Android policies are divided into seven categories, which are explained in the following lines:
Passcode
When enabled, this category defines passcode settings like complexity and duration. There are two tabs in this category: Device scope and Profile scope. Device scope applies for full device ownership, while Profile scope applies for the work profile of the device only. See the table below to see the different settings controlled by this category.
| Setting | Definition |
| Require password to unlock | This defines whether a passcode is required to unlock the device.
|
| History length | Number of passwords remembered (100 is the maximum allowed). |
| Maximum failed passwords for wipe | The maximum number of incorrect passwords entered before the device (or the profile) is wiped. |
| Maximum passcode age (days) | The maximum number of days that must pass before the passcode expires. If the passcode expires, the device (or work profile apps) will not be accessible. |
| Password quality | This field defines the passcode complexity:
|
Table 2. Android Passcode category settings.
Restrictions
This category includes a series of restrictions that can be applied. They are divided into Functionality, Application, Network & Internet, and Security & Privacy. Some restrictions apply to company-owned devices and others to BYOD. When a restriction applies to BYOD devices, it also applies to company-owned devices. Refer to the table below for an explanation of each restriction.
| Setting | Category | Enrollment | Description |
| Screen capture disabled | Functionality | BYOD | If checked, screen capture is disabled. |
| Adjust volume disabled | Functionality | BYOD | If checked, adjusting the volume is disabled. |
| Outgoing calls disabled | Functionality | BYOD | If checked, adjusting the volume is disabled. |
| SMS disabled | Functionality | BYOD | If checked, adjusting the volume is disabled. |
| Set user icon disabled | Functionality | BYOD | If checked, changing the used icon. |
| Camera disabled | Functionality | BYOD | If checked, the camera is disabled. |
| Factory reset disabled | Functionality | BYOD | If checked, the option to reset the device to factory settings is disabled. |
| Unmute microphone disabled | Functionality | Company-owned | If checked, the microphone cannot be disabled. |
| Set wallpaper disabled | Functionality | Both | If checked, changing the wallpaper is disabled |
| Fun disabled | Functionality | Both | If checked, the Easter egg game in Settings is disabled |
| Create windows disabled | Functionality | Both | If checked, creating windows besides app windows is disabled. |
| Auto date and timezone | Functionality | Company-owned |
|
| Printing policy | Functionality | Company-owned | Controls whether printing is allowed. This is supported on devices running Android 9 and above. |
| Screen brightness mode | Functionality | Company-owned | Controls the screen brightness mode. |
| Screen brightness | Functionality | Company-owned | The screen brightness between 1 and 255 where 1 is the lowest and 255 is the highest brightness. Supported on Android 9 and above. |
| Skip first use hints enabled | Application | BYOD | If checked, hints will be displayed on first start-up. |
| Install apps disabled | Application | BYOD | If checked, no apps can be installed. |
| Uninstall apps disabled | Application | BYOD | If checked, no apps can be uninstalled. |
| Modify accounts disabled | Security & Privacy | BYOD | If checked, modifying accounts is disabled. |
| Add user disabled | Security & Privacy | BYOD | If checked, adding users and profiles is disabled |
| Remove user disabled | Security & Privacy | BYOD | If checked, remove user disabled. |
| Mount physical media disabled | Security & Privacy | BYOD | If checked, mounting physical external media is disabled. |
| Credentials config disabled | Security & Privacy | BYOD | If checked, configuring user credentials is disabled. |
| Share location disabled | Security & Privacy | BYOD | If checked, location sharing is disabled. |
| Private key selection enabled | Security & Privacy | BYOD | If checked, a user interface can be displayed on the device for a user to choose a private key alias. |
| Keyguard disabled | Security & Privacy | BYOD | If checked, this disables the Lock Screen for primary and/or secondary displays. |
| Location mode. The degree of location detection enabled. | Security & Privacy | BYOD |
When location tracking is enabled, this setting is grayed out. |
| Screen timeout mode | Security & Privacy | Company-owned | Controls whether the user is allowed to configure the screen timeout. Supported on Android 9 and above. Options are Unspecified, User choice and Enforced. |
| Screen timeout | Security & Privacy | Company-owned | Controls the screen timeout duration. |
| Bluetooth disabled | Network & Internet | BYOD | If checked, Bluetooth is disabled. |
| Mobile networks configuration disabled | Network & Internet | BYOD | If checked, configuring mobile networks is disabled. |
| VPN configuration disabled | Network & Internet | BYOD | If checked, configuring VPN is disabled. |
| Bluetooth contact sharing disabled | Network & Internet | BYOD | If checked, Bluetooth contact sharing is disabled. |
| Bluetooth configuration disabled | Network & Internet | BYOD | If checked, Bluetooth configuration is disabled. |
| Cell broadcasts configuration disabled | Network & Internet | BYOD | If checked, cell broadcasts configuration is disabled. |
| Network reset disabled | Network & Internet | BYOD | If checked, network reset is disabled. |
| Outgoing beam disabled | Network & Internet | BYOD | If checked, using NFC to beam data from apps is disabled. |
| Data roaming disabled | Network & Internet | BYOD | If checked, data roaming services are disabled. |
| Network escape hatch enabled 1 | Network & Internet | BYOD | If checked, the network escape hatch is enabled. |
| Preferential network service 2 | Network & Internet | BYOD | If checked, Preferential network service is used for work applications. |
| USB data access | Network & Internet | Company-owned | Controls of what files and/or data can be transferred via USB. Supported only on company-owned devices.
|
| Configure Wi-Fi | Network & Internet | BYOD | Controls Wi-Fi configuring privileges. Based on the option set, user will have either full or limited or no control in configuring Wi-Fi networks.
|
| Tethering settings | Network & Internet | Company-owned | Controls tethering settings. Based on the value set, the user is partially or fully disallowed from using different forms of tethering.
|
| Wi-Fi direct settings | Network & Internet | BYOD | Controls configuring and using Wi-Fi direct settings. Supported on company-owned devices running Android 13 and above.
|
| Wi-Fi state | Network & Internet | Company-owned | Controls whether the Wi-Fi is on or off as a state and if the user can change said state. Supported on Android 13 and above. |
| Airplane mode state | Network & Internet | Company-owned | Controls the state of airplane mode and whether the user can toggle it on or off. Supported on Android 9. |
| Ultra-Wideband state | Network & Internet | Company-owned | Controls the state of the ultra-wideband setting and whether the user can toggle it on or off. |
| Cellular 2G state | Network & Internet | Company-owned | Controls the state of cellular 2G setting and whether the user can toggle it on or off. |
| Minimum Wi-Fi security level | Network & Internet | Company-owned | Defines the different minimum Wi-Fi security levels required to connect to Wi-Fi networks. Supported on Android 13 and above. |
1 If a network connection can’t be made at boot time, the escape hatch prompts the user to temporarily connect to a network to refresh the device policy. After applying policy, the temporary network will be forgotten, and the device will continue booting. This prevents being unable to connect to a network if there is no suitable network in the last policy and the device boots into an app in lock task mode, or the user is otherwise unable to reach device settings.
2 Controls whether preferential network service is enabled on the work profile. For example, an organization may have an agreement with a carrier that all the work data from its employees’ devices will be sent via a network service dedicated for enterprise use. An example of a supported preferential network service is the enterprise slice on 5G.
Applications
This category controls which apps can be installed or denied. It also controls the installation of apps and kiosk mode.
The Applications category has two tabs: Managed Apps and Kiosk Settings. Kiosk mode will be explained in section nine, for now the focus is the control of applications.
The Managed Applications tab has three sections: General, Always-on VPN and Managed Applications, each of which is explained below.
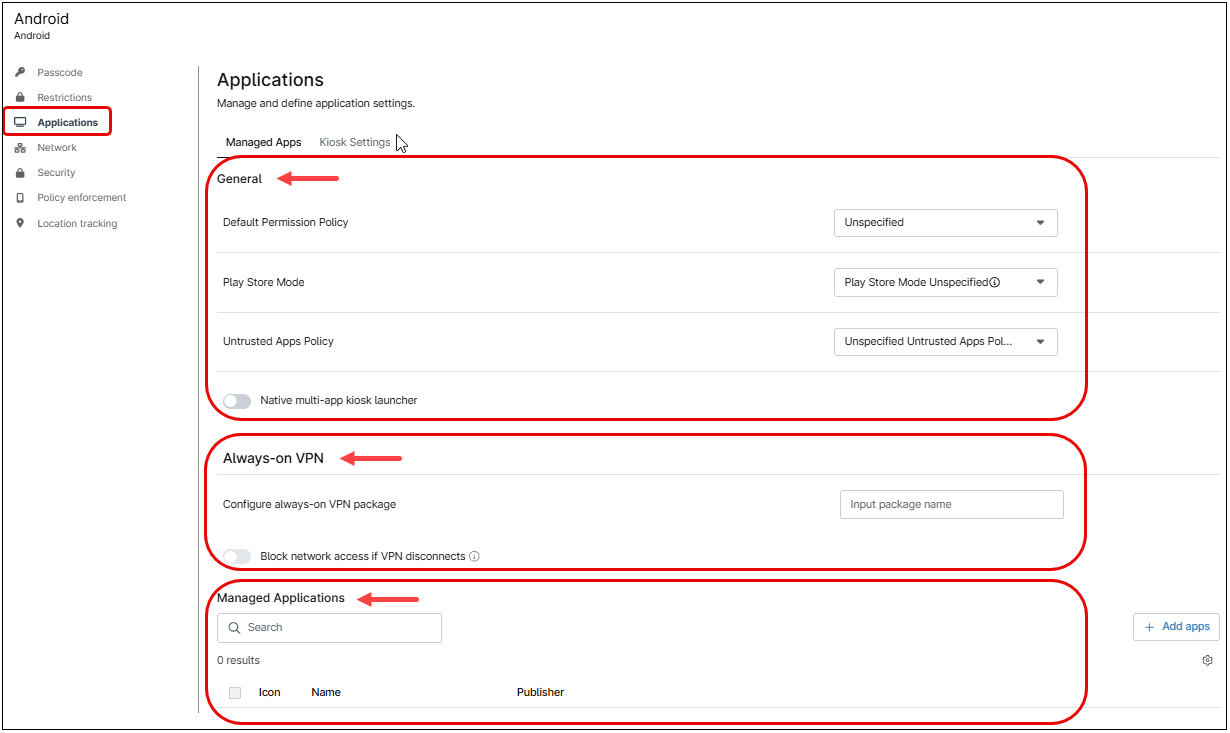
General section
Here, the policy can be configured to set permissions for all applications added to the device(s).
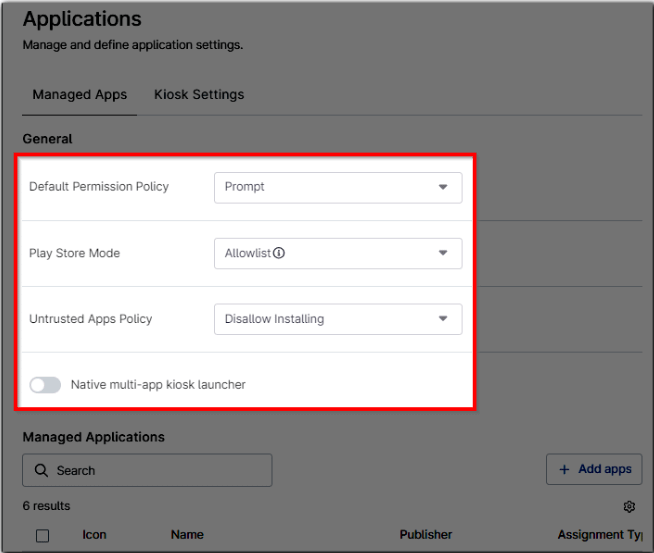
Refer to the table below for an explanation on these fields.
| Application Setting | Description |
| Default Permission Policy | Refers to the permissions that the app requires to access device resources or services like camera, location, etc.
This applies globally to all applications installed. Granular, per-app permissions management is available within app settings if preferred. Values can be Unspecified, Prompt, Grant or Deny. |
| Play Store Mode |
|
| Untrusted Apps Policy | Defines whether applications can be sideloaded onto the device, either via the web, file transfer, or developer options.
Possible values are Unspecified, Disallow installing, Allow installing in profile only and allow installing device wide. |
| Native multi-app kiosk launcher | This sets the kiosk mode to Multi-App, and enables the Kiosk Settings tab. |
Table 4. Android policy, general application settings
Always-on VPN section
Android can start a VPN service when the device boots and keep it running while the device or work profile is on. This section allows you to set a specific VPN application for this purpose. Optionally, network access can be blocked if the VPN application loses connectivity (use with caution, as offline devices cannot be managed). The VPN app must be added as a managed application to the policy.
To configure the VPN solution, enter the application package name (e.g., com.wireguard.android) in the corresponding settings. Any Android VPN application is supported. However, it is recommended to use one that supports remote configuration via managed configuration (accessible through the application details in the managed applications list). This is because the VPN solution must be configured before being set to always on. Failure to do so may cause errors on Android devices.
Managed Applications section
This section allows you to add, remove, and edit applications.
Once an app is added to the policy, it can be edited to modify its attributes. These attributes determine how the application will behave, such as whether it is allowed or denied. If allowed, you can further configure how the application will function once installed on the device.
The attributes must be edited for each application individually, they cannot be edited in bulk.
Applications can be System apps, Play Store apps, private apps, or Web apps.
Each added application will have an Application assignment type by default, as defined in the above section, however they can be edited and changed individually. The different assignment types are explained in the table below.
| Assignment Type | Description |
| Unspecified | Defaults to Available. Not available for system apps. |
| Preinstalled | The application is automatically installed and can be removed by the device’s user. |
| Force Installed | When set, the application will ignore any constraints or windows for installation and install as soon as possible. The app cannot be removed by the device’s user. If removed from the policy, the app will be removed from the device as well. |
| Blocked | Restricts the device’s user from using or installing the selected app. If the app is already installed, this setting will uninstall it. If a system app is blocked it will be disabled on the device. |
| Available | The application is made available for the device’s user to install it from the managed Google Play store. It will not be installed automatically; it must be selected by the user. Not available for system apps. |
| Required for Setup | The application is automatically installed and cannot be removed by the user. Device setup cannot be completed until the application is installed. Not available for system apps. |
| Single app Kiosk | The app is automatically installed in kiosk mode. It is set as preferred and allowlisted for lock task mode. Device setup cannot be completed until the application is installed. After installation, users cannot remove the app. This assignment type can be selected for only one application per policy. When this is present in the policy, the status bar will be automatically disabled. |
Table 5. Android Application Assignment Types.
Additionally, to the Application assignment type, each application has other attributes that are explained in the table below.
| Attribute (General tab) | Description |
| Assignment type | See table above. |
| Default Permission Policy | Refers to the permissions that the app requires to access device resources or services like camera, location, etc.
|
| Connected Work and Personal App | Some apps can connect to others, this setting controls whether work apps and personal apps can connect.
|
| Auto Update Mode | Controls how apps are updated without user intervention.
Unspecified. Defaults to “Default” Default. Updates happen over Wi-Fi when the phone is idle and charging. Postponed. Apps are not automatically updated. High Priority. Apps are updated immediately after Google Play approves them. |
| Allow force stop and clear data | Allow or restrict a user to force stopping an app and clear the cache.
Requires Android 11 or later versions. Unspecified. Defaults to Allowed. Allowed. Disallowed. |
| Application track for installation | This offers a list of available closed track application versions within Google Play. If an app developer supports application tracks, and the app has been shared with the customer connection ID, NinjaOne will show these versions of the app here. |
| Per app permission overrides | This setting is for specifically assigning permissions to device resources or services. The permission list is as follows:
ACCESS_COARSE_LOCATION, ACCESS_FINE_LOCATION, BLUETOOTH_ADVERTISE, BLUETOOTH_CONNECT, .BLUETOOTH_SCAN, CAMERA, GET_ACCOUNTS, POST_NOTIFICATIONS, READ_CONTACTS, READ_EXTERNAL_STORAGE, READ_MEDIA_AUDIO, READ_MEDIA_IMAGES, READ_MEDIA_VIDEO, READ_PHONE_STATE, RECORD_AUDIO and WRITE_EXTERNAL_STORAGE. Each of them can be assigned specific permissions, overriding the default permission policy (see above). |
| Overrides |
Displays the list of overridden permissions.
|
| Delegated scope overrides | This allows this app to have additional privileges (requires Android 11 or above). These privileges can include app permission management, certificate management, etc. |
| Delegated scope overrides () | Displays the list of delegated scope overrides. |
Table 6. Android App attributes.
Note: the attribute list has a second tab called Managed configurations. These configurations are application specific, and the number of fields can vary depending on the app. Refer to the application owner for specifics on these fields.
Follow the steps below to modify attributes of an application.
- Select the application from the list using the check mark to the left of its name.
- Click Edit. The edit application policy dialog box appears.
- Under Assignment type, select the assignment of your preference, per the assignment types shown on Table 5.
- Continue filling out the rest of the fields or app attributes per Table 6.
The following paragraphs explain how to add each type of app to the policy.
- Follow the steps below to add a Play Store app to the policy.
- Click the + Add apps button.
- Select Play Store. The Add New Package dialog box appears.
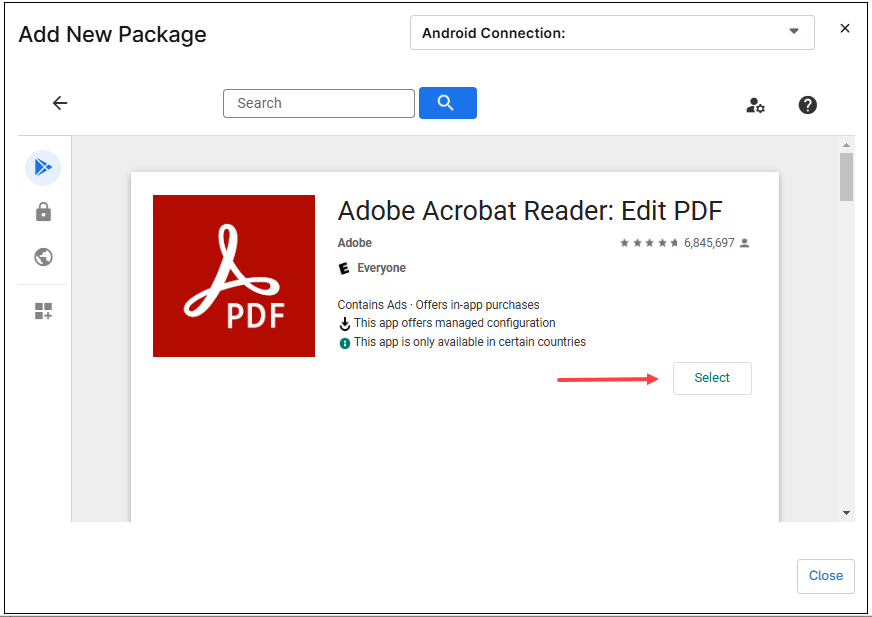
Figure 56. Add New Package dialog box. - Find the app from the list of applications, the search bar can be used to find the app more easily.
- Once the desired application is found, click on it and then click Select.
Figure 57. Select app to be added to the policy.
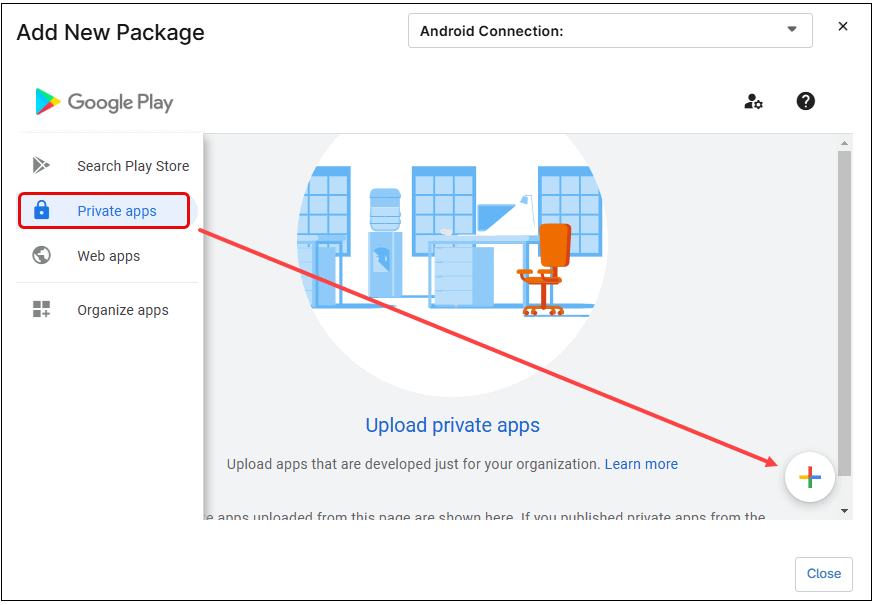
- Follow the steps below to add a private app to the policy.
- Click the + Add apps button.
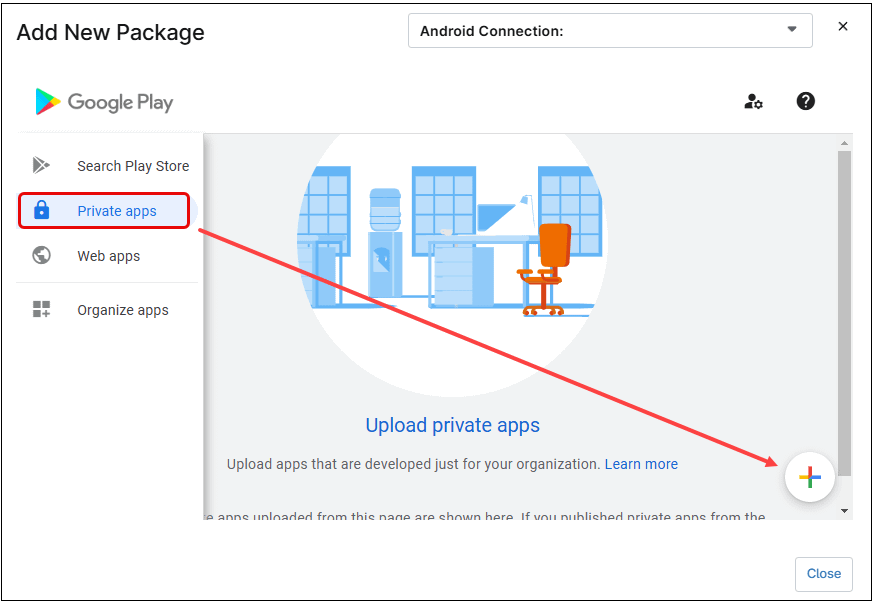
- Select Play Store. The Add New Package dialog box appears.
Figure 58. Add New Package dialog box. - Select Private Apps on the left side of the Add New Package dialog box (the padlock icon).
Figure 59. Private apps selection. - Click the + icon.
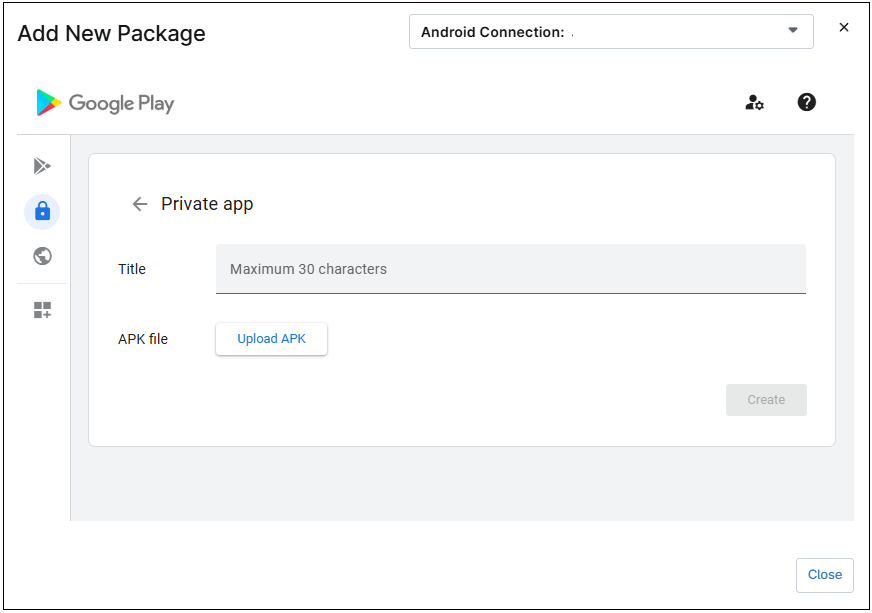
- Provide a name for the app and upload the APK file.
Figure 60. Private app; upload APK file. - Click Create.
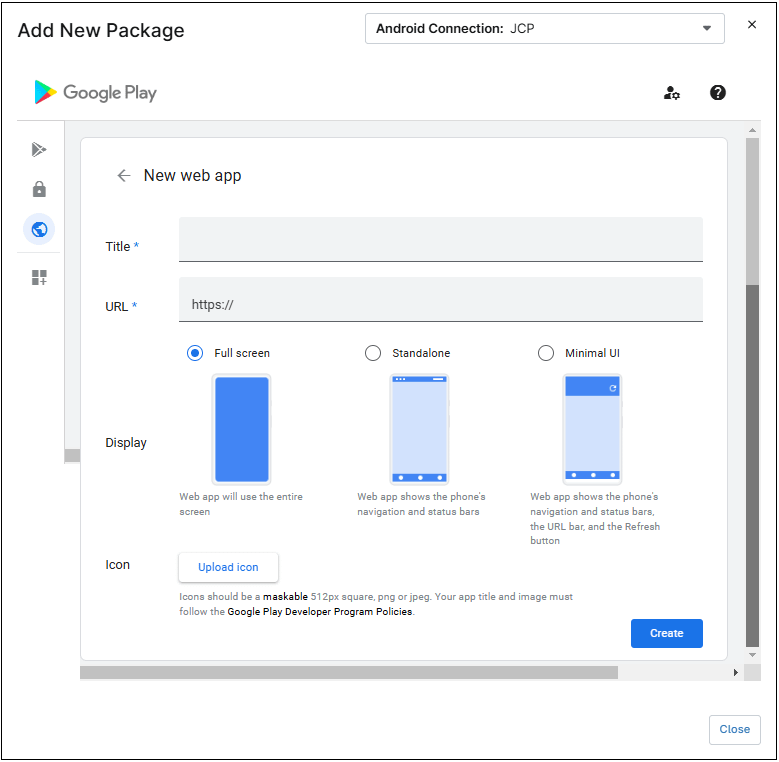
- Follow the steps below to add a Web app to the policy.
- Click the + Add apps button.
- Select Play Store. The Add New Package dialog box appears.
Figure 61.Add New Package dialog box. - Select Web Apps on the left side of the Add New Package dialog box (the earth icon).
Figure 62. Add new web app. - Click the + icon.
- Provide a name for the app and the URL. Then select how the web site will be displayed, and optionally upload an icon to identify the app.
If no icon is uploaded, a generic one will be inserted by NinjaOne.Figure 63. Select web app to be added to the policy. - Click Create.
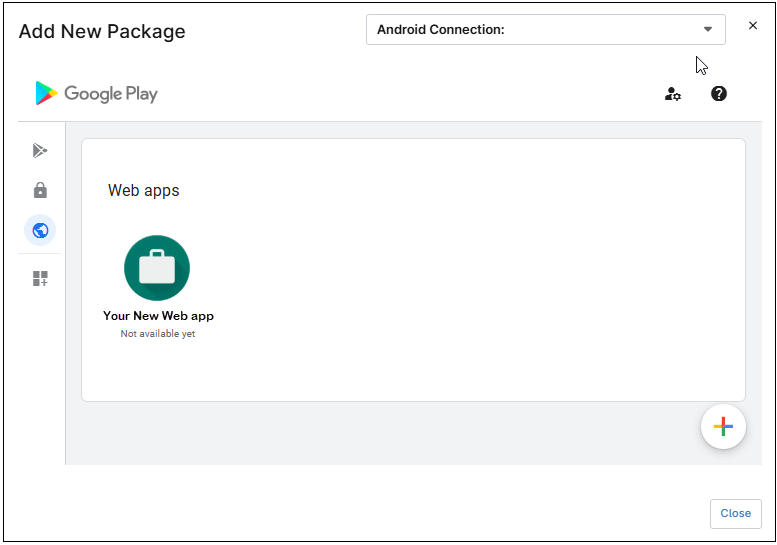
- After a few seconds, it will appear in the list as a web application. If more web applications were added before, they would all appear together.
Note: The newly added web app may take some minutes to be available to be added.Figure 64. web app list. - Click the newly added icon.
- Scroll down and click Select. If the Select button is grayed out, wait a few minutes and try again.
- Click Close.
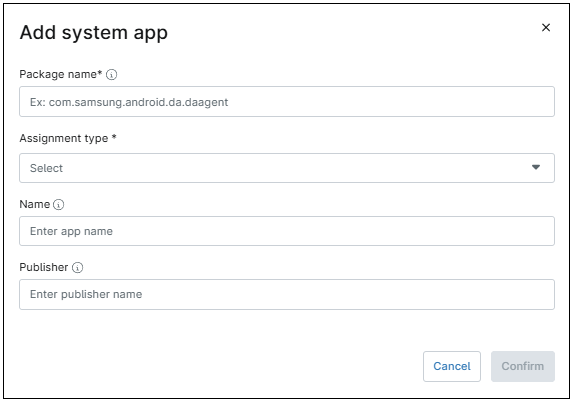
- Follow the steps below to add a System app to the policy.
- Click the + Add apps button.
- Select System app. The Add New system app dialog box appears.
Figure 65. Add New System app dialog box. - Fill out the app package name, then, select the assignment type from the drop-down. Then, optionally provide a name and publisher for the app.
- Click Confirm.
Network
In this category, device’s network settings can be configured, like Proxy and Wi-Fi networks. Multiple Wi-Fi networks can be added, but only one proxy.
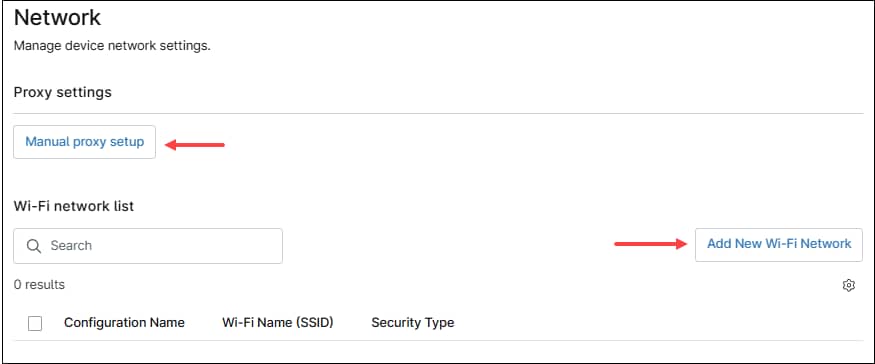
Proxy
Use the Manual proxy setup button to configure proxy settings. This action will open the Manual Proxy Setup dialog box.
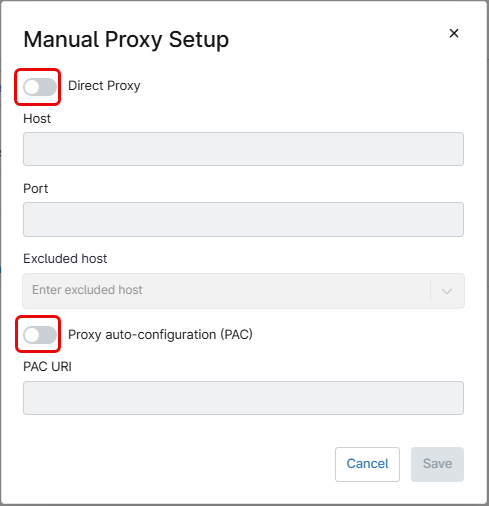
Turn on the Direct Proxy switch to manually enter the proxy configuration information – Host name and port.
Turn on the Proxy auto-configuration (PAC) switch to enter the URL for the PAC file.
Host names can be excluded from the proxy by writing the name under the Excluded host field and pressing enter.
After entering the information, click the blue Save button. This will add the proxy settings used by the mobile device. Once added, the information can be edited or removed.
Wi-Fi Networks
Use the Add new Wi-Fi Network button to configure a new Wi-Fi network. This action will open the Wi-Fi Network dialog box, then follow the next steps to configure a new Wi-Fi network.
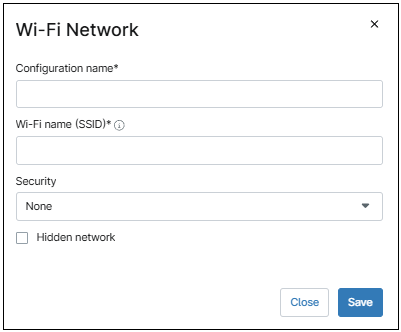
- Enter a configuration name (a friendly name of your choice to distinguish this Wi-Fi network).
- Enter the SSID.
- Under Security, select either ‘WPA-PSK‘ or ‘WEP-PSK‘ as the encryption method. This will bring up the Password field.
- Enter the password.
- Select Hidden network if it’s the case.
- Click Save.
- The new Wi-Fi network configuration will appear in the list. This network can be edited or removed by selecting it using the check mark to the left of the name.
Security
The Security category allows admins to encrypt the device, manage developer settings, define how data is moved for work, and more. There are 6 sections under this category which will be explained below.
General
- Minimum Android version support (API level). The minimum supported API level.
- Maximum time to lock (seconds). This field defines how many seconds pass before the device is locked and the user is required to input password.
- Encryption Policy—Enable the policy to require a password or not. Options are: Unspecified, Enabled without password and Enabled with password.
- Disabled keyguard customizations—Keyguard customizations are lockscreen items, such as widgets, notifications, camera access, and other tools while the device is locked.
- Battery Plugged Mode—The battery plugged in modes for which the device stays on. This setting is used to force a device to have its screen stay on under specific conditions (e.g., plugged into AC power, on wireless charging or connected to a USB connection). When using this setting, it is recommended to clear Maximum Time To Lock (above) so that the device doesn’t lock itself while it stays on.
- Developer Settings—Defines whether developer options such as system behaviors, quick settings, and safe boot are allowed. For more information about Android developer settings, please refer to Configure on-device developer options | Android Studio | Android Developers.
- Memory Tagging Extension (MTE). Defines whether MTE (a hardware feature that helps detect and fix memory safety bugs in Android) is used or not.
- Send content to assist apps. Allows for contextual content about the current app or screen state to be provided to assist apps such as Gemini, supported on Android 15+, disable to prevent content from being shared.
- Factory reset protection allowlisted accounts. This feature helps prevent unauthorized factory resets of the device. Enter the email addresses of all device administrators responsible for Factory Reset Protection (FRP), which may include one or more Google accounts. If someone attempts a factory reset, the device will require one of the listed administrators to log in with their Google account to unlock the device.
Custom messaging
Provide messages to notice the end user about unallowed actions or lockscreen.
- Short support message. Provide a short message that will be displayed on the device´s screen when an action is not permitted.
- Long support message. Provide a long message that will be displayed on the device´s screen when the user taps for more information on the action disallowed prompt.
- Lock screen message. Define a message that appears on the lockscreen of the device.
Personal Usage Policies
- Camera Disabled. Turn on this switch to disable the device camera.
- Screen Capture Disabled. Turn on this switch to disable taking screenshots.
- Controls how long the work profile can stay off (days). This setting is for COPE devices which can disable the work profile. It controls the maximum number of days that the work profile can be disabled. If the limit is reached and the work profile is not re-enabled, all personal applications are disabled, and the device can only be used for calls.
Cross-profile policies applied on the device
- Shown in personal profile contact searches and incoming calls.
This setting controls whether work contacts are displayed when receiving a call and when searching for contacts in the personal contacts app.
Drop-down menu.
- Unspecified. Default to “Allowed”.
- Disallowed. Contacts are not displayed.
- Allowed. Contacts are displayed.
- Copy and paste between profiles. Drop-down menu that controls whether copy and paste is allowed across personal and work profiles.
- Unspecified. Defaults to “Disallowed.”
- Disallowed. Copying and pasting across personal and work profiles is not allowed.
- Allowed. Copying and pasting across personal and work profiles is allowed.
- Data from either profile can be shared with the other profile. Drop-down menu that controls whether data can be shared between profiles.
- Unspecified. Defaults to “Disallowed.”
- Disallowed. Data cannot be shared between profiles.
- From Work to personal Disallowed. Data can be shared from personal profile to the work profile, but not the other way around.
- Allowed. Data can be shared from one profile to another.
System update configuration
- Type. Drop-down menu that controls how the OS and apps update will be performed. See below the explanation for each option.
- Unspecified. When updates are available, the user is prompted to install them.
- Automatic. Updates are installed as soon as they become available, without user intervention. If a reboot is required, it will occur automatically, which may disrupt ongoing work.
- Windowed. Updates are installed when available, but only during a specified update window. Selecting this option allows you to configure the update window.
Start minutes: (0-1439 minutes). Specifies the time after midnight, in minutes, when the update window begins.
End minutes: (0-1439 minutes). Specifies the time after midnight, in minutes, when the update window ends. - Postpone. The update will not be performed.
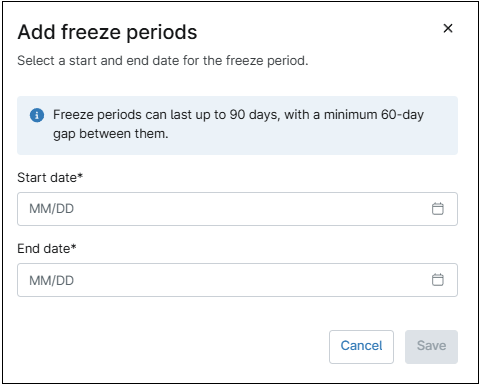
Freeze periods
Freeze Periods are timeframes during which over-the-air system updates are paused to maintain the current OS version on a device. To avoid indefinite freezing, each freeze period can last up to 90 days and must be followed by a minimum of 60 days before another freeze period can begin.
To add a freeze period, follow the steps below.
- Click the Add freeze periods button. The Add freeze periods dialog box appears.
Figure 69. Add freeze periods dialog box. - Enter the start date and the End date.
- Click Save.
Multiple freezing periods can be added, considering restrictions.
Policy enforcement
Policy enforcement rules are rules that define behavior when a policy cannot be enforced on a device. For example, blocking access to a certain setting in a work profile or on the entire device for a specific number of days. If certain aspects of the policy are not enforced correctly, there is an additional option to wipe the device. Follow the steps below to add a policy enforcement rule:
- Select Policy enforcement on the left side panel of the policy editor.
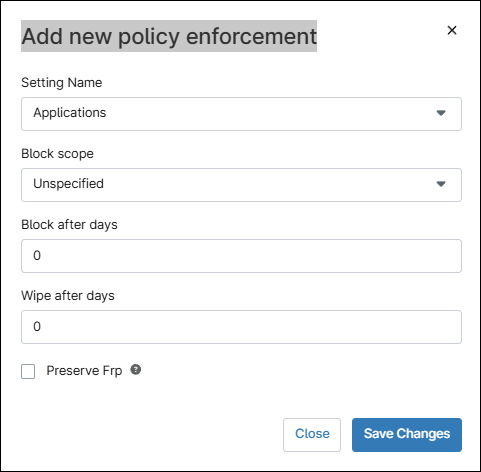
- Click +Add. The Add new policy enforcement dialog box appears.
Figure 70. Add new policy enforcement dialog box. - Under Setting Name, select setting you want to block. Refer to Table 6. (below) for an explanation for each setting.
Setting Name Description Applications Policy settings applied to applications. Keyguard disabled Disabled Lock Screen for primary and/or secondary displays. Permitted accessibility services If the field is not set, any accessibility service can be used. If the field is set, only the accessibility services in this list and the system’s built-in accessibility service can be used. In particular, if the field is set to empty, only the system’s built-in accessibility services can be used. This can be set on fully managed devices and on work profiles. When applied to a work profile, this affects both the personal profile and the work profile. Permitted input methods If present, only the input methods provided by packages in this list are permitted. If this field is present, but the list is empty, then only system input methods are permitted. Minimum API level Minimum allowed Android API level. Recommended global proxy The network-independent global HTTP proxy. Typically, proxies should be configured per-network in Network configuration. However, for unusual configurations like general internal filtering a global HTTP proxy may be useful. If the proxy is not accessible, network access may break. The global proxy is only a recommendation, and some apps may ignore it. Location mode Degree of location detection enabled. Always on VPN Package Specifies whether the app is allowed networking when the VPN is not connected and enabled. Only supported on devices running Android 10 and above. Bluetooth config disabled Whether configuring Bluetooth is enabled. Encryption policy Encryption configuration. Permission grants Explicit permission grants or denials for the app. Password policies Password requirement policies. Different policies can be set for work profile or fully managed devices by setting the password Scope field in the policy. Advanced security overrides Security policies set to secure values by default. To maintain the security posture of a device, we don’t recommend overriding any of the default values. Personal usage policies Policies managing personal usage on a company-owned device. Cross-profile policies Cross-profile policies applied on the device. Table 6. Policy enforcement settings
- Fill out the Block scope, Block after days, Wipe after days and Preserve Frp fields. Refer to Table 5 (below) for an explanation of each field.
Field Description Block Scope Block access to apps and data on a company owned device or in a work profile. This action also triggers a user-facing notification with information (where possible) on how to correct the compliance issue. Block after days Optionally, set a specific date for the setting to be blocked X days following the date the policy changes are saved. Wipe after days An action to reset a company owned device or delete a work profile. This number must be greater then “Block after days” and up to 30. Preserve Frp Optionally, preserve the factory reset protection for personal profiles. Table 7. Policy enforcement scope and actions.
- Click Save Changes.
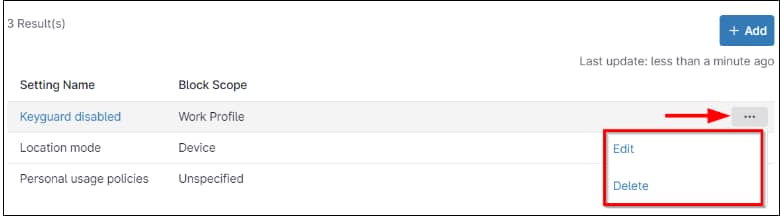
Once the policies are set, you can edit or delete them by hovering the mouse over the policy row and clicking the ellipsis button.Figure 71. Editing or deleting Policy enforcement rules.
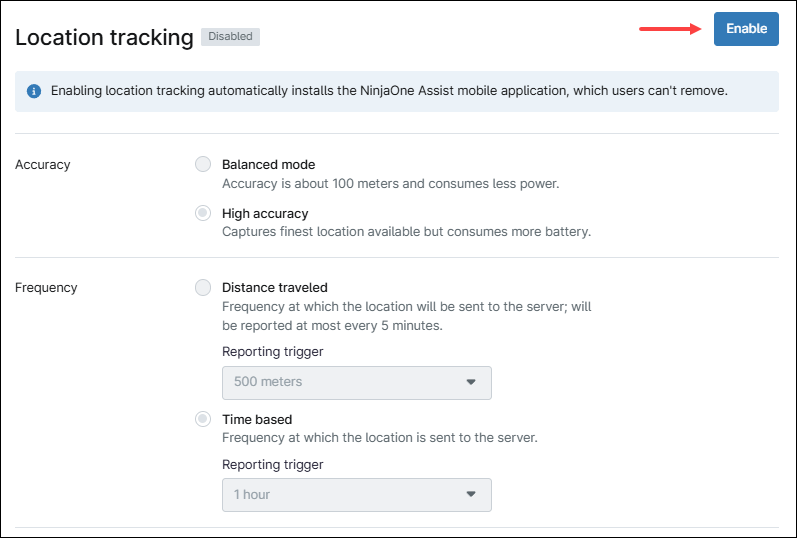
Location tracking
This category enables location tracking and specifies the accuracy and frequency of location updates.
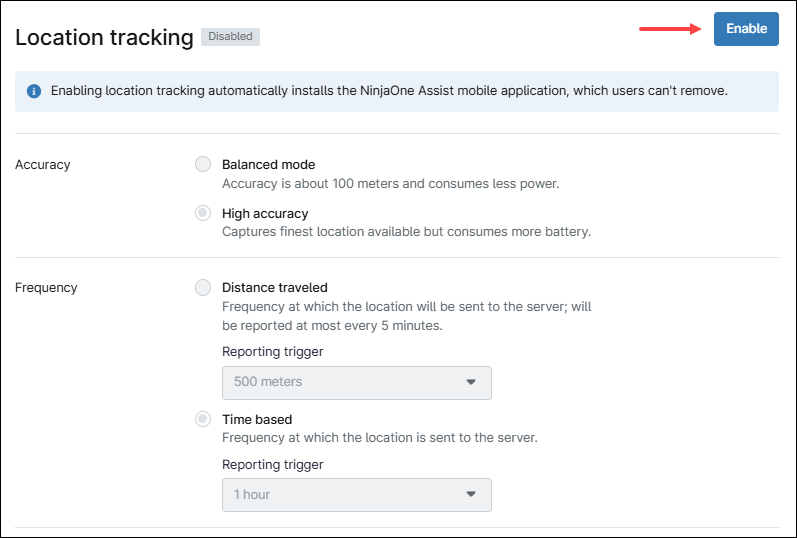
Follow the instructions below to enable location tracking.
- Click Enable.
- Select accuracy: Balanced mode is accurate to within 100 meters and consumes less battery. High Accuracy mode captures the best available location but consumes more battery.
- Select the location update frequency: Distance traveled means a location update is sent to the server after the device moves a specified distance (500 m, 1000 m or 5000 m). Time based means a location update is sent to the server based on time. Options are five minutes, 30 minutes, one hour, six hours, 12 hours or 24 hours.
- Click Save.
Note: Enabling location tracking automatically installs the NinjaOne Assist mobile app, which users can’t remove. Additionally, location tracking services must be allowed on the Android device.
iOS policites
iOS policies are divided into six categories, which are explained in the following lines:
Passcode
When enabled, this category defines passcode settings like complexity, history, etc. See the table below to see the different settings controlled by this category.
| Setting | Definition |
| Require alphanumeric value | Switch that, when activated, enforces the use of both numbers (123) and alphabetical characters (Abc) in the passcode. The “Require alphanumeric value” and “Allow simple passcode” switches are mutually exclusive. |
| Allow simple passcode | Switch that, when activated, allows entry of a simple passcode. Simple passcodes may contain repeated characters or increasing or decreasing characters (123 or CBA).). The “Require alphanumeric value” and “Allow simple passcode” switches are mutually exclusive. |
| Maximum number of failed attempts | The number of allowed failed attempts when entering the passcode at the device’s lock screen. After six failed attempts, a time delay is imposed before a passcode can be entered again. The delay increases with each attempt. If a user’s failed attempts exceed the number set in the policy, then the device will be wiped. |
| Maximum passcode age (days) | The number of days for which the passcode can remain unchanged. After this number of days, the user is required to change the passcode before the device is unlocked. If set to zero (0), then the passcode will not time out. This property is ignored for User Enrollments. |
| Maximum grace period for device lock | The period to unlock the phone without entering a passcode. When the grace period expires, the device is auto locked by the system and the user will be prompted to enter their passcode. |
| Minimum number of complex characters | A complex (or ‘special’) character is a character other than a number or a letter, such as & % $ #. This property is ignored for User Enrollments. |
| Minimum passcode length | This parameter is independent of the optional ‘Minimum number of complex characters’ setting. |
| Passcode history | The number set here defines the number of passcode entries that can be applied before a new, unique passcode must be created. For example, if this requirement is set to “3” then a user can reset their password to something they used in the past up to three times before they need to apply different characters. |
| Maximum auto-lock | The number of minutes for which the device can be idle before it gets locked by the system. When this limit is reached, the device is locked, and the passcode must be entered. The user can edit this setting on their device, but the value cannot exceed the policy setting. |
Table 8. iOS policy passcode settings.
Restrictions
Through this category, there is a series of restrictions that can be applied, they are divided into Functionality, Application, Network, Security & Privacy, Media, iCloud and Classroom. Some restrictions apply to supervised, others to unsupervised. All restrictions are displayed under their appropriate category and can be filtered using the Category dropdown at the top of the page; they can be enabled or disabled by checking/unchecking the box next to the restriction name. The policy configuration will be sent to all devices managed by the policy. Refer to the sections below for an explanation of each restriction.
Functionality restrictions
The table below explains the functionality restrictions for iOS policies. Some apply to supervised enrollment while others to unsupervised.
| Setting | Category | Enrollment | Description |
| Allow modifying account settings | Functionality | Supervised | If unchecked, it prohibits account modification. Requires a supervised device. |
| Allow Handoff | Functionality | Unsupervised. | If unchecked, it prohibits activity continuation. |
| Allow AirDrop | Functionality | Supervised | If checked, allows AirDrop sharing. |
| Allow AirPrint | Functionality | Supervised | Requires a supervised device. Available in iOS 11 and later |
| Allow Storage AirPrint credentials in Keychain.
(Requires Allow AirPrint enabled). |
Functionality | Supervised | Enables keychain storage of username and password for AirPrint. Requires a supervised device. |
| Allow Storage AirPrint credentials in Keychain.
(Requires Allow AirPrint enabled). |
Functionality | Supervised | Enables iBeacon discovery of AirPrint printers, which prevents spurious AirPrint Bluetooth beacons from phishing for network traffic. Requires a supervised device. Available in iOS 11 and later. |
| Disallow AirPrint to destinations with untrusted certificates.
(Requires Allow AirPrint enabled). |
Functionality | Supervised | Disallow AirPrint to destinations with untrusted certificates |
| Allow Modifying cellular data app settings | Functionality | Supervised | Enables changing settings for cellular data usage for apps. Requires a supervised device. |
| Allow App Clips | Functionality | Supervised | If disabled, prevents a user from adding any App Clips, and removes any existing App Clips on the device. Requires a supervised device. |
| Allow Apple personalized advertising | Functionality | Unsupervised | If disabled, limits Apple personalized advertising. Requires iOS 14 or later. |
| Allow autocorrection | Functionality | Supervised | Enables keyboard autocorrection. Requires a supervised device. |
| Allow modifying Bluetooth settings | Functionality | Supervised | Allows modification of Bluetooth settings. Requires a supervised device. Available in iOS 11 and later. |
| Allow Camera | Functionality | Supervised | If disabled, blocks the camera, and its icon is removed from the home screen. Users are unable to take photographs. |
| Allow FaceTime. (Requires Allow Camera enabled). | Functionality | Supervised | If disabled blocks Facetime. |
| Allow modifying cellular plan settings | Functionality | Supervised | If disabled, users can’t change any settings related to their cellular plan. Requires a supervised device. |
| Allow continuous path keyboard | Functionality | Supervised | Enables QuickPath keyboard. Requires a supervised device. |
| Allow Definition Lookup | Functionality | Supervised | Enables definition lookup. Requires a supervised device on iOS. |
| Allow modifying device name | Functionality | Supervised | If disabled, prevents the user from changing the device name. Requires a supervised device. |
| Allow submitting diagnostic and usage data to Apple | Functionality | Unsupervised | If disabled, prevents the device from automatically submitting diagnostic reports to Apple. Available for user enrollment. |
| Allow modifying diagnostic settings. (Requires Allow submitting diagnostic and usage data to Apple enabled.) | Functionality | Supervised | Enables changing the diagnostic submission and app analytics settings in the Diagnostics & Usage UI in Settings. Requires a supervised device. |
| Allow dictation | Functionality | Supervised | Enables dictation input. |
| Allow Screen time | Functionality | Supervised | If disabled, it blocks the ‘Enable Restrictions’ option in the Restrictions UI in Settings. On iOS 12 or later, it blocks the ‘Enable ScreenTime’ option in the ScreenTime UI and disables ScreenTime if it is already enabled. |
| Allow trusting new enterprise app authors | Functionality | Unsupervised | If disabled, it removes the ‘Trust Enterprise Developer’ button in Settings > General > Profiles & Device Management, preventing app installation via universal provisioning profiles. This restriction applies to free developer accounts but not to enterprise apps trusted through MDM. Previously granted trust is not revoked. |
| Allow Erase All Content and Settings | Functionality | Supervised | If turned off, disables the Erase All Content and Settings option in the Reset UI. |
| Allow modifying eSIM settings | Functionality | Supervised | If turned off, disables modifications to carrier plan related settings (only available on select carriers). |
| Allow Find My Device | Functionality | Supervised | Enables Find My Device in the Find My app. Available in iOS 13 and later. |
| Allow Find My Friends | Functionality | Unsupervised | Enables Find My Friends in the Find My app. Available in iOS 13 and later. |
| Allow modifying Find My Friends settings | Functionality | Unsupervised | Enables modifying Find My Friends settings. |
| Allow automatic sync while roaming | Functionality | Enables global background fetch activity when an iOS phone is roaming. | |
| Allow host pairing | Functionality | Supervised | If turned off, disables host pairing except for the supervision host. If no supervision host certificate is configured, all pairing is disabled. Host pairing allows administrators to control whether an iOS device can connect to a Mac or PC. |
| Allow keyboard shortcuts | Functionality | Supervised | If turned off, disables keyboard shortcuts. |
| Show Notification Center on Lock screen | Functionality | Unsupervised | If turned off, disables the Notifications history view on the lock screen, so users can’t view past notifications. However, they can still see notifications when they arrive. |
| Allow lock screen today view. | Functionality | Unsupervised | If turned off, disables the Today view in Notification Center on the lock screen. |
| Allow Mail Privacy Protection | Functionality | Unsupervised | If turned off, disables Mail Privacy Protection on the device. Available in iOS 15.2 and later. |
| Allow managed apps to write contacts to unmanaged contacts accounts | Functionality | Unsupervised | If enabled, managed apps can save contacts to unmanaged contact accounts. This restriction is ineffective if ‘Allow Open From Managed To Unmanaged’ is also enabled. To apply this restriction, you must install the payload through MDM. |
| Allow News | Functionality | Supervised | Allow the News app. |
| Allow NFC | Functionality | Supervised | Allow Near Field Communication. |
| Allow modifying notification settings | Functionality | Supervised | If turned off, disables modification of notification settings. |
| Allow documents from managed sources in unmanaged destinations | Functionality | Unsupervised | Controls data sharing between corporate (managed) and personal (unmanaged) apps or accounts on a device. |
| Allow documents from unmanaged sources in managed destinations | Functionality | Unsupervised | Controls whether users can transfer files or data from personal (unmanaged) apps or accounts to corporate (managed) apps or accounts. |
| Allow over-the-air PKI updates | Functionality | Unsupervised | If turned off, disables over-the-air PKI updates. Setting this restriction to false doesn’t disable CRL and OCSP checks. |
| Allow pairing with Apple Watch | Functionality | Supervised | If turned off, disables pairing with an Apple Watch. Any currently paired Apple Watch is unpaired, and the watch’s content is erased. |
| Allow Apple Wallet notifications on lock screen | Functionality | Unsupervised | Controls whether Apple Wallet notifications are shown on a locked screen. |
| Allow Personal Hotspot modification | Functionality | Supervised | Controls whether a user can manage the personal Hotspot. |
| Allow predictive keyboard | Functionality | Supervised | Controls whether users can enable or disable the predictive text feature on their keyboards. |
| Allow setting up new nearby iOS devices | Functionality | Supervised | Controls whether users can use their device to help set up other nearby iOS devices. |
| Allow screenshots and screen recording | Functionality | Unsupervised | If turned off, it disables saving a screenshot of the display and capturing a screen recording. It also disables the Classroom app from observing remote screens. |
| Allow Shared iPad temporary session | Functionality | Unsupervised | If turned off, temporary sessions aren’t available on Shared iPad. |
| Allow iCloud Photo Sharing | Functionality | Unsupervised | Controls whether users can use the iCloud Photo Sharing feature. |
| Allow spell check | Functionality | Supervised | Controls whether users can use the built-in spell-checking functionality. |
| Allow Siri Suggestions | Functionality | Unsupervised | Controls whether users can receive proactive suggestions from Siri. |
| Allow user installation of configuration profiles | Functionality | Supervised | If turned off, it prohibits the user from installing configuration profiles and certificates interactively. |
| Allow unmanaged apps to read contacts from managed contacts accounts | Functionality | Unsupervised | Controls whether personal (unmanaged) apps can access contact information stored within the corporate´s (managed) contacts account. |
| Allow booting into recovery by unpaired devices | Functionality | Unsupervised | Controls whether a device can be put into Recovery Mode by a computer or device that is not paired (trusted) with it. |
| Allow users to accept untrusted TLS certificates | Functionality | Unsupervised | Controls whether users can manually accept TLS certificates that are not verified by a trusted certificate authority. |
| Allow USB accessories while device is locked | Functionality | Supervised | Controls whether users can connect and use USB accessories to the device when it´s locked.
If the device has Lockdown mode enabled, this setting is ignored. |
| Allow voice dialing while the device is locked | Functionality | Unsupervised | If enabled, the voice dialing feature can be used while the device is locked. |
| Allow adding VPN configurations | Functionality | Supervised | If enabled, the user can add VPN configurations. |
| Allow modifying Wallpaper | Functionality | Supervised | If disabled, the user cannot modify the
device’s wallpaper. |
| Treat AirDrop as unmanaged destination | Functionality | Unsupervised | If enabled, it causes AirDrop to be considered an unmanaged drop target. |
| Require passcode on first outgoing AirPlay pairing | Functionality | Unsupervised | If enabled, all devices receiving AirPlay requests from this device to use a pairing password. |
| Require Touch ID / Face ID authentication before Autofill | Functionality | Supervised | If enabled, the user must authenticate before passwords or credit card information can be autofilled in Safari and Apps. If this restriction isn’t enforced, the user can toggle this feature in Settings. Only supported on devices with Face ID or Touch ID. |
| Force automatic date and time | Functionality | Supervised | If enabled, date and time are automatically set, and the user cannot change this behavior. |
| Force encrypted backups | Functionality | Unsupervised | If enabled, all backups are automatically encrypted. |
| Require iTunes Store password for all purchases | Functionality | Unsupervised | If enabled, forces the user to enter their iTunes password for each transaction. |
| Force limited ad tracking | Functionality | Unsupervised | If enabled, limits ad tracking. Additionally, it disables app tracking and the Allow Apps To Request To Track setting. |
| Force on-device only dictation | Functionality | Unsupervised | If enabled, the device won’t connect to Siri servers for the purposes of translation. |
| Force on-device only translation | Functionality | Unsupervised | If enabled, the device won’t connect to Siri servers for the purposes of translation. |
| Force Apple Watch wrist detection | Functionality | Unsupervised | If enabled, forces a paired Apple Watch to use Wrist Detection. |
| Join only Wi-Fi networks installed by a Wi-Fi payload | Functionality | Supervised
|
If enabled, limits device to only join Wi-Fi networks set-up via configuration profile. |
| Force Wi-Fi Power On | Functionality | Supervised
|
If enabled, prevents Wi-Fi from being turned off in Settings or Control Center, even by entering or leaving Airplane Mode. It doesn’t prevent selecting which Wi-Fi network to use. |
| Require managed pasteboard | Functionality | Unsupervised | If turned off, the system disallows iPhone widgets on a Mac that has signed in the same Apple ID for iCloud. Available on iOS 17 and later. |
| Allow iOS widgets on a Mac signed in with the same Apple ID | Functionality | Supervised | If turned off, the system disables live voicemail on the device Available in iOS 17.2 and later. |
| Allow live voicemail | Functionality | Supervised | If turned on, the system preserves eSIM when it erases the device due to too many failed password attempts or the Erase All Content and Settings option in Settings > General > Reset. Available in iOS 17.2 and later. Note: The system doesn’t preserve eSIM if Find My initiates erasing the device. |
| Allow auto dim | Functionality | Supervised | If turned off, disables auto dim on iPads with OLED displays. Available in iOS 17.4 and later. |
| Allow eSIM outgoing transfers | Functionality | Supervised | If turned off, it prevents the transfer of an eSIM from the device on which the restriction is installed to a different device. Available in iOS 18 and later. |
| Allow Genmoji | Functionality | Supervised | If turned off, it prohibits creating new Genmoji. Available in iOS 18 and later. |
| Allow Image Playground | Functionality | Supervised | If turned off, it prohibits the use of image generation. Available in iOS 18 and later. |
| Allow Image Wand | Functionality | Supervised | If turned off, it prohibits the use of Image Wand. Available in iOS 18 and later. |
| Allow Writing Tools | Functionality | Supervised | If turned off, disables Apple Intelligence writing tools. Available in iOS 18 and later. |
| Allow personalized handwriting results | Functionality | Supervised | If turned off, it prevents the system from generating text in the user’s handwriting. Available in iOS 18 and later. |
| Allow iPhone mirroring | Functionality | Supervised | If turned off, it prohibits the use of iPhone Mirroring. This prevents the iPhone from mirroring to any Mac. Available in iOS 18 and later. |
| Allow video conferencing remote control | Functionality | Supervised | If turned off, disables the ability for a remote FaceTime session to request control of the device. Available in iOS 18 and later. |
| Allow hiding apps | Functionality | Supervised | If turned off, disables the ability for the user to hide apps. It does not affect the user’s ability to leave it in the App Library, while removing it from the home screen. Available in iOS 18.0 and later. |
| Allow locking apps | Functionality | Supervised | If turned off, disables the ability for the user to lock apps. Because hiding apps also requires locking them, disallowing locking also disallows hiding. Available in iOS 18.0 and later. |
| Allow call recording | Functionality | Supervised | If turned off, call recording is disabled. Available in iOS 18.1 and later. |
| Allow mail summary | Functionality | Supervised | If turned off, disables the ability to create summaries of email messages manually. This does not affect automatic summary generation. Available in iOS 18.1 and later. |
| Allow RCS messaging | Functionality | Supervised | If turned off, prevents the use of RCS messaging. Available in iOS 18.1 and later. |
Table 9. iOS policy functionality restrictions.
Application restrictions
The table below explains the application restrictions for iOS policies. Some apply to supervised enrollment while others to unsupervised.
| Setting | Category | Enrollment | Description |
| Allow Game Center | Application | Supervised | If disabled, blocks Game Center, and its icon is removed from the Home screen. |
| Allow adding Game Center friends. Requires “Allow Game Center” to be enabled. | Application | Supervised | If disabled, prohibits adding friends to Game Center. As of iOS 13. |
| Allow multiplayer gaming. Requires “Allow Game Center” to be enabled. | Application | Supervised | If disabled, prohibits multiplayer gaming. |
| Allow Installation Apps | Application | Supervised | If disabled, blocks the App Store, and its icon is removed from the home screen. Users are unable to install or update their apps. |
| Allow automatic app download. Requires “Allow Installation Apps” to be enabled. | Application | Supervised | If disabled, prevents automatic downloading of apps purchased on other devices. This setting doesn’t affect updates to existing apps. |
| Allow installing apps using App Store. Requires “Allow Installation Apps” to be enabled. | Application | Supervised | If turned off, disables the App Store, and its icon is removed from the Home screen. However, users may continue to use host apps (iTunes, Configurator) to install or update their apps. |
| Allow removing apps | Application | Supervised | If disabled, user cannot remove any apps. |
| Allow app installation from alternative marketplaces | Application | Supervised | If disabled, prevents installation of alternative marketplace apps from the web and prevents any installed alternative marketplace apps from installing apps. This restriction does not impact the native App Store app. Available in iOS 17.4 and later. |
| Allow Siri | Application | Unsupervised | If disabled, prevents the use of the Siri built-in feature. |
| Show user-generated contents in Siri.
Requires “Allow Siri” to be enabled. |
Application | Supervised | If disabled, prevents Siri from querying user-generated content from the web. |
| Allow Siri when device is locked.
Requires “Allow Siri” to be enabled. |
Application | Unsupervised | Enable Siri when the device is locked. This restriction is ignored if the device doesn’t have a passcode set. |
| Enable Siri profanity filter assistant.
Requires “Allow Siri” to be enabled. |
Application | Supervised | If enabled, Siri will filter out and avoid using or recognizing any profane or explicit language in its responses and dictations. |
| Allow iBooks Store | Application | Supervised | If disabled, removes the Book Store tab from the Books app. |
| Allow iMessage | Application | Supervised | Enables the use of the iMessage with supervised devices. If the device supports text messaging, the user can still send and receive text messages. |
| Allow in app purchases | Application | Unsupervised | If turned off, prohibits in-app purchasing. |
| Allow iTunes Store | Application | Supervised | If turned off, disables the iTunes Music Store, and its icon is removed from the Home screen. Users cannot preview, purchase, or download content. |
| Allow Apple Music | Application | Supervised | If turned off, disables the Music service, and the Music app reverts to classic mode. |
| Allow podcasts | Application | Supervised | If turned off, disables the Podcasts app. |
| Allow Radio | Application | Supervised | If turned off, disables the radio app. |
| Allow use of Safari | Application | Unsupervised | If turned off, disables the Safari web browser app, and its icon is removed from the Home screen. This setting also prevents users from opening web clips. |
| Enable Autofill on Safari. Requires “Allow use of Safari” to be enabled. | Application | Supervised | If turned off, disables Safari AutoFill for passwords, contact info, and credit cards and also prevents the Keychain from being used for AutoFill. Though third-party password managers are allowed and apps can use AutoFill. |
| Enable JavaScript on Safari.
Requires “Allow use of Safari” to be enabled. |
Application | Unsupervised | If turned off, Safari doesn’t execute JavaScript. |
| Block pop-ups on Safari. Requires “Allow use of Safari” to be enabled. | Application | Unsupervised | If turned off, Safari doesn’t allow pop-up windows. |
| If enabled,
Requires “Allow use of Safari” to be enabled. |
Application | Unsupervised | If enabled, forces the use of Safari’s built-in security measures to help protect users from phishing attempts or other malicious websites that might steal personal information. |
| Allow removing system apps | Application | Supervised | If turned off, disables the removal of system apps from the device. |
| Accept cookies | Application | Unsupervised | Defines the behavior for Cross-Site Tracking and Cookies. Options are:
|
| Allow apps to be installed directly from the web | Application | Supervised | If turned off, the device prevents installation of apps directly from the web. Requires a supervised device. Available in iOS 17.5 and later. |
Table 10. iOS policy application restrictions.
Security & privacy restrictions
The table below explains the Security & Privacy restrictions for iOS policies. Some apply to supervised enrollment while others to unsupervised.
| Setting | Category | Enrollment | Description |
| Allow auto unlock | Security & Privacy | Unsupervised | If turned on, allows the ability to unlock Face ID-enabled phone with an associated Apple Watch.
Available in iOS 14.5 and later. |
| Allow Touch ID / Face ID to unlock device | Security & Privacy | Unsupervised | If turned on the device can be unlocked using Touch ID or Face ID. If turned off, the device can only be unlocked using passcode. |
| Allow modifying passcode | Security & Privacy | Supervised | If turned off, prevents the device passcode from being added, changed, or removed. This restriction is ignored by Shared iPads. |
| Allow modifying Touch ID / Face ID. Requires “Allow modifying passcode” to be enabled. | Security & Privacy | Supervised | If turned off, prevents modifying Touch ID / Face ID. This restriction is ignored by Shared iPads. |
| Allow password autofill | Security & Privacy | Supervised | If turned off, disables the AutoFill Passwords feature in iOS (with Keychain and third-party password managers) and the user isn’t prompted to use a saved password in Safari or in apps. This restriction also disables Automatic Strong Passwords, and strong passwords are no longer suggested to users. It doesn’t prevent AutoFill for contact info and credit cards in Safari. |
| Allow proximity based password sharing requests | Security & Privacy | Supervised
|
If turned off, disables requesting passwords from nearby devices. |
| Allow password sharing | Security & Privacy | Supervised
|
If turned off, disables sharing passwords with the Airdrop Passwords feature. |
| Allow lock screen Control Center | Security & Privacy | Supervised | If disabled, prevents Control Center from appearing on the Lock screen. |
Table 11. iOS policy security & privacy restrictions.
Media restrictions
The table below explains the Media restrictions for iOS policies. Some apply to supervised enrollment while others to unsupervised.
| Setting | Category | Enrollment | Description |
| Allow explicit sexual content in Apple Books | Media | Unsupervised | If disabled, the user can’t download Apple Books media that is tagged as erotica. |
| Allow playback of explicit music, podcast & iTunes U media | Media | Supervised | If disabled, hides explicit music or video content purchased from the iTunes Store. Explicit content is marked as such by content providers, such as record labels, when sold through the iTunes Store. |
| Allow Files Network Drive Access | Media | Supervised | If disabled, prevents connecting to network drives in the Files app. Available in iOS 13.1 and later. |
| Allow Files USB Drive Access | Media | Supervised | If disabled, prevents connecting to any connected USB devices in the Files app |
| Allowed content ratings – Apps | Media | Unsupervised | The maximum level of app content allowed on the device. Options are:
|
| Allowed content ratings – Movies | Media | Unsupervised | The maximum level of movie content allowed on the device. Options are:
|
| Ratings region | Media | Unsupervised | The two-letter key that profile tools use to display the proper ratings for the given region. Options are:
|
| Allowed content ratings – TV Shows | Media | Unsupervised | The maximum level of TV content allowed on the device. Options are:
|
Table 12. iOS policy media restrictions.
iCloud restrictions
The table below explains the iCloud restrictions for iOS policies. Some apply to supervised enrollment while others to unsupervised.
| Setting | Category | Enrollment | Description |
| Allow iCloud backup | iCloud | Unsupervised | Enables backing up the device to iCloud. |
| Allow iCloud Keychain sync | iCloud | Unsupervised | Enables iCloud keychain synchronization on the device. |
| Allow iCloud Photo Library | iCloud | Unsupervised | Enables iCloud Photo Library. Any photos not fully downloaded from iCloud Photo Library to the device are removed from local storage. |
| Allow iCloud Private Relay | iCloud | Unsupervised | Enables iCloud Private Relay. For iOS devices, this restriction requires a supervised device. |
| Allow backup of enterprise books | iCloud | Unsupervised | If turned off, disables backup of Enterprise books. Also available for user enrollment. |
| Allow notes and highlights sync for enterprise books | iCloud | Unsupervised | Enables synchronization of notes and highlights for enterprise books. |
| Allow managed apps to store data in iCloud | iCloud | Unsupervised | Allows managed apps to store their data in iCloud.
Enables My Photo Stream functionality. |
| Allow My Photo Stream | iCloud | Unsupervised | If enabled, photos taken on the device are automatically uploaded to My Photo Stream and synchronized across all other iOS devices linked to the same Apple ID via iCloud. |
| Allow cloud document sync | iCloud | Supervised | Enables document and key-value syncing to iCloud. As of iOS 13. Shared iPad doesn’t support it. |
Classroom restrictions
The table below explains the classroom restrictions for iOS policies. Some apply to Supervised enrollment while others to unsupervised.
| Setting | Category | Enrollment | Description |
| Allow AirPlay screen view | Classroom | Supervised | If turned off, disables remote screen observation by the Classroom app. If ScreenShot is disabled, the Classroom app doesn’t observe remote screens. |
| Allow Classroom screen view without prompting.
Requires “Allow AirPlay screen view” to be enabled. |
Classroom | Supervised | If enabled, Teachers using the Classroom app can view the screen of a supervised student’s device without the student being prompted to allow or deny the action. This is particularly useful for maintaining seamless classroom management and monitoring during lessons.
If disabled, Students will be prompted for permission each time a teacher attempts to view their device screen, giving them the ability to allow or deny access. |
| Require teacher permission to leave Classroom app unmanaged classes | Classroom | Supervised | If enabled, automatically gives permission to the teacher’s requests without prompting the student. |
| Allow Classroom to lock apps or the device without prompting | Classroom | Supervised | If enabled, Teachers using the Classroom app can remotely lock a student’s iPad or iPhone, or limit the device to a single app, without the student receiving a prompt or needing to approve the action. This ensures uninterrupted focus during lessons or exams.
If disabled, students will receive a prompt asking for their consent before the teacher can lock their device or restrict it to a specific app. |
Table 14. iOS policy classroom restrictions.
Applications
This category controls which apps are available to end users, and which apps are blocked from use. In addition, NinjaOne’s MDM supports apps assigned through Apple’s App and Books feature – formerly Volume Purchase Program (VPP). Apple Business Manager (ABM) content tokens are supported per organization/location, and provides information related to the token, assigned apps, and licenses from the MDM Configuration page in NinjaOne. To learn more about Apple’s App and Books, consult the Buying content through apps and books tutorial.
Follow the steps below to add and configure apps in a policy.
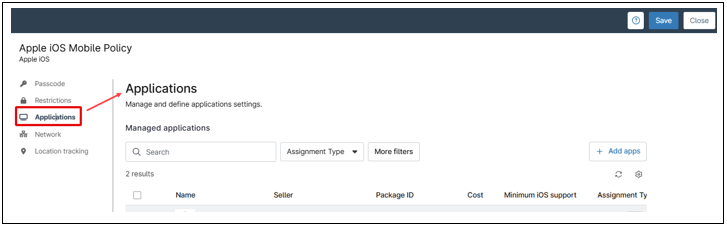
Click + Add apps.
- Switch between the Apps and Books and Public App Store tabs depending on the type of app you want to add. Please note that if you do not have your Apps and Books token set up you will not see any content under the Apps and Books tab.
- Type the name of the app or the app’s publisher into the search field. If you’re unsure what to enter, you can simply type a single letter and then click Search. A list of matching applications will appear.
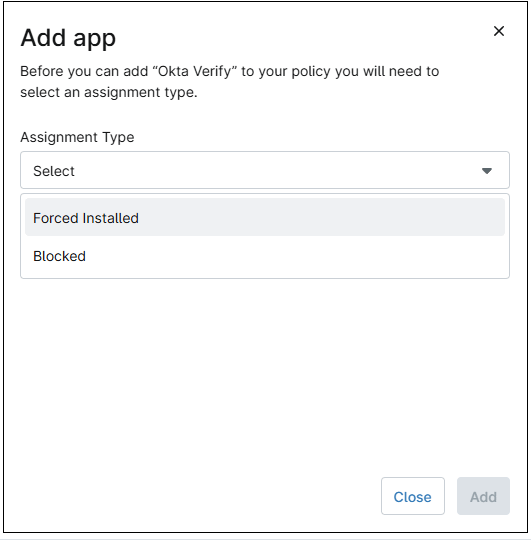
- Click the desired application. A dialog box will appear.
Figure 74. Apple iOS policy. Add app dialog box. - Select the assignment type from the drop-down (force installed or blocked). Note that the Blocked assignment type is only supported on supervised devices.
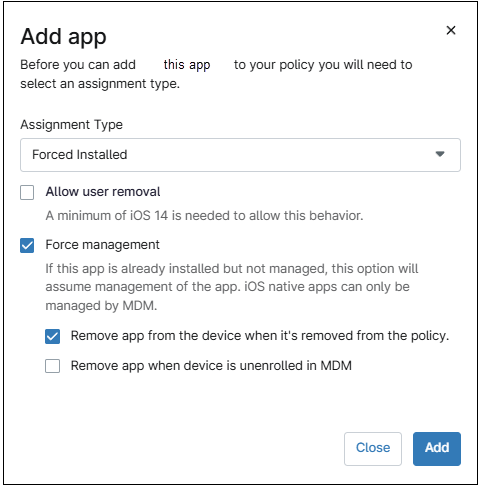
- If the selection was blocked, go to step eight.
- If the selection was Force Installed, fill out the remaining fields.
Figure 75. Apple iOS policy. app assignment type. Note: If you opt to remove the app when a device is removed from a policy, this function also applies when you switch a device’s policy under the Settings tab on the device dashboard if the new policy does not also have the app included.
- Click Add. You can continue adding applications, once you’re done,
- Click Save on the upper right side of the screen. Enter your MFA response method and close.
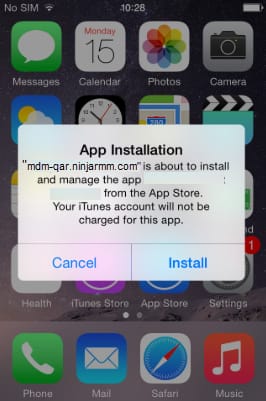
The app(s) will now appear under Managed Applications, displaying its details and assignment type. When the policy attempts to install an application via the Public App Store on company-supervised devices, or through any method on unsupervised devices, the end user receives a notification on their device. The user may need to sign in with an Apple ID and enter their password to complete the installation. Additionally, the user must select Install to proceed with the installation.
Network
In this category, device’s network settings can be configured, like Proxy and Wi-Fi networks. Multiple Wi-Fi networks can be added, but only one proxy.
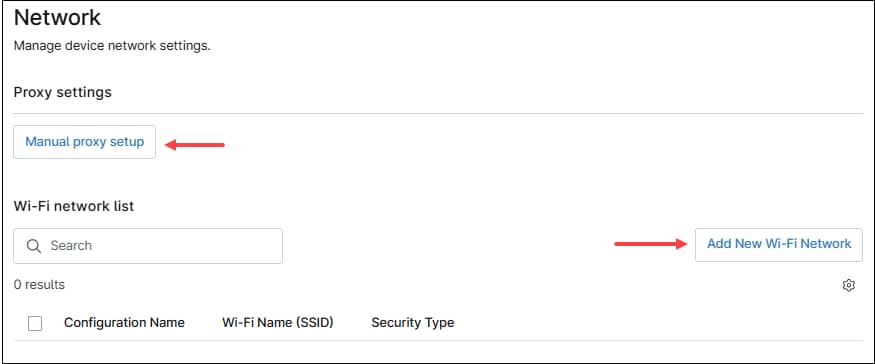
Proxy
Use the Manual proxy setup button to configure proxy settings. This action will open the Manual Proxy Setup dialog box.
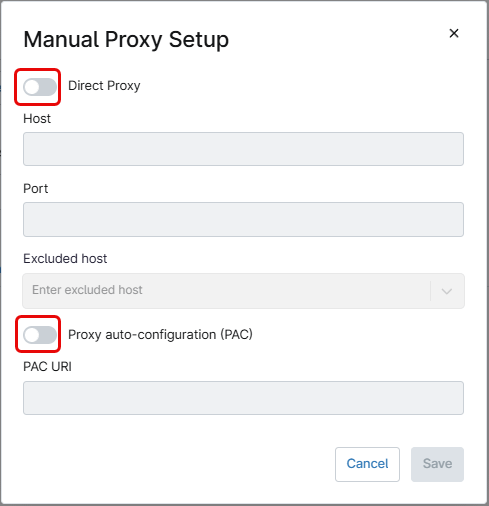
Turn on the Direct Proxy switch to manually enter the proxy configuration information – Host name and port.
Turn on the Proxy auto-configuration (PAC) switch to enter the URL for the PAC file.
Host names can be excluded from the proxy by writing the name under the Excluded host field and pressing enter.
After entering the information, click the blue Save button. This will add the proxy settings used by the mobile device. Once added, the information can be edited or removed.
Wi-Fi Networks
Use the Add new Wi-Fi Network button to configure a new Wi-Fi network. This action will open the iOS policy Wi-Fi Network Dialog Box, then follow the next steps to configure a new Wi-Fi network.
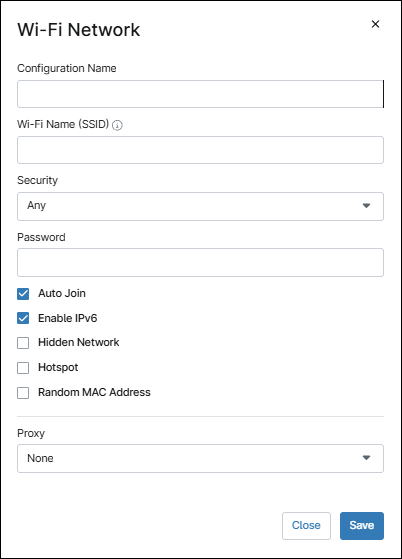
- Enter a configuration name (a friendly name of your choice to distinguish this Wi-Fi network).
- Enter the SSID.
- Under Security, select the encryption method, options are: ‘WEP-PSK‘, ‘WPA-PSK‘, ‘WPA2-PSK‘, ‘WPA3-PSK‘, Any or None.
- Enter the password.
- Select the additional options if required (Auto Join, Enable IPv6, Hidden Network, Hotspot or Random MAC Address).
- Select the proxy method (Auto, Manual or None).
- Click Save.
- The new Wi-Fi network configuration will appear on the list. This network can be edited or removed by selecting it using the check mark to the left of the name.
OS updates
This category defines how users can install software updates and defines enforced OS versions.
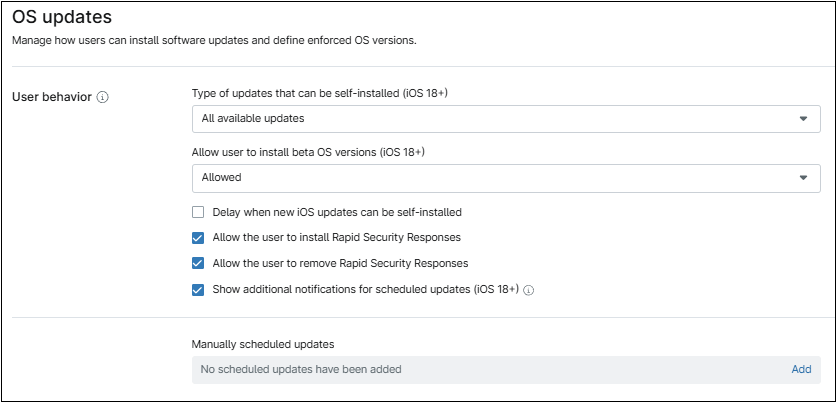
- Type of updates that can be self-installed (iOS 18+). This option controls what updates will be installed. Options are: All available updates, Highest available update, and Lowest available update.
- Allow user to install beta OS versions (iOS 18+). This option controls the installation of beta OS versions. The available settings are: Allowed, Always On, and Always Off.
- Delay when new iOS updates can be self-installed. This option delays the availability of a released operating system (OS) update for the device. When enabled, you can specify the delay duration, which can range from 1 to 90 days.
- Allow the user to install Rapid Security Responses. If enabled, critical security updates released by Apple will be installed. RSRs are released more quickly than traditional OS updates.
- Allow the user to remove Rapid Security Responses. This option controls the ability for a used to remove RSRs.
- Show additional notifications for scheduled updates (iOS 18+). If enabled, users will receive daily notifications for updates scheduled in the future. If disabled, users will only receive notifications beginning one hour before the scheduled deadline.
- Manually scheduled updates. This option is used to enforce software updates. An approval date is set to give the user the option to install the update voluntarily. If the user does not install the update by the approval date, an enforcement date ensures the update is installed automatically.
Location tracking
This category enables location tracking and specifies the accuracy and frequency of location updates.
Follow the instructions below to enable location tracking.
- Click Enable.
- Select accuracy: Balanced mode is accurate to within 100 meters and consumes less battery. High Accuracy mode captures the best available location but consumes more battery.
- Select the location update frequency: Distance traveled means a location update is sent to the server after the device moves a specified distance (500 m, 1000 m or 5000 m). Time based means a location update is sent to the server based on time. Options are five minutes, 30 minutes, one hour, six hours, 12 hours or 24 hours.
- Click Save.
Note: Location tracking requires the NinjaOne Assist app to be installed and active on the device, with Location Services enabled. The app must also be added to the policy as a managed application with Forced Install selected.