High risk software audit is a broad term encompassing various software applications that pose significant potential threats to systems, data, or users. Let’s explore the characteristics of High-Risk Software:
- Vulnerability: Outdated software, software nearing end-of-life (EOL), or software with known security vulnerabilities are targets for attackers.
- Unreliable or unmaintained: Software with a history of bugs, crashes, or lack of updates, increasing the risk of system instability and potential security vulnerabilities.
- Poor coding practices: Software developed with poor coding practices, making it more susceptible to exploitation and security flaws.
- Excessive permissions: Software that demands excessive access permissions on a system, potentially granting unrestricted access to sensitive data or functionalities.
- Unauthorized or unknown source: Software downloaded from untrusted sources or with unknown origins, often harboring malware, or other malicious code.
- End-of-life (EOL) software: Software no longer receiving security updates or support from the vendor, leaving it vulnerable to known and emerging threats.
How to Conduct a High Risk Software Audit?
Conducting a high-risk software audit involves a systematic approach to identifying and mitigating potential risks. Here are the key steps involved:
1. Preparation:
a) Define Scope: Determine which systems and software will be included in the audit.
b) Gather Information: Collect information about installed software, licenses, and vendor support agreements.
c) Develop Checklist: Create a checklist to assess various risk factors like software version, vendor support status, and access controls.
2. Execution:
a) Discovery and Inventory: Utilize tools to discover and list all installed software across your network.
b) Vulnerability Scanning: Run vulnerability scans to identify known security weaknesses in the discovered software.
c) License Verification: Verify the validity and compliance of software licenses across your organization.
d) Access and Control Review: Evaluate user access controls and privileges associated with high-risk software.
3. Reporting and Remediation:
a) Document Findings: Compile a comprehensive report outlining the identified high-risk software and associated risks.
b) Prioritize Remediation: Based on risk severity, prioritize actions like updating, replacing, or removing high-risk software.
c) Implement Remediation: Implement corrective actions based on the prioritized list.
How Can I Find if I Have Any High Risk Software Installed?
Here’s a step-by-step approach to identifying high-risk software on your devices:
1. Define the Risk Criteria: vulnerable, unpatched, unauthorized, non-compliant, EOL, etc.
2. Compile a list of all installed software on every endpoint, including the OS.
3. Compare every software piece against the risk criteria.
4. Flag each software found that matches the risk criteria as high-risk.
These tasks can be performed manually when the number of endpoints is low; however, as you scale, the job becomes very challenging.
How Can NinjaOne Help in The High Risk Software Audit Process?
NinjaOne can significantly aid in conducting high-risk software audits through several functionalities:
- Software Inventory: Manually identifying and listing all installed software across numerous devices can be a tedious and error-prone process. NinjaOne automates this task, providing a comprehensive and accurate inventory of all software on managed endpoints, saving significant time and effort.
- Patch Management: NinjaOne simplifies patch deployment, ensuring timely updates for software identified as high-risk during the audit. This proactive approach helps organizations swiftly address vulnerabilities and minimize the window of risk exposure.
- Harden Endpoints: NinjaOne integrates with security software, this eliminates the need to switch between different tools, streamlining the process of hardening and securing endpoints.
- Reporting and Analytics: NinjaOne generates customizable reports that track the progress of the audit and identify trends in software usage and associated risks. These reports provide valuable insights that can be used to inform future security decisions and resource allocation.
In essence, NinjaOne acts as a central hub, automating tedious tasks, consolidating data from various sources, and streamlining the overall high-risk software audit process, making it efficient and effective for organizations.
How Can NinjaOne Help in Identifying High Risk Software?
NinjaOne is an excellent tool that can help to identify high-risk software.
You can customize your device list by showing the OS by name, OS build number and OS release ID, then you can sort the list by these fields, this way you can easily identify Operating systems and pick the ones that are high-risk targets. You can also filter the list to only show the OSs you´re looking for.
With NinjaOne. you can create customized reports. It´s easy to create a software inventory report with all the applications on all endpoints of an organization. This report can be exported to a spreadsheet to manipulate it and find high-risk applications more easily.
If you have a list of identified high-risk software names, you can create a filter and let NinjaOne look for the endpoints having this software installed.
What Are The Benefits of Using NinjaOne For The High Risk Audit Process?
Here are some of the multiple benefits of using NinjaOne for managing high-risk software.
- Centralized Inventory:
Obtain a comprehensive overview of all installed software across managed endpoints. Easily identify high-risk applications within your network.
- Automated Scanning:
Utilize predefined criteria to automatically detect high-risk software. Reduce manual effort and enhance detection accuracy. Detect and alert on new software installations.
- Real-Time Monitoring: Continuously monitor for new software installations and potential violations. Swiftly respond to prevent high-risk software usage.
- Minimize manual workflows:
Automate routine tasks related to high-risk software management. Free up IT staff for more strategic initiatives.
- Automated Reporting:
Generate reports to track high-risk software usage trends. Identify recurring issues and measure the effectiveness of your management strategies.
In conclusion, conducting high-risk software audits is crucial for identifying vulnerabilities, assessing compliance, and mitigating potential risks.
NinjaOne provides a powerful set of tools for automated patching, continuous monitoring, inventory reporting, and integrations with security software.
By leveraging NinjaOne, organizations can enhance the effectiveness and efficiency of their high-risk software audit processes, ultimately improving the security of their software systems.
Operating System Discovery Strategy
The following examples show how to list the different operating systems on your endpoints.
- Go to the Devices dashboard, you can see that by default, the operating systems are not included in the list.
- Click the Table Settings icon, on Columns (Add column to board), and add the OS Name, OS Build Number, and OS Release ID fields.
- On the Sort By field, select OS Name, then Click Save.
The list will now show the Operating System details and now it´s easy to see if there are any that are EOL
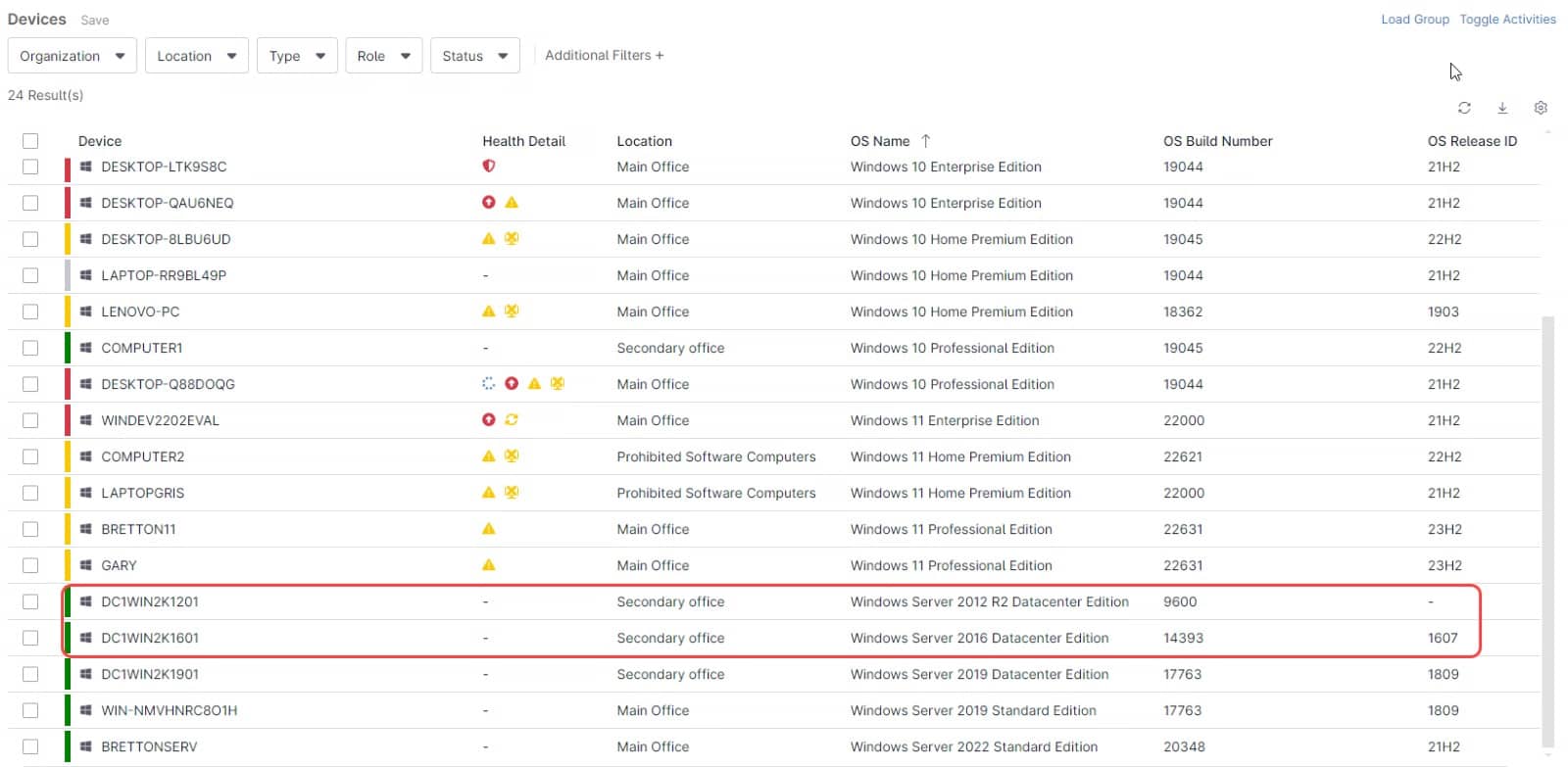
Another way to find an EOL operating system is by applying filters. Let´s use this method to find the endpoints with the Windows server 2012 and Windows 2016 OS installed.
- Go to the Devices dashboard, click on Additional Filters. Choose OS (with editions).
- A dialog box opens, from there, choose the OS you´re looking for, in this case, Windows Server 2012 R2 Datacenter. Then, from the same drop-down, select Windows Server 2016 Datacenter edition (you can keep adding as per your preferences).
- Click anywhere outside of the dialog box to close it. Now, the list will only show the devices that meet the selected OSs.
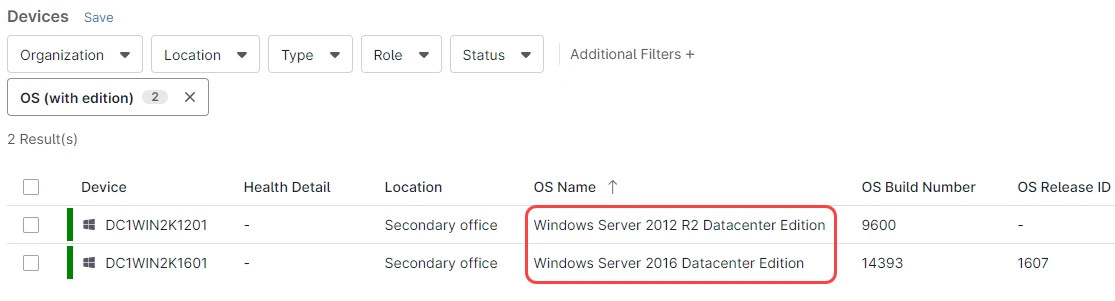
Note: The drop-down menus auto-populate with the OS names and editions present on your tenant.
Find a Target Software Strategy
Sometimes, you already know about one or more software names, and you want to find where they are installed. Follow the next steps to find the endpoints having a software name installed.
- Go to the Device dashboard, click on Additional Filters.
- From the drop-down select Software Inventory, a dialog box appears.
- From there, select All time, then, select Contains, then select Any of the software. Click on Add and add the software name, here you can add more than one name. Only the names found in the list can be added, but don´t worry, the list is huge and includes any software currently installed on systems in the enviornment.
After adding all the names, click Close. The list of devices having any of the software added will be displayed.
Moreover, once the above filter has been applied, this filtered list can be saved as a device group, this group is dynamic and whenever any devices fall (or stop falling) into the condition parameters, the list will be updated.
You can consult this group any time or create a report. This report can be run on demand or at a scheduled time.
Generate a Software Inventory Report Strategy
It´s possible to use the NinjaOne reporting tool to generate a software report for all the endpoints. This report can be group-wide, organization-wide or tenant wide.
There´s a link at the end of this document: “More on Software Inventory Reports”. This page has an explanation on how to generate this kind of report.
