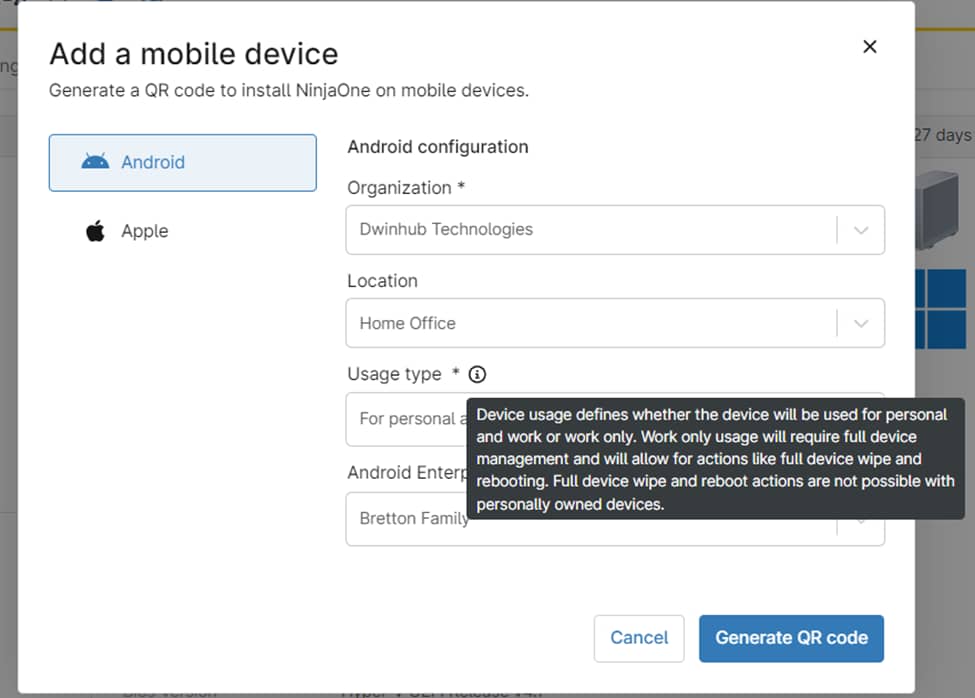
This guide will introduce to you the benefits of MDM Security and Privacy. Mobile Device Management (MDM) solutions are essential tools for businesses to secure and manage the growing number of devices connecting to their networks. However, MDM implementations raise valid concerns about user privacy, especially in BYOD (Bring Your Own Device) environments.
This document outlines how NinjaOne’s MDM functionality addresses these concerns while providing robust security features, enabling organizations to effectively manage and protect devices without compromising employee privacy. We’ll explore key areas like device security, data protection, BYOD security policy, and the benefits of using NinjaOne MDM software for comprehensive mobile device management solutions.
Security vs Privacy: Finding the Right Balance
Mobile Device Management allows enterprises to control and secure data on both personally owned and corporate devices. However, an effective MDM solution must delicately balance security requirements with respect for individual user privacy, addressing MDM privacy concerns.
This balance is especially important for organizations managing a mix of BYOD and COPE devices alongside fully managed corporate devices.
For BYOD and COPE devices, privacy protections are prioritized. NinjaOne’s mobile device management software ensures that personal applications on personally owned Apple devices are visible to administrators but cannot be managed or acted upon.
Browsing history and messages remain entirely inaccessible, maintaining user privacy. Security features such as data encryption, remote wipe, and secure access controls can be applied to protect corporate data without interfering with personal data.
Additionally, device-level management options, including application whitelisting and blacklisting, allow administrators to safeguard corporate information without visibility into personal apps.
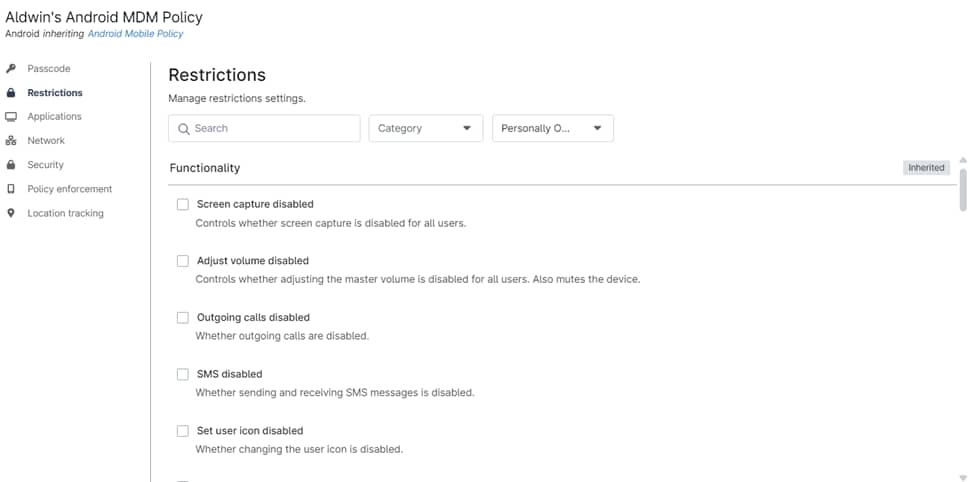
What MDM Can See vs What It Cannot See
One of the most common questions users have is, “What does MDM actually see on my device?” This is where transparency is crucial. With our MDM solution, the scope of visibility depends on the ownership model of the device.
- BYOD (Bring Your Own Device): When it comes to personal devices, the MDM is restricted to seeing corporate app inventories, not personal ones. Apple MDM can view personally installed apps but cannot block them or access their usage or data, such as personal emails, messages, or browsing histories.
- COPE (Corporate-Owned, Personally Enabled): On COPE devices, NinjaOne’s MDM solution offers deeper security while maintaining a clear division between corporate and personal spaces. Corporate apps can be managed, and restrictions can be placed to prevent sharing corporate data into personal apps, but the privacy of the user’s personal apps is still upheld.
- Fully Managed Devices: For fully managed or supervised devices, the MDM has a greater level of visibility and control. This includes full app inventories and device status checks to ensure compliance with corporate policies. However, even here, we strive to protect user privacy by limiting invasive monitoring.
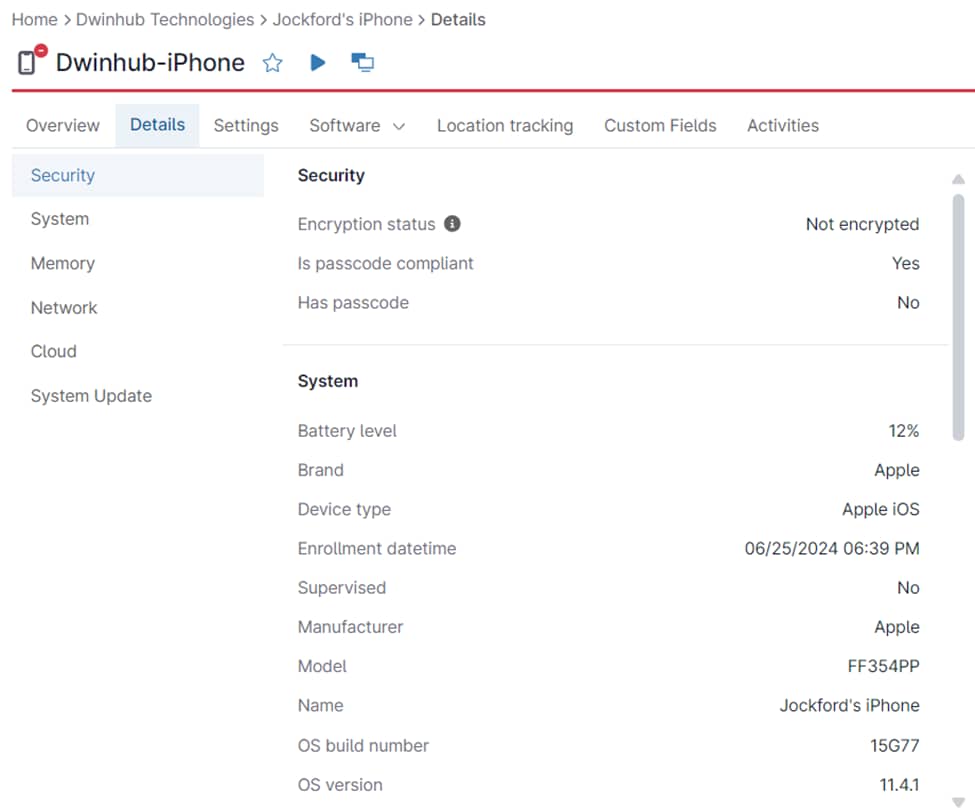
Enforcing Security Without Compromising Privacy
NinjaOne MDM offers advanced controls to protect corporate data on managed devices without compromising user privacy. Administrators can enforce policies to prevent corporate data from being copied to personal applications, set up secure work profiles, and restrict data transfers between managed and unmanaged apps, ensuring that corporate information stays secure.
For personally owned devices, NinjaOne MDM ensures strict separation of corporate and personal application inventories. Additionally, location tracking settings can be disabled, balancing necessary security with user privacy during work operations.
Building Trust with Transparent Policies
Security is a critical requirement in any enterprise environment, but ensuring the privacy of employees is equally important. NinjaOne MDM is designed with transparency at its core, providing clear and accessible information about what data is visible to IT administrators and what remains private. By maintaining this transparency, NinjaOne MDM fosters trust between IT teams and end-users, enabling a productive environment where both security and privacy coexist seamlessly.
The Benefits of Using NinjaOne for MDM Security and Privacy
- User-Friendly Interface: NinjaOne’s intuitive interface simplifies MDM tasks, making it easy to implement and manage security policies.
- Comprehensive Feature Set: NinjaOne offers a wide range of security features, including device enrollment, policy management, remote wipe, and encryption enforcement.
- Flexibility and Scalability: NinjaOne adapts to diverse device environments and scales to accommodate growing organizations.
- Strong Privacy Focus: NinjaOne prioritizes user privacy with features like data segregation and selective wiping, addressing BYOD privacy concerns.
Strategies for MDM Security and Privacy with NinjaOne
- Risk-Based Approach: Tailor security policies based on the sensitivity of data and the risk profile of different devices.
- Least Privilege Principle: Grant only the necessary access permissions to users and applications.
- Regular Policy Review: Periodically review and update MDM policies to adapt to evolving security threats and privacy regulations.
- Employee Training: Educate employees about security best practices, BYOD policies, and their role in maintaining a secure mobile environment.
Examples of NinjaOne MDM Use Cases
- Securing Company-Owned Devices: Enforce strong passcodes, restrict app installations, and manage device access to protect sensitive corporate data.
- Managing BYOD Environments: Implement containerization to separate work and personal data, ensuring employee privacy while maintaining control over corporate resources.
- Ensuring Compliance: NinjaOne enforces data encryption, access controls, and other security measures out of the box, simplifying regulatory compliance.
By implementing NinjaOne’s MDM solution and following these best practices, organizations can effectively manage and secure their mobile devices while respecting employee privacy.