Importance of Inventory Scanning
Inventory scanning is a critical component of network management, serving as the foundation for ensuring that all devices connected to a network are accounted for and properly managed.
By conducting regular inventory scans, IT professionals can obtain a comprehensive overview of the network’s assets, including computers, servers, mobile devices, and software applications. This visibility is essential for maintaining operational efficiency, as it allows for the effective allocation of resources, timely updates, and the identification of unauthorized devices that may pose security risks.
Moreover, inventory scanning plays a pivotal role in network security by identifying all devices connected to the network, including unauthorized or rogue devices. IT administrators can ensure that all devices are properly configured with up-to-date security patches and antivirus software, mitigating the risk of security breaches arising from outdated or unpatched software.
Regular inventory scanning also facilitates compliance with regulatory requirements by providing documentation of software usage and configurations.
Furthermore, inventory scanning facilitates compliance with various regulatory standards that mandate the management and protection of sensitive data. By having a clear understanding of where data resides within the network and which systems have access to it, organizations can implement appropriate controls to safeguard this information.
Regular inventory scans help ensure that all assets are compliant with industry regulations, which is vital for avoiding legal penalties and maintaining the trust of customers and partners.
In conclusion, investing in robust inventory scanning tools and practices is essential for organizations seeking to maintain a secure, efficient, and resilient network environment.
How does Inventory scanning work?
Inventory scanning is based on network scanning, which is a technique that sweeps all possible hosts within a network for ping responses, ARP scans, and port scans. Since the possible number of hosts that can fit within a network is large, an automatic scanning tool is usually used. Scanning tools can be agent-based or agentless. The scan tool scans and discovers active hosts and services that appear as a result of the scan. IT administrators make decisions based on these results.
Does NinjaOne have an Inventory Scanning tool?
Yes, NinjaOne has an Inventory Scanning tool, as well as a Network Management Suite (NMS) agent that is installed on a Windows computer within the network. The agent features a monitoring tool that communicates with the endpoints and reports their status to the NinjaOne application.
As a prerequisite for running the Inventory scanning tool, you must select one Windows computer in your network to serve as the NMS monitoring server. Once new endpoints are detected and added as NMS devices, they can be monitored by this server. The selected computer must have the NinjaOne agent installed and should be visible in the organization and location within the monitored network.
What are NMS devices?
NMS devices are endpoints, but they don´t fall into the categories of computer, server, or mobile devices. Examples of NMS devices are network printers, switches, routers, storage devices, such as JBODs or NAS, among others. Ideally these devices need to be monitored for health status like computers.
Since agents cannot be installed on these devices, a dedicated device takes care of the monitoring within the network and the monitoring is done using protocols such as ICMP, SNMP, SSH, Telnet, etc. NinjaOne can monitor NMS devices and send alerts when issues are detected.
How can I add NMS devices to my organization in NinjaOne?
Follow the instructions below to install the NMS agent and run the discovery job.
1. Run the discovery job and install the NMS agent.
a) From any NinjaOne dashboard, click the + sign in the top right corner of the screen. A drop-down menu will appear.
b) From the drop-down menu, select Device, then select Run Ad Hoc Network Discovery. A dialog box will appear (see below screenshot for reference).
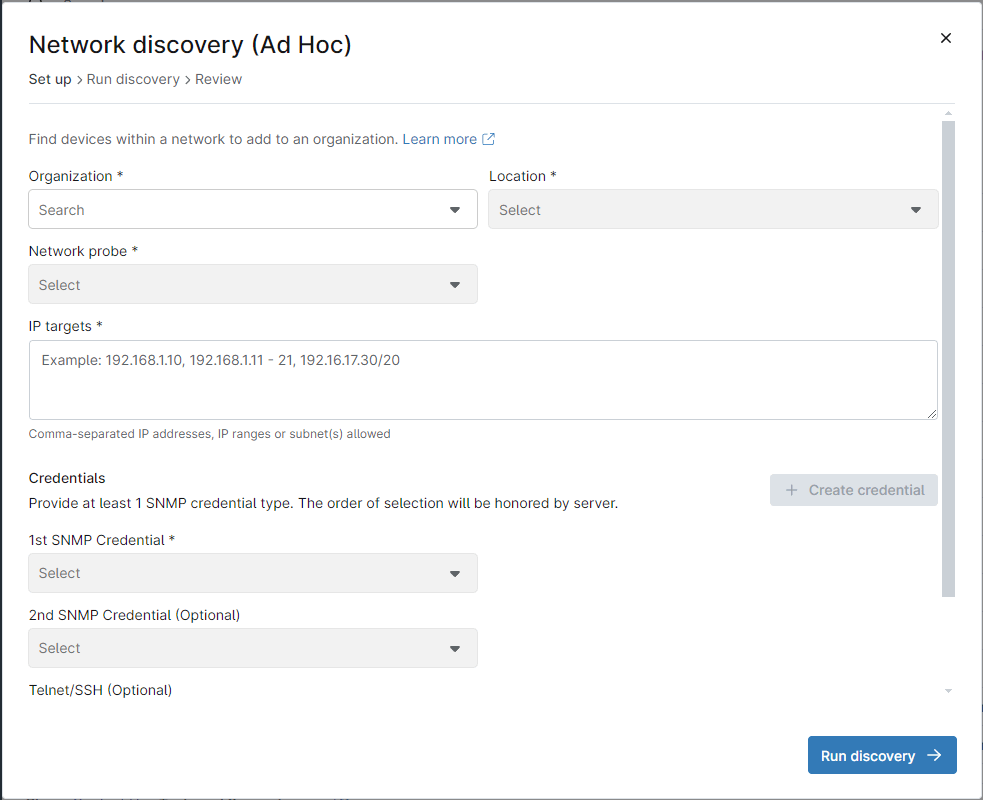
c) Fill out the Organization and Location.
d) Under Network Probe, select the designated computer that will act as the NMS monitoring server.
e) Select the IP targets (the IP ranges to scan for NMS devices).
f) Under credentials, select the credentials that will be used by the SNMP protocol.
g) If no credentials have been defined yet, click + Create credential to define new ones.
h) Optionally you can enter Telnet/SSH credentials.
i) Optionally, you can click Advanced settings to modify the ping timeout, ping packet TTL, number of pings per node and delay between pings.
j) Click Run discovery. At this time, the NMS agent will be silently installed on the NMS monitoring server and the discovery job will be run.
k) fter some minutes, the discovery job will finish showing the discovered devices. Devices that NinjaOne recognizes as already part of the organization will be grayed out to avoid being added twice.
l) Select the devices you want to add and click Review.
m) Review the devices to add, making sure these are the ones you want to add, select each of them using the checkmark and click Edit. Give the device a name and role (see screenshot below for reference).
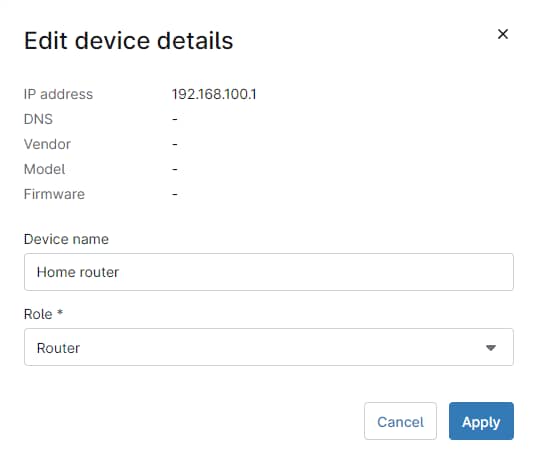
n) Click Finish and confirm.
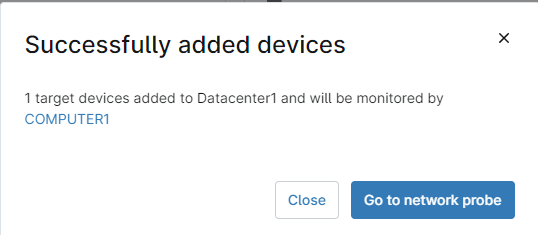
o) You will see a notice saying that your devices have been successfully added, along with the name of the NMS monitoring server name (see screenshot below for reference).
What kind of devices can be discovered and monitored with the NinjaOne NMS agent?
The NMS agent can discover and monitor mobile devices, computers, printers, JBODs, managed switches, routers, any device with network access that responds to ICMP (ping).
More monitoring options can be obtained if the device has SNMP capabilities, for instance, an SNMP enabled JBOD device can be monitored for temperature, drives, fans, and other parameters available through SNMP.
Telnet and SSH are other protocols available in the NinjaOne NMS agent, they are used to monitor the availability of connection-based TCP/IP applications.