NinjaOne Linux Policy
NinjaOne emerges as a powerful solution for organizations seeking to streamline and centralize their endpoint management processes. Among its many capabilities, NinjaOne’s Linux policy management feature plays a crucial role in enabling IT administrators to effectively monitor, manage, and secure their Linux endpoints at scale.
This article explores the intricacies of NinjaOne’s Linux policies, examining their significance, configuration, benefits, and strategies for optimal implementation.
How to Create or Edit a NinjaOne Linux Policy
These steps will guide you in either creating a new policy or editing an existing one within NinjaOne’s policy management interface:
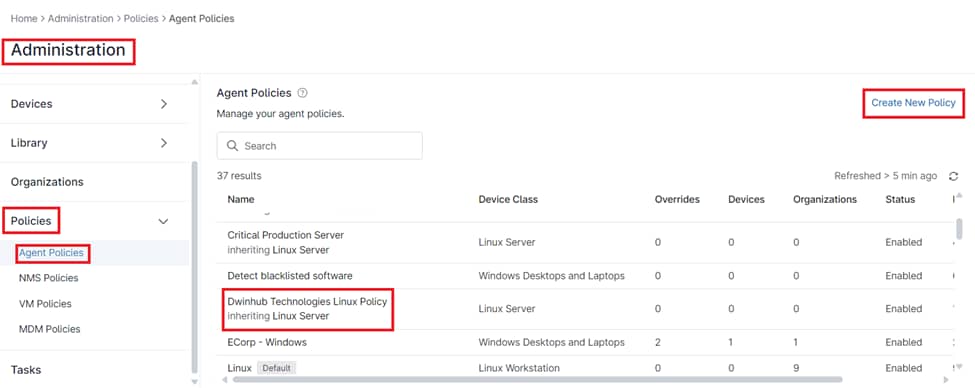
1. Access the “Administration” Section:
- From the NinjaOne dashboard, navigate to the left-hand sidebar.
- Click on “Administration” to expand the options under this section.
2. Navigate to “Policies”:
- Under the Administration section, locate and click on “Policies” to reveal the different policy categories.
3. Select “Agent Policies”:
- Click on “Agent Policies” from the list of policy categories. This will display the list of all existing agent policies on the right-hand side.
4. Create or Edit a Policy:
- To create a new Linux policy, click on the “Create New Policy” button located at the top-right corner of the Agent Policies page.
- To edit an existing Linux policy, locate the desired policy from the list and click on it.
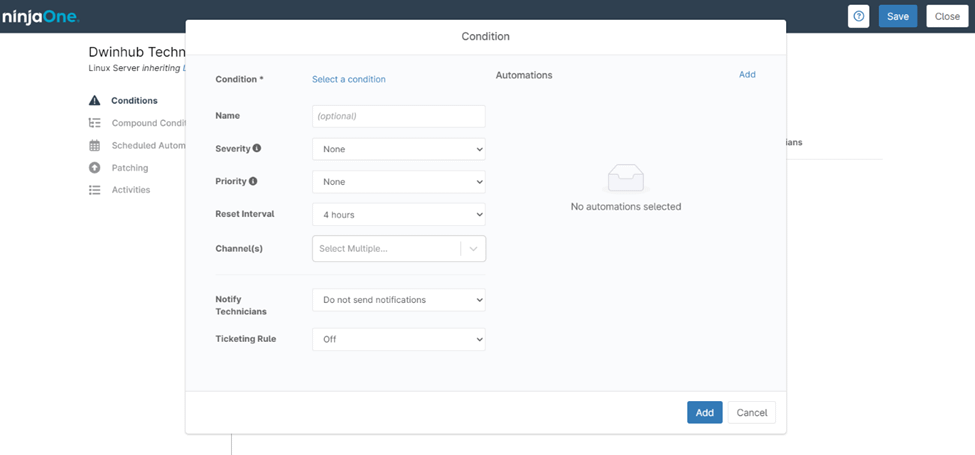
Configurable Options for NinjaOne Linux Policy Conditions
When configuring a condition within a NinjaOne Linux Policy, the following options are available:
- Condition: Select the specific system metric or event that will trigger the condition, such as CPU usage, disk space thresholds, or other relevant criteria.
- Name: Provide an optional descriptive name for the condition to easily identify it within the policy.
- Severity: Choose the severity level associated with this condition, ranging from none to high. This setting helps categorize the urgency and potential impact of the condition.
- Priority: Set the priority level, which indicates the importance of the condition relative to others, guiding how quickly it should be addressed.
- Reset Interval: Define the time interval after which the condition will reset if it is no longer met.
- Channel(s): Select one or more communication channels (e.g., email, SMS) where notifications will be sent if the condition is triggered.
- Notify Technicians: Decide whether to send notifications to technicians when the condition occurs. This option can be customized to fit your notification preferences.
- Ticketing Rule: Specify whether a ticket should be automatically generated when the condition is met. This can be set to off if no ticket creation is required.
- Automations: You can configure specific automations to execute automatically when the condition is triggered. These automations might include running scripts, restarting services, or performing other predefined actions to remediate or respond to the condition. Automations are configured by clicking “Add” in the “Automations” section, where you can define the exact response actions tied to the condition.
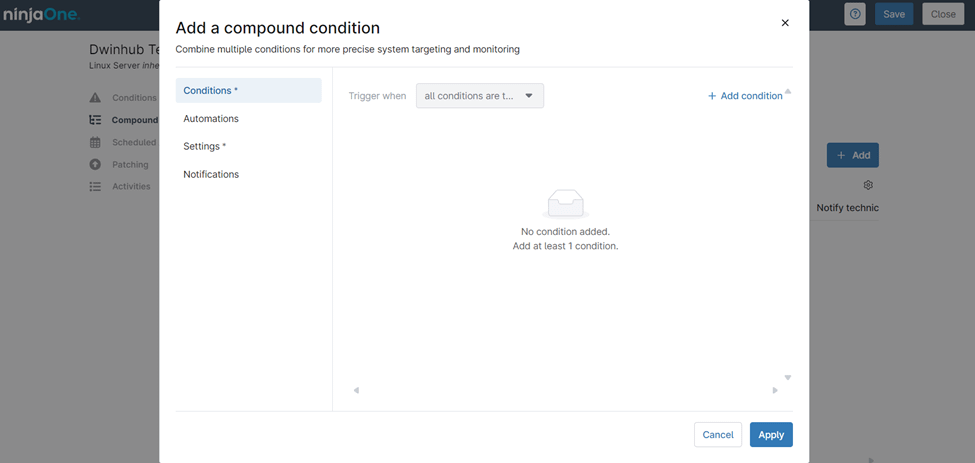
Configurable Options for NinjaOne Linux Policy Compound Conditions
When setting up a compound condition in a NinjaOne Linux Policy, you have several configuration options to tailor the monitoring and response:
- Conditions: Start by adding one or more individual conditions. These can be any of the predefined conditions available in NinjaOne, such as thresholds for CPU usage, memory consumption, disk space, or other system metrics. Compound conditions allow you to combine multiple conditions for more precise monitoring.
- Trigger When: Choose the logic that determines when the compound condition is met.
- Automations: Configure automations that will execute when the compound condition is triggered. These automations can include running scripts, restarting services, sending notifications, or any other predefined actions aimed at responding to the condition. Automations are added by selecting the “Automations” tab and configuring the desired actions.
- Settings: Customize additional settings for the compound condition, such as defining how frequently the condition should be evaluated or other advanced options that refine how the condition operates.
- Notifications: Specify how and where notifications should be sent when the compound condition is met. This could include email alerts, SMS notifications, or other communication channels, ensuring that the appropriate personnel are informed.
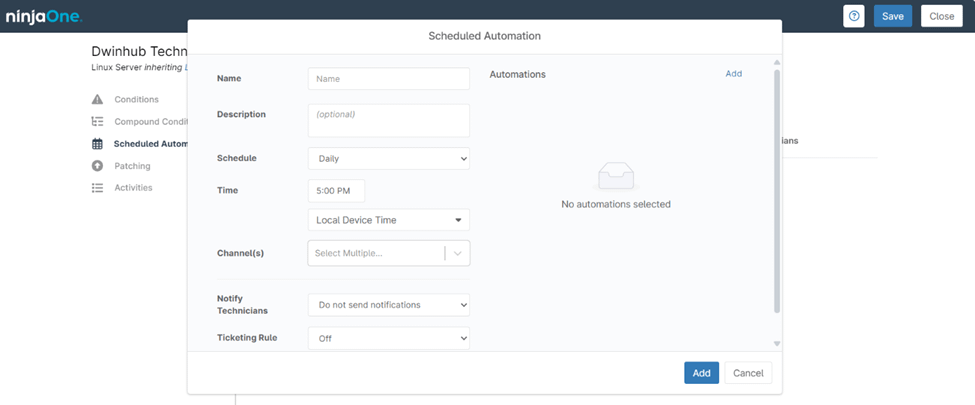
Configurable Options for NinjaOne Linux Policy Scheduled Automations
When setting up a scheduled automation within a NinjaOne Linux Policy, you can configure the following options:
- Name: Assign a unique name to the scheduled automation for easy identification and reference within the policy.
- Description: Provide a detailed description of the automation, explaining its purpose and what actions it will perform.
- Schedule: Define the frequency of the automation, such as daily, weekly, or monthly, and specify which days it should run.
- Time: Set the exact time of day when the automation should be executed, ensuring it runs during the optimal time window for your environment.
- Channel: Select one or more communication channels through which notifications or alerts related to the automation will be sent.
- Notify Technicians: Choose whether to notify technicians when the automation runs, helping them stay informed about the actions being performed on managed devices.
- Ticketing Rule: Determine if a ticket should be created automatically when the automation runs, and configure the associated rules to manage these tickets.
- Automations: Select the specific automation script or action to be executed according to the configured schedule.
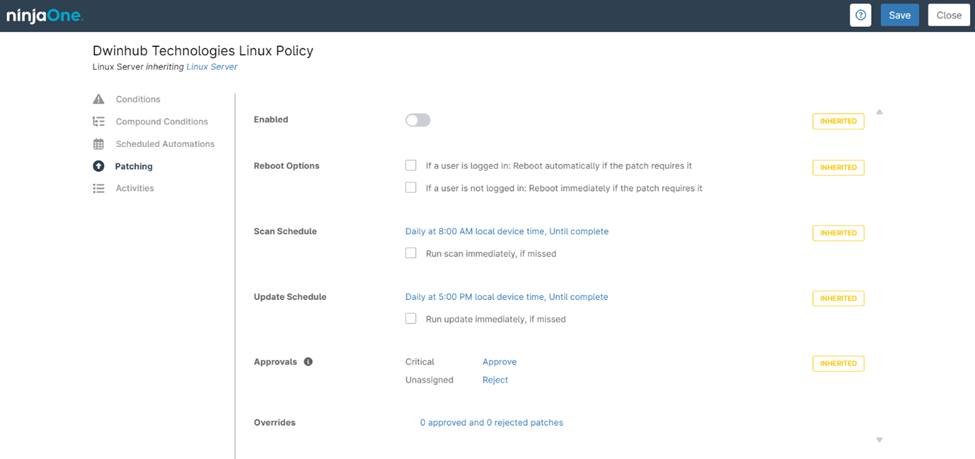
Configurable Options for a NinjaOne Linux Policy Patching
When configuring patch management within a NinjaOne Linux Policy, you have the following options to control how patches are handled on your Linux systems:
- Enabled: Toggle the entire patching functionality on or off for this policy.
- Reboot Options: Configure how the system handles reboots when required by a patch, with options to automate reboots based on user login status.
- Scan Schedule: Define the frequency and timing for scanning for new patches and an option for immediate scans if a scheduled scan is missed.
- Update Schedule: Set the schedule for applying approved patches and an option for immediate updates if a scheduled update is missed.
- Approvals: Control the automatic approval or rejection of patches based on their criticality, with separate settings for critical and unassigned patches.
- Overrides: Display the count of patches that have been manually approved or rejected, overriding any automatic approval or rejection settings.
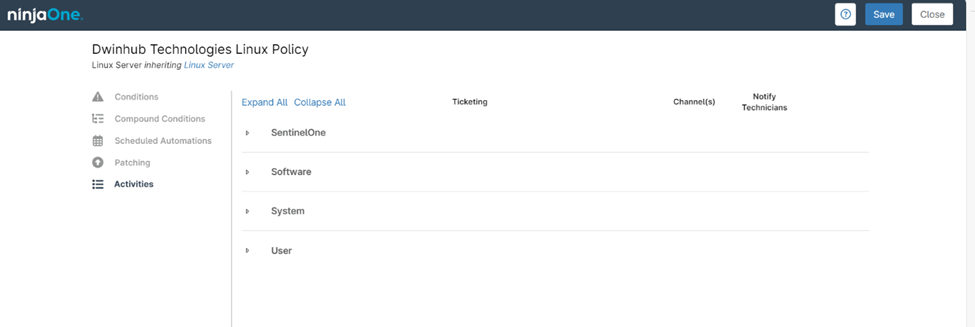
Configurable Options for a NinjaOne Linux Policy Activities
When configuring activity monitoring and alerts within a NinjaOne Linux Policy, you can define conditions and actions related to the following areas:
- Software: Set up notifications and tickets for software added or removed events.
- System: Configure alerts and tickets for system events like processes started/stopped or system reboots.
- User: Create notifications and tickets based on user activities such as account added/removed or login/logout.
Benefits of Using NinjaOne for Linux Policy Management
NinjaOne’s Linux policy management feature offers several key advantages:
- Centralized Management: Manage your Linux endpoints from a single pane of glass, reducing complexity and improving efficiency.
- Scalability: Effortlessly scale your Linux management operations as your organization grows.
- Automation: Automate routine tasks like patching, software deployment, and security configuration, freeing up IT resources for more strategic initiatives.
- Enhanced Security: Harden your Linux endpoints against cyber threats with robust security policies and proactive monitoring.
- Improved Compliance: Ensure compliance with internal and external regulations by enforcing consistent configurations across your Linux environment.
Strategies for Effective Linux Policy Management with NinjaOne
To maximize the benefits of NinjaOne’s Linux policies, consider the following strategies:
- Group-Based Policies: Utilize group-based policies to apply configurations to multiple Linux endpoints simultaneously, saving time and effort.
- Role-Based Access Control: Implement role-based access control to restrict policy management capabilities to authorized personnel.
- Regular Policy Reviews: Regularly review and update your Linux policies to ensure they remain aligned with your evolving security and management requirements.
- Testing and Validation: Thoroughly test and validate new policies in a controlled environment before deploying them to production endpoints.