iOS Policies
iOS policies in NinjaOne refer to the policies specific to Apple devices using the iOS operating system, like iPhone devices. iOS policies in an MDM (Mobile Device Management) system are crucial because they ensure that devices are configured and managed according to Apple’s guidelines and security standards. These policies help maintain device integrity, enforce security protocols, and provide seamless integration with Apple services.
They also enable IT administrators to control device features, manage app distribution, and protect sensitive data. Ultimately, these policies enhance user experience and operational efficiency within organizations using Apple devices.
What can be configured using iOS policies NinjaOne?
iOS policies have six categories: Passcode, Restrictions, Applications and Network.
Let´s explain each of them below.
1. Passcode
This category defines the phone password settings. If enabled, the password is enforced according to the settings.
| Setting | Definition |
| Require alphanumeric value | Enforces use of both numbers (123) and alphabetical characters (Abc). |
| Allow simple passcode | A simple passcode contains repeated characters or increasing/decreasing characters (123 or CBA). |
| Maximum number of failed attempts | The number of allowed failed attempts when entering the passcode at the device’s lock screen. After six failed attempts, a time delay is imposed before a passcode can be entered again. The delay increases with each attempt. If a user’s failed attempts exceed the number set in the policy, then the device will be wiped. |
| Maximum passcode age (days) | The number of days for which the passcode can remain unchanged. After this number of days, the user is required to change the passcode before the device is unlocked. If set to zero (0), then the passcode will not time out. This property is ignored for User Enrollments. |
| Maximum grace period for device lock | The period to unlock the phone without entering a passcode. When the grace period expires, the device is auto locked by the system and the user will be prompted to enter their passcode. |
| Minimum number of complex characters | A complex (or ‘special’) character is a character other than a number or a letter, such as & % $ #. This property is ignored for User Enrollments. |
| Minimum passcode length | This parameter is independent of the optional ‘Minimum number of complex characters’ setting. |
| Passcode history | The number set here defines the number of passcode entries that can be applied before a new, unique passcode must be created. For example, if this requirement is set to “3” then a user can reset their password to something they used in the past up to three times before they need to apply different characters. |
| Maximum auto-lock | The number of minutes for which the device can be idle before it gets locked by the system. When this limit is reached, the device is locked, and the passcode must be entered. The user can edit this setting on their device, but the value cannot exceed the policy setting. |
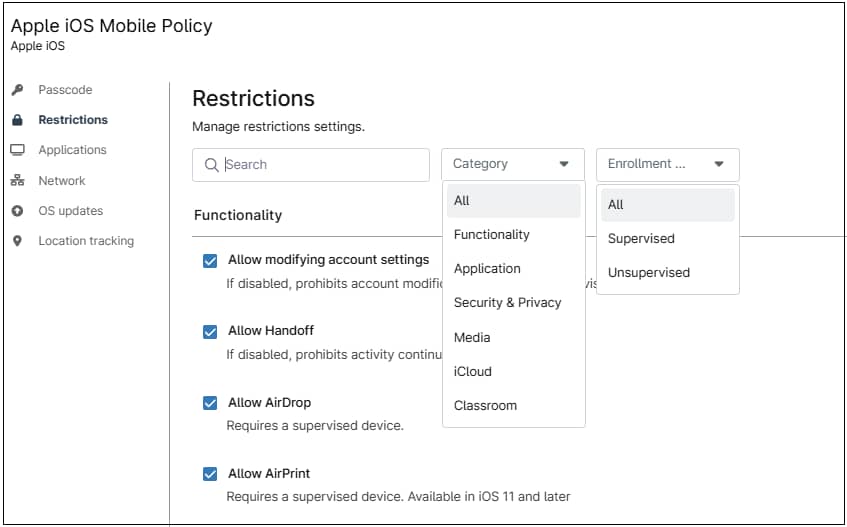
2. Restrictions
This category has over 100 phone settings that can be enabled or disabled. The settings are divided into 6 categories: Functionality, Application, Security & Privacy, Media, iCloud, and Classroom. Some of these settings are exclusive to iOS Supervised mode and some are for Unsupervised mode. The policy editor allows you to view only the settings for a chosen category or all settings. The editor also allows you to view only the settings that apply for Supervised, Unsupervised, or All. There is also a search option to make it easier to find a setting. See the screenshot below for reference.
Only values modified from their default setting will be delivered to a device. The default values in a policy represent how a device behaves without any MDM policy enabled.
If the device was enrolled with a work profile, the restrictions will be applied to only the work profile.
Consult the iOS policies section of the NinjaOne MDM Setup guide for a detailed description of each restriction.
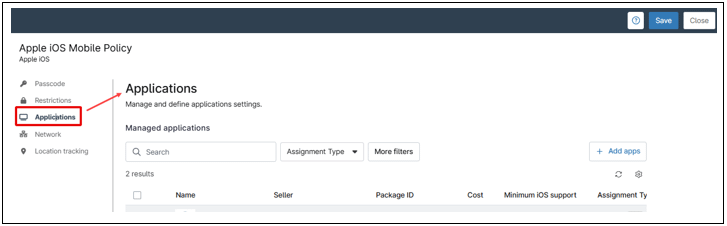
3. Applications
This category controls which apps are available to end users, and which apps are blocked from use. In addition, NinjaOne’s MDM supports apps assigned through Apple’s App and Books feature – formerly Volume Purchase Program (VPP). Apple Business Manager (ABM) content tokens are supported per organization/location, and provide information related to the token, assigned apps, and licenses from the MDM Configuration page in NinjaOne. To learn more about Apple’s Apps and Books, consult the Buying content through apps and books tutorial.
Follow the steps below to add and configure apps in a policy.
a. Click + Add apps.
b. Switch between the Apps and Books and Public App Store tabs depending on the type of app you want to add. Please note that if you do not have your Apps and Books token set up you will not see any content under the Apps and Books tab.
c. Type the name of the app or the app’s publisher into the search field. If you’re unsure what to enter, you can simply type a single letter and then click Search. A list of matching applications will appear.
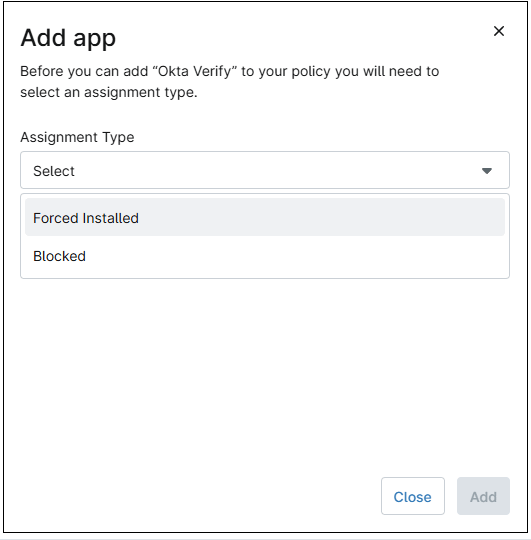
d. Click the desired application. A dialog box will appear.
e. Select the assignment type from the drop-down (force installed or blocked). Note that the Blocked assignment type is only supported on supervised devices.
f. If the selection was blocked, go to step eight.
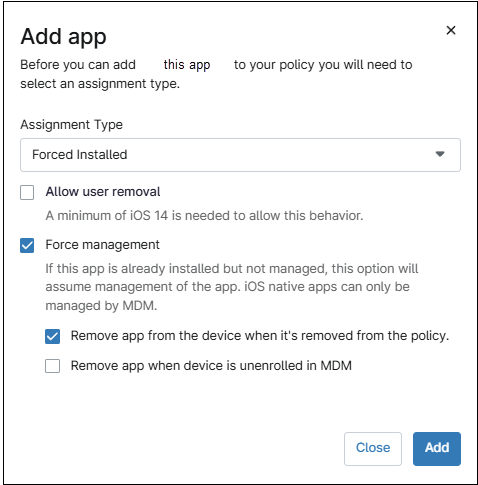
g. If the selection was Force Installed, fill out the remaining fields.
Note: If you opt to remove the app when a device is removed from a policy, this function also applies when you switch a device’s policy under the Settings tab on the device dashboard if the new policy does not also have the app included.
h. Click Add. You can continue adding applications, once you´re done,
i Click Save on the upper right side of the screen. Enter your MFA response method and close.
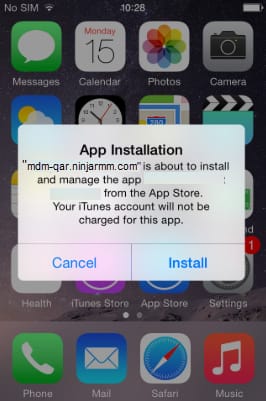
The app(s) will now appear under Managed Applications, displaying its details and assignment type. When the policy attempts to install an application via the Public App Store on company-supervised devices, or through any method on unsupervised devices, the end user receives a notification on their device. The user may need to sign in with an Apple ID and enter their password to complete the installation. Additionally, the user must select Install to proceed with the installation.
4. Network
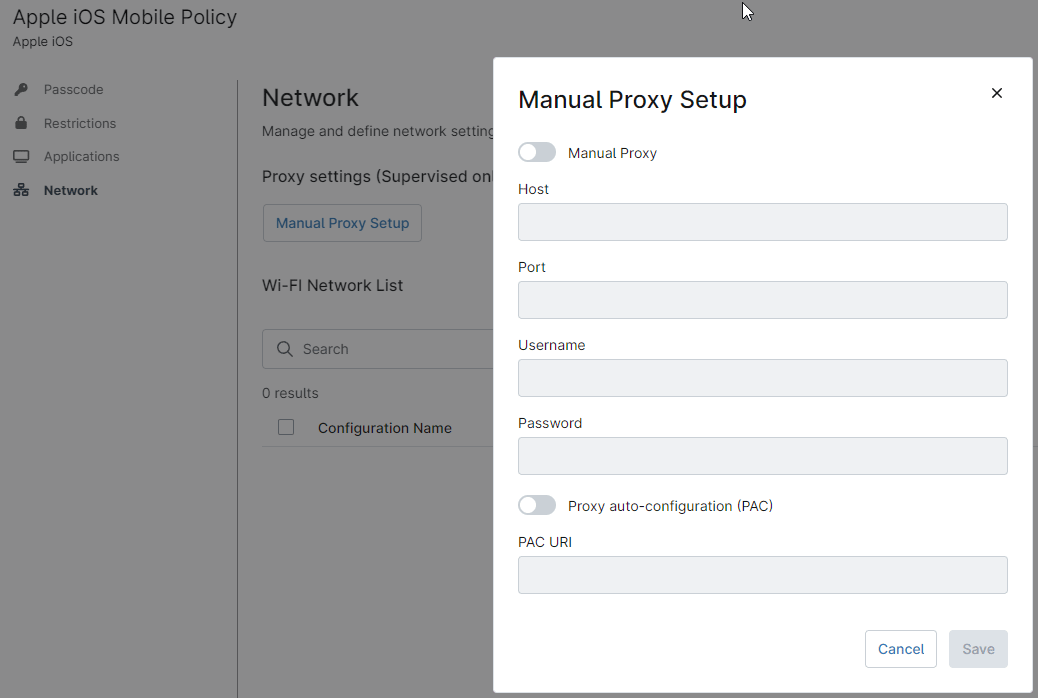
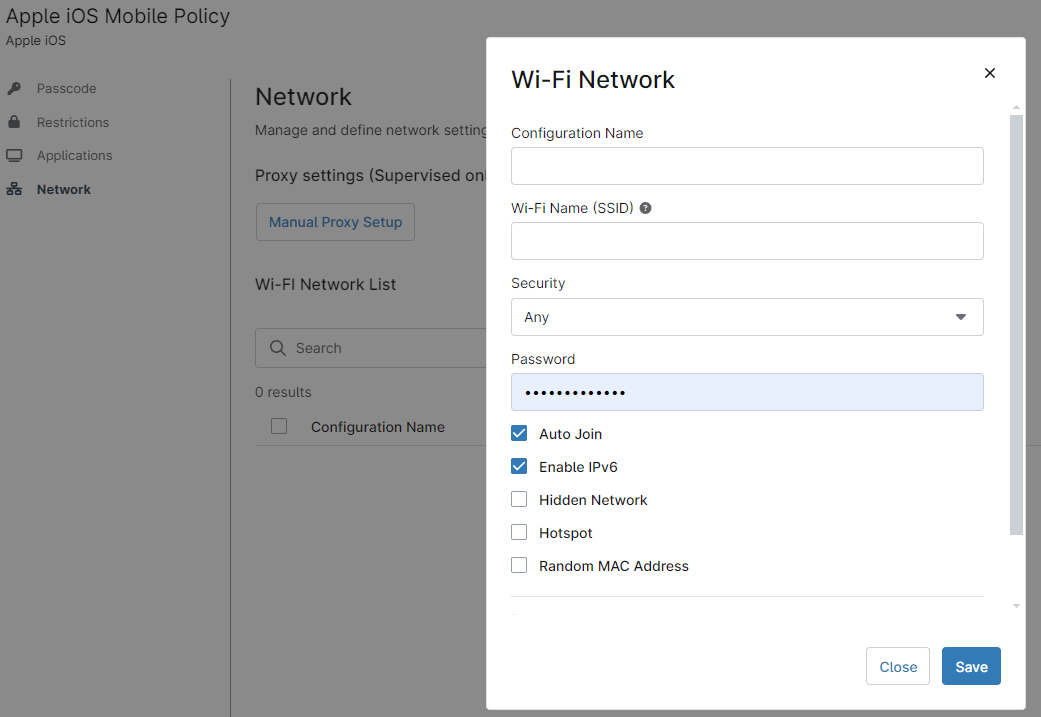
This category is for configuring proxy settings and Wi-Fi networks. You can add only one proxy, but multiple wi-fi networks. When any network is deleted from the policy, it will also be removed from the physical device.
For manual proxy settings, fill out the fields and click Save.
Notice that if a global proxy is configured, the user has the option to turn it off on the device.
For Wi-Fi network settings, fill out the required fields and click Save.
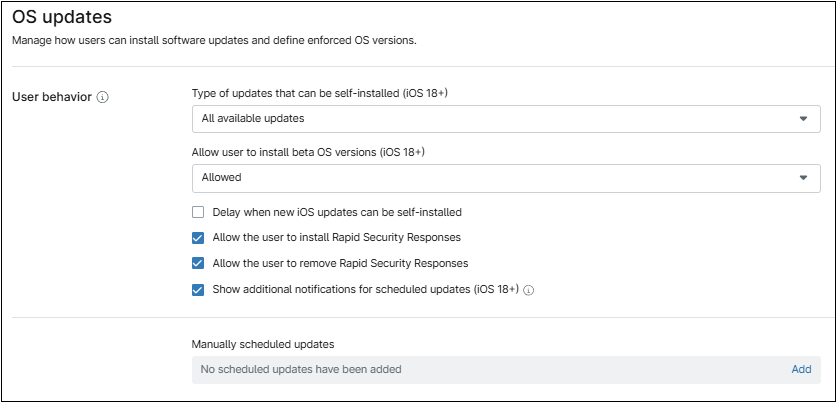
5. OS updates
This category defines how users can install software updates and defines enforced OS versions.
- Type of updates that can be self-installed (iOS 18+). This option controls what updates will be installed. Options are: All available updates, Highest available update, and Lowest available update.
- Allow user to install beta OS versions (iOS 18+). This option controls the installation of beta OS versions. The available settings are: Allowed, Always On, and Always Off.
- Delay when new iOS updates can be self-installed. This option delays the availability of a released operating system (OS) update for the device. When enabled, you can specify the delay duration, which can range from 1 to 90 days.
- Allow the user to install Rapid Security Responses. If enabled, critical security updates released by Apple will be installed. RSRs are released more quickly than traditional OS updates.
- Allow the user to remove Rapid Security Responses. This option controls the ability for a used to remove RSRs.
- Show additional notifications for scheduled updates (iOS 18+). If enabled, users will receive daily notifications for updates scheduled in the future. If disabled, users will only receive notifications beginning one hour before the scheduled deadline.
- Manually scheduled updates. This option is used to enforce software updates. An approval date is set to give the user the option to install the update voluntarily. If the user does not install the update by the approval date, an enforcement date ensures the update is installed automatically.
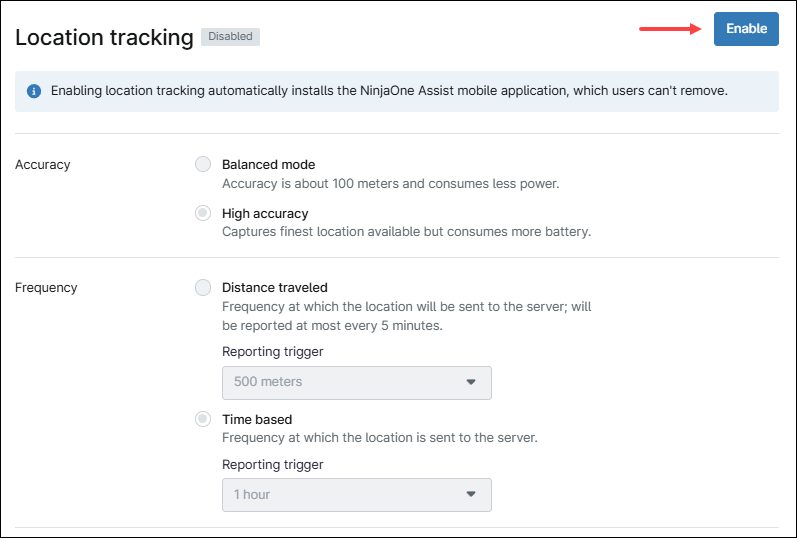
6. Location tracking
This category enables location tracking and specifies the accuracy and frequency of location updates.
Follow the instructions below to enable location tracking.
a. Click Enable.
b. Select accuracy: Balanced mode is accurate to within 100 meters and consumes less battery. High Accuracy mode captures the best available location but consumes more battery.
c. Select the location update frequency: Distance traveled means a location update is sent to the server after the device moves a specified distance (500 m, 1000 m or 5000 m). Time based means a location update is sent to the server based on time. Options are five minutes, 30 minutes, one hour, six hours, 12 hours or 24 hours.
d. Click Save.
Note: Location tracking requires the NinjaOne Assist app to be installed and active on the device, with Location Services enabled. The app must also be added to the policy as a managed application with Forced Install selected.