Integrating CrowdStrike with NinjaOne enhances endpoint security by combining the robust threat detection and response capabilities of CrowdStrike with the comprehensive device management features of NinjaOne. This CrowdStrike integration with NinjaOne ensures that IT administrators have a centralized platform for managing security incidents and maintaining device health. By learning how to connect CrowdStrike with NinjaOne, organizations can streamline their security operations, reduce response times, and enhance overall endpoint security posture.
How to Connect CrowdStrike With NinjaOne
Enabling CrowdStrike Integration in NinjaOne
CrowdStrike integrations can be seamlessly enabled within the NinjaOne administration interface using an API token from CrowdStrike. This process allows you to bring your own CrowdStrike license to NinjaOne. Follow the steps below to configure the integration:
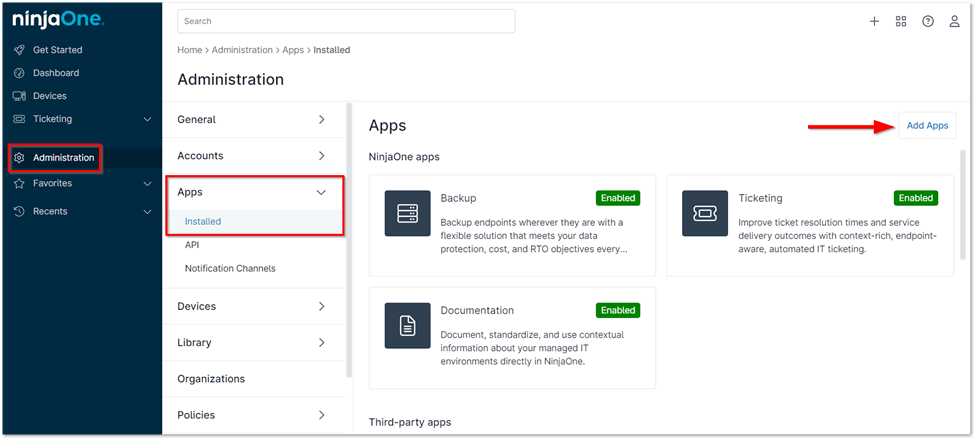
1. Navigate to Administration:
- Go to Administration > Apps and click Add Apps.
- From the list of available third-party apps, select CrowdStrike.
2. Enable the Integration:
- Click Enable.
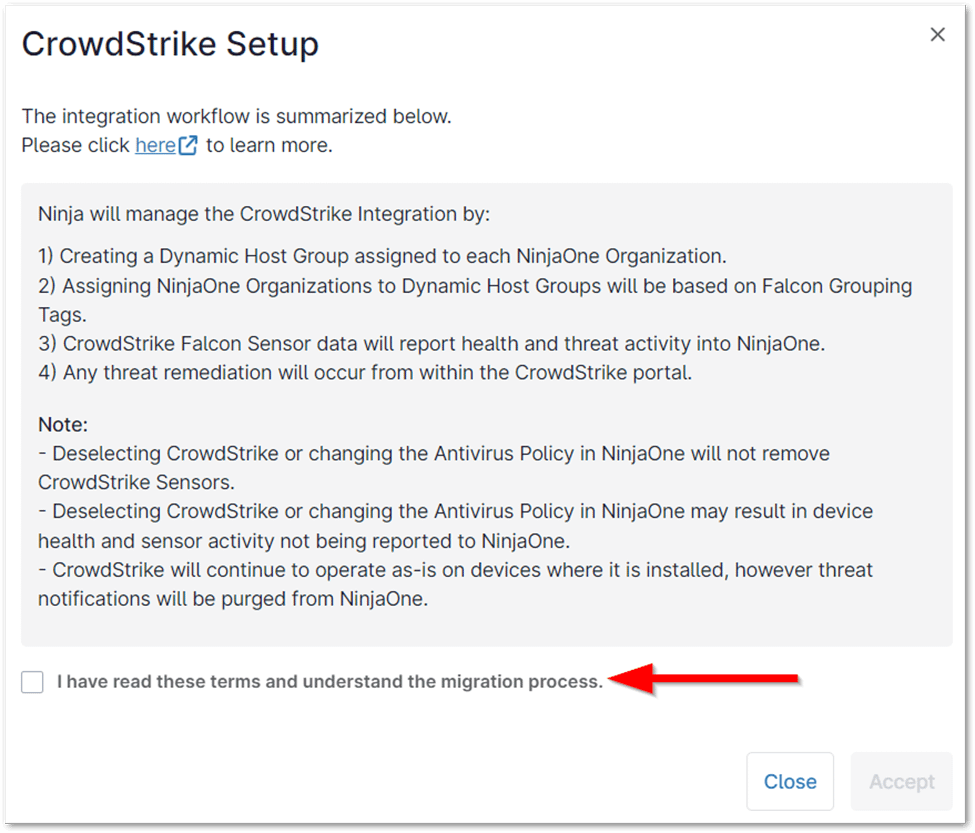
3. Accept Terms and Conditions:
- Carefully read the terms outlining the migration process in the CrowdStrike Setup popup window.
- Activate the checkbox at the bottom of the page to enable the Accept button.
4. Obtain CrowdStrike API Token:
- Go to https://falcon.{domain}.crowdstrike.com/support/api-clients-and-keys (note: the base URL will vary based on your geo-location or cloud license).
- Select an existing API client or create a new one. If you have forgotten your client secret, you can reset it from this page.
- Enter the required details to confirm your API client and provision your API scopes.
5. Finalize Integration:
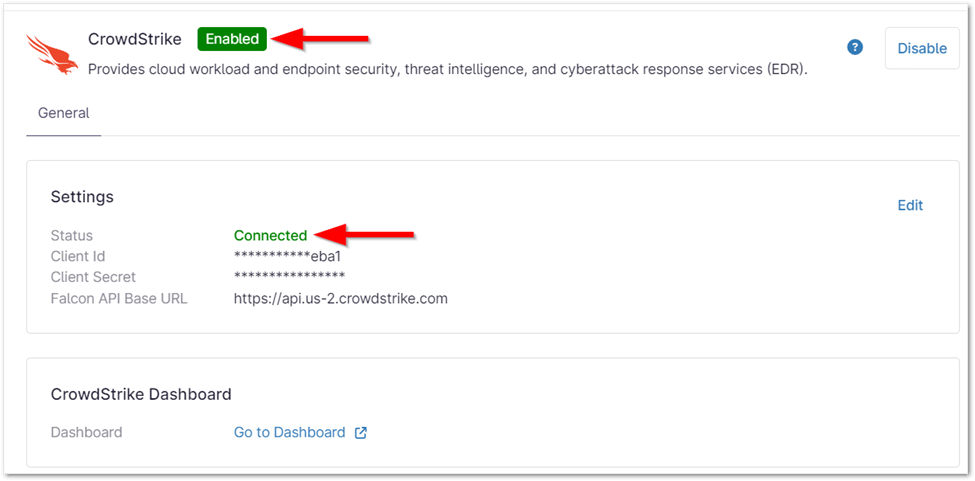
- Click Enable.
Your CrowdStrike status should now display as Enabled and Connected.
Deploying CrowdStrike at The Policy Level in NinjaOne
1. Policy Selection or Creation:
- Navigate to Administration > Policies within the NinjaOne console.
- Choose the existing policy you wish to modify or create a new policy to apply the CrowdStrike configuration.
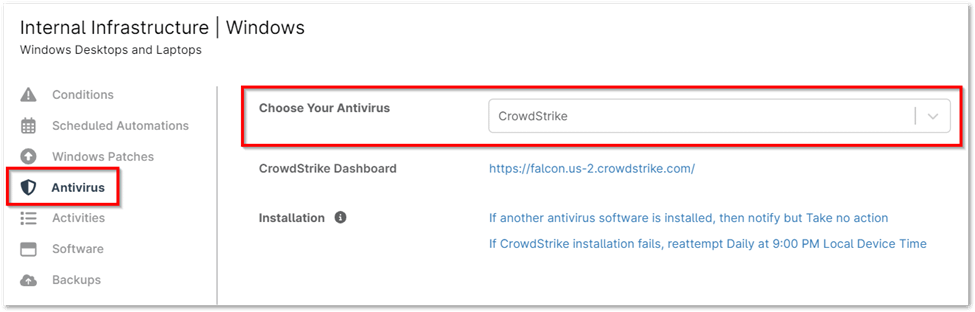
2. Endpoint Protection Configuration:
- Open the Antivirus tab within the selected policy.
- From the dropdown menu, select CrowdStrike. If another antivirus solution is currently active, first select Disabled before choosing CrowdStrike.
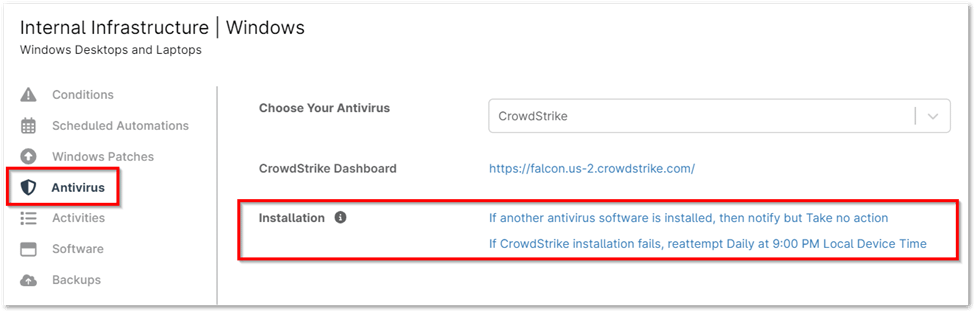
3. Click the two options adjacent to Installation to configure the installation settings:
- If another antivirus software is installed, then notify and: Select whether you want to proceed with installation or take no action.
- If CrowdStrike installation fails, reattempt Daily at 9:00 PM Local Device.
4. Save Changes:
- Click Save to apply the CrowdStrike antivirus configuration to the selected policy.
The Benefits of Using NinjaOne For CrowdStrike Integration
- Unified Visibility: See CrowdStrike security alerts and device status directly within your NinjaOne dashboard.
- Close the threat alert loop: CrowdStrike threats trigger immediate quarantine and NinjaOne alerts, enabling swift response and automatic closure of the threat loop within a unified workflow.
- Enhanced Reporting: Combine security and IT operations data to gain deeper insights into your environment.
- Automation: Save time and reduce manual effort with automated workflows.
Strategies For Maximizing CrowdStrike And NinjaOne Integration
- Prioritize Critical Alerts: Focus on the most severe threats first and create automated responses for them.
- Leverage Asset Management: Use NinjaOne’s asset inventory to ensure all devices have the CrowdStrike agent installed and updated.
- Regular Review: Continuously monitor the integration’s performance and adjust your settings as needed.
- Utilize CrowdStrike Connect to Host Button: The “Connect to Host” button allows you to remotely connect and take action, streamlining troubleshooting and remediation.
Example Use Cases
- Rapid Incident Response: As CrowdStrike Falcon detects and isolates threats, alerts are instantly sent to the NinjaOne console, triggering notifications via SMS, Teams, Slack, email, or PagerDuty to ensure a rapid response.
- Compliance Reporting: Generate reports that show which devices are compliant with security policies, based on CrowdStrike data.