Managing and securing employee iPhones is essential for businesses, particularly as mobile devices become integral to daily operations. Apple iOS Restrictions provide a comprehensive solution for controlling device functionality, safeguarding corporate data, and ensuring compliance with company policies. With NinjaOne, IT administrators can efficiently configure and enforce these restrictions across the organization’s iOS devices, streamlining device management and enhancing security.
How to Apply iOS Restrictions With NinjaOne
NinjaOne simplifies the process of applying iOS Restrictions through an intuitive interface and robust policy management. Here’s a step-by-step guide:
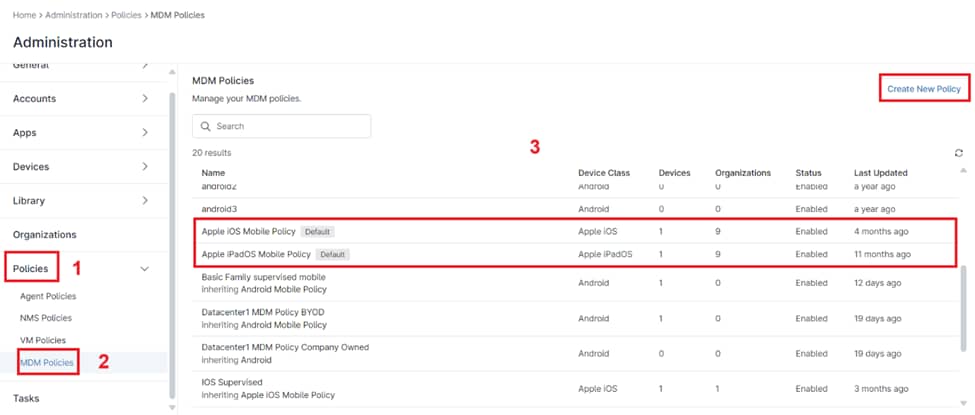
1. Navigate to iOS Policies:
- Start by going to the “Administration” section in the left navigation pane.
- Then, select “Policies” followed by “MDM Policies” to access iOS device management.
2. Select an iOS Policy:
- To create a brand new policy, click “Create New Policy.”
- If you want to modify an existing policy, simply select it from the list provided.
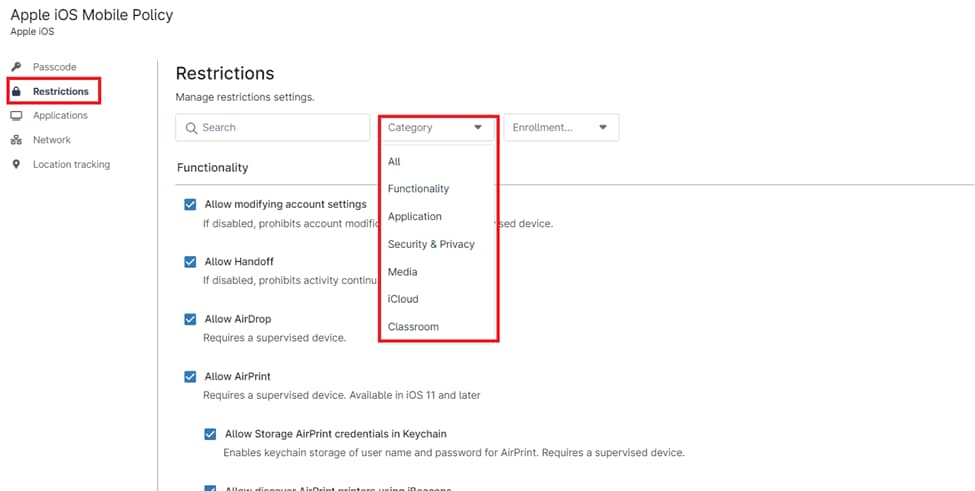
3. Managing Restrictions:
- Click on the “Restrictions” tab in the policy editor screen to access restriction settings for iOS devices.
- Configure specific restrictions such as app installations, system features, and security settings according to your organization’s requirements.
4. Save and Close:
- Once you’ve configured the restrictions, click “Save.”
- After saving, click “Close” to exit the policy editor.
Note: Ensure the policy is applied to the relevant devices or organizations so the restrictions are enforced.
Managing iOS Restrictions
All restrictions are categorized under Functionality, Application, Security and Privacy, Media, iCloud, and Classroom. These restrictions can be filtered using the Category dropdown at the top of the page. To enable or disable a restriction, simply check or uncheck the box next to the restriction name.
This table presents the available settings as of the date of writing.
| Functionality | Functionality | Functionality | Application |
| Allow modifying account settings | Allow Find My Friends | Allow unmanaged apps to read contacts from managed contacts accounts | Allow Game Center |
| Allow Handoff | Allow modifying Find My Friends settings | Allow booting into recovery by unpaired devices | Allow adding Game Center friends |
| Allow AirDrop | Allow automatic sync while roaming | Allow users to accept untrusted TLS certificates | Allow multiplayer gaming |
| Allow AirPrint | Allow host pairing | Allow USB accessories while device is locked | Allow Installation Apps |
| Allow Storage AirPrint credentials in Keychain | Allow keyboard shortcuts | Allow voice dialing while the device is locked | Allow automatic app download |
| Allow discover AirPrint printers using iBeacons | Show Notification Center on Lock screen | Allow adding VPN configurations | Allow installing apps using App Store |
| Disallow AirPrint to destinations with untrusted certificates | Allow lock screen today view | Allow modifying Wallpaper | Allow removing apps |
| Allow Modifying cellular data app settings | Allow Mail Privacy Protection | Treat AirDrop as unmanaged destination | Allow app installation from alternative marketplaces |
| Allow App Clips | Allow managed apps to write contacts to unmanaged contacts accounts | Require passcode on first outgoing AirPlay pairing | Allow Siri |
| Allow Apple personalized advertising | Allow News | Require Touch ID / Face ID authentication before AutoFill | Show user-generated content in Siri |
| Allow autocorrection | Allow NFC | Force automatic date and time | Allow Siri when device is locked |
| Allow modifying Bluetooth settings | Allow modifying notification settings | Force encrypted backups | Enable Siri profanity filter assistant |
| Allow Camera | Allow documents from managed sources in unmanaged destinations | Require iTunes Store password for all purchases | Allow iBooks Store |
| Allow FaceTime | Allow documents from unmanaged sources in managed destinations | Force limited ad tracking | Allow iMessage |
| Allow modifying cellular plan settings | Allow over-the-air PKI updates | Force on-device only dictation | Allow in-app purchases |
| Allow continuous path keyboard | Allow pairing with Apple Watch | Force on-device only translation | Allow iTunes Store |
| Allow Definition Lookup | Allow Apple Wallet notifications on lock screen | Force Apple Watch wrist detection | Allow Apple Music |
| Allow modifying device name | Allow Personal Hotspot modification | Join only Wi-Fi networks installed by a Wi-Fi payload | Allow podcasts |
| Allow submitting diagnostic and usage data to Apple | Allow predictive keyboard | Force Wi-Fi Power On | Allow Radio |
| Allow modifying diagnostic settings | Allow setting up new nearby iOS devices | Require managed pasteboard | Allow use of Safari |
| Allow dictation | Allow screenshots and screen recording | Enable Autofill on Safari | |
| Allow Screen Time | Allow Shared iPad temporary session | Enable JavaScript on Safari | |
| Allow trusting new enterprise app authors | Allow iCloud Photo Sharing | Block pop-ups on Safari | |
| Allow Erase All Content and Settings | Allow spell check | Force fraud warning on Safari | |
| Allow modifying eSIM settings | Allow Siri Suggestions | Allow removing system apps | |
| Allow Find My Device | Allow user installation of configuration profiles | Accept cookies |
| Security and Privacy | Media | iCloud | Classroom |
| Allow auto unlock | Allow explicit sexual content in Apple Books | Allow iCloud backup | Allow AirPlay screen view |
| Allow Touch ID / Face ID to unlock device | Allow playback of explicit music, podcast & iTunes U media | Allow iCloud Keychain sync | Allow Classroom screen view without prompting |
| Allow modifying passcode | Allow Files Network Drive Access | Allow iCloud Photo Library | Automatically join Classroom classes without prompting |
| Allow modifying Touch ID / Face ID | Allow Files USB Drive Access | Allow iCloud Private Relay | Require teacher permission to leave Classroom app unmanaged classes |
| Allow password autofill | Allowed content ratings – Apps | Allow backup of enterprise books | Allow Classroom to lock apps or the device without prompting |
| Allow proximity based password sharing requests | Allowed content ratings – Movies | Allow notes and highlights sync for enterprise books | |
| Allow password sharing | Ratings region | Allow managed apps to store data in iCloud | |
| Allow lock screen Control Center | Allowed content ratings – TV Shows | Allow My Photo Stream | |
| Allow cloud document sync |
Benefits of Using NinjaOne for iOS Restrictions
NinjaOne offers several advantages for managing iOS restrictions compared to manual configuration or other MDM solutions:
- Centralized Management: Manage restrictions for all your iOS devices from a single console.
- Scalability: Easily apply and enforce restrictions across a large number of devices.
- Increased Security: Protect sensitive company data and ensure compliance with security policies.
Strategies for iOS Restrictions with NinjaOne
- Security-Focused Restrictions: Prioritize restrictions that enhance device security, such as enforcing strong passwords, disabling USB file transfer, and restricting access to sensitive data.
- Productivity-Driven Restrictions: Implement restrictions that minimize distractions and promote a productive work environment, such as disabling games or social media apps.
- Phased Rollouts: When introducing new restrictions, consider a phased rollout approach. Start with a small group of users to test the impact and gather feedback before deploying to the entire organization.
