within VLAN 10, and another device from the Marketing department to a port in VLAN 20. Attempt to communicate between these devices, and you’ll notice successful communication within the same VLAN while traffic between VLANs is blocked, illustrating the isolation provided by VLANs.
Generate heavy network traffic on one VLAN (e.g., Marketing). Observe that this traffic does not affect devices in the other VLANs, showcasing how VLANs minimize broadcast domains and prevent congestion.
If inter-VLAN routing is configured, verify that you can access the VLAN router’s sub-interfaces (e.g., 192.168.10.1, 192.168.20.1) from devices within the respective VLANs, highlighting the ability to route traffic between VLANs when necessary.
By implementing VLANs as described in this scenario, the sysadmins at Example Corporation can significantly improve the security and efficiency of their network, ensuring that each department’s traffic remains segregated and that network performance is optimized, contributing to a more robust and organized network infrastructure.
NinjaOne offers powerful endpoint management to keep your segmented networks secure, efficient, and easy to monitor.
Take full control of IT with NinjaOne
NinjaOne, a comprehensive remote monitoring and management platform, plays a crucial role in simplifying and optimizing the utilization of Virtual Local Area Networks (VLANs).
By seamlessly integrating with VLAN configurations, NinjaOne grants network administrators granular insights into the performance and security of each VLAN. It provides a centralized view of VLAN traffic, facilitating the identification of issues and bottlenecks within different virtual networks. Using NinjaOne’s monitoring and alerting capabilities, IT administrators can proactively address any anomalies or security breaches in VLANs, ensuring the continued integrity of the network.
NinjaOne also simplifies the task of VLAN administration by providing a user-friendly interface for configuring, managing, and scaling VLANs, making it an invaluable tool for organizations seeking to harness the full potential of VLAN technology while maintaining optimal network performance and security.
If you’re ready to try NinjaOne for yourself, schedule a Demo or Start Your 14-day Trial and see why so many organizations and MSPs choose Ninja as their RMM partner!
Just looking for more hot tips and comprehensive guides? Check our blog often, and be sure to sign up for MSP Bento to have great info, interviews, and inspiration delivered directly to your inbox!