NinjaOne BitLocker/FileVault Encryption Key Management
Managing encryption keys is a critical aspect of maintaining data security across an organization’s IT infrastructure. NinjaOne’s BitLocker and FileVault encryption management solution simplifies the process of monitoring and managing disk encryption for Windows and Mac devices. By integrating directly with BitLocker on Windows and FileVault on Mac, NinjaOne provides IT administrators with a centralized platform to oversee encryption status, enforce encryption policies, and securely manage recovery keys.
How to Manage Encryption Keys with NinjaOne
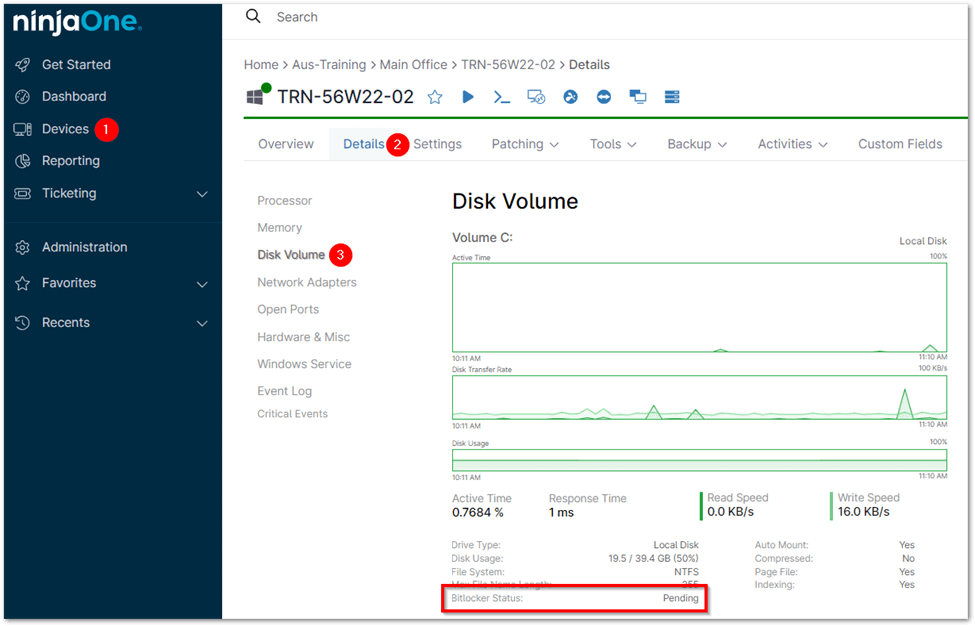
Verify the BitLocker Status on a Windows Device
1. Go to the device dashboard in NinjaOne.
2. Click on the Details tab.
3. From the left-hand menu, choose Disk Volume. Here, you will see the BitLocker status for each volume.
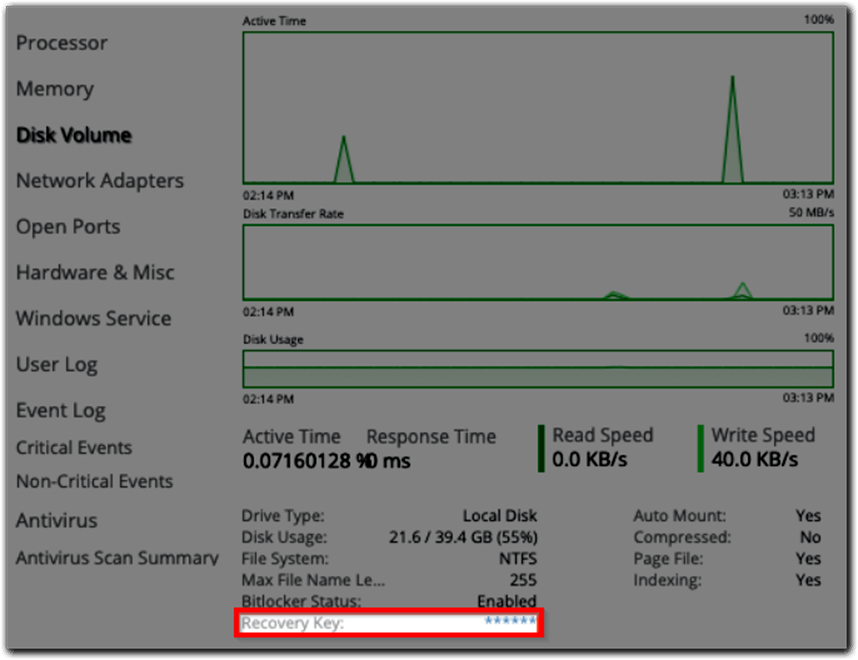
4. If BitLocker is enabled, select the starred hyperlink next to Recovery Key to view the recovery key. You can also copy the recovery key to your clipboard from this location.
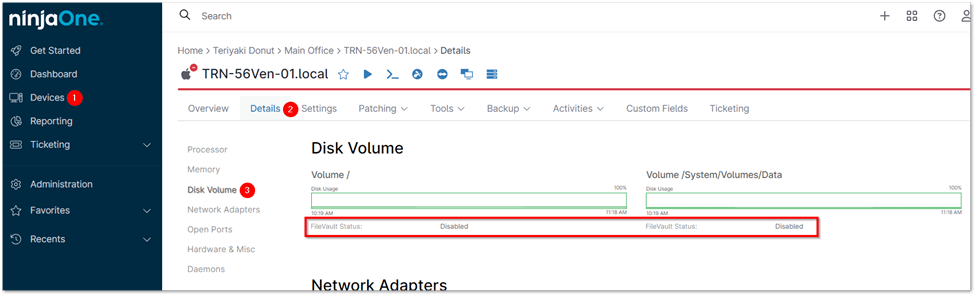
Verify the FileVault Status for a Mac
1. Go to the device dashboard in NinjaOne.
2. Click on the Details tab.
3. Select Disk Volume from the left-hand menu. The FileVault status for each volume will be displayed.
Note: Currently, if the customer stores their BitLocker key in TPM, it cannot be displayed in NinjaOne.
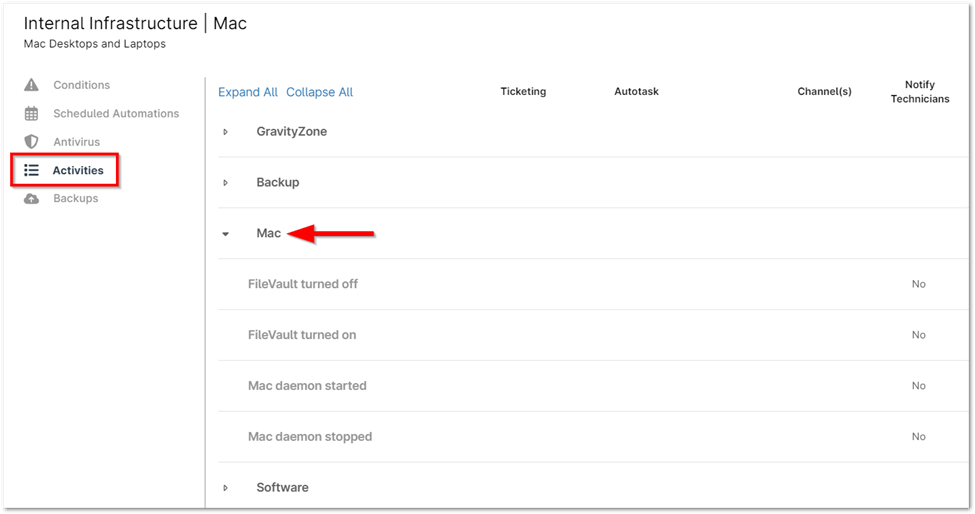
Activate Notifications for BitLocker/FileVault Status Updates
1. Go to the policy editor by navigating to Administration > Policies for the specific policy where you want to enable BitLocker or FileVault activity notifications, and then open the Activities tab.
2. Depending on the policy editor opened (either for Windows or Mac), expand the relevant dropdown menu.
3. Select the BitLocker or FileVault activity for which you want to enable notifications. The Activity configuration modal will appear.
4. Use the dropdown options to configure the notification settings.
Benefits of NinjaOne’s BitLocker and FileVault Encryption Management
- Centralized Monitoring: View encryption status for both Windows (BitLocker) and Mac (FileVault) devices from a single NinjaOne console, streamlining management and oversight.
- Enhanced Security Compliance: Ensure that all devices comply with encryption policies, reducing risk and meeting security standards.
- Simplified Management: Efficiently manage and audit encryption settings and statuses across your entire fleet of devices without needing to access each device individually.
Encryption key management best practices and strategies
- Centralized Control: Centralized key management systems offer a single point of control, streamlining oversight and reducing the chance of human error.
- Implement Key Rotation: Regular key rotation minimizes the potential damage of a compromised key, as its lifespan and usage are limited.
- Restrict Key Access: Access controls ensure that only authorized individuals can interact with keys, reducing internal threats.
- Monitor Key Usage: Tracking key access and usage patterns helps identify unusual activity that may signal unauthorized use or a potential breach.
- Backup Recovery Keys: Securely storing backup keys offsite guarantees data accessibility even if the primary system or location is compromised.
Example Use Cases
- Device Decommissioning: Safely manage and revoke encryption keys when decommissioning or disposing of old devices to prevent unauthorized access to data.
- Compliance Audit: Demonstrate adherence to data protection regulations with detailed key management reports.
- Data Breach: Minimize the impact of a data breach by ensuring only authorized parties can access sensitive information.