Unleash Seamless IT Monitoring Software with NinjaOne: Your Ultimate Solution for Effortless Maintenance
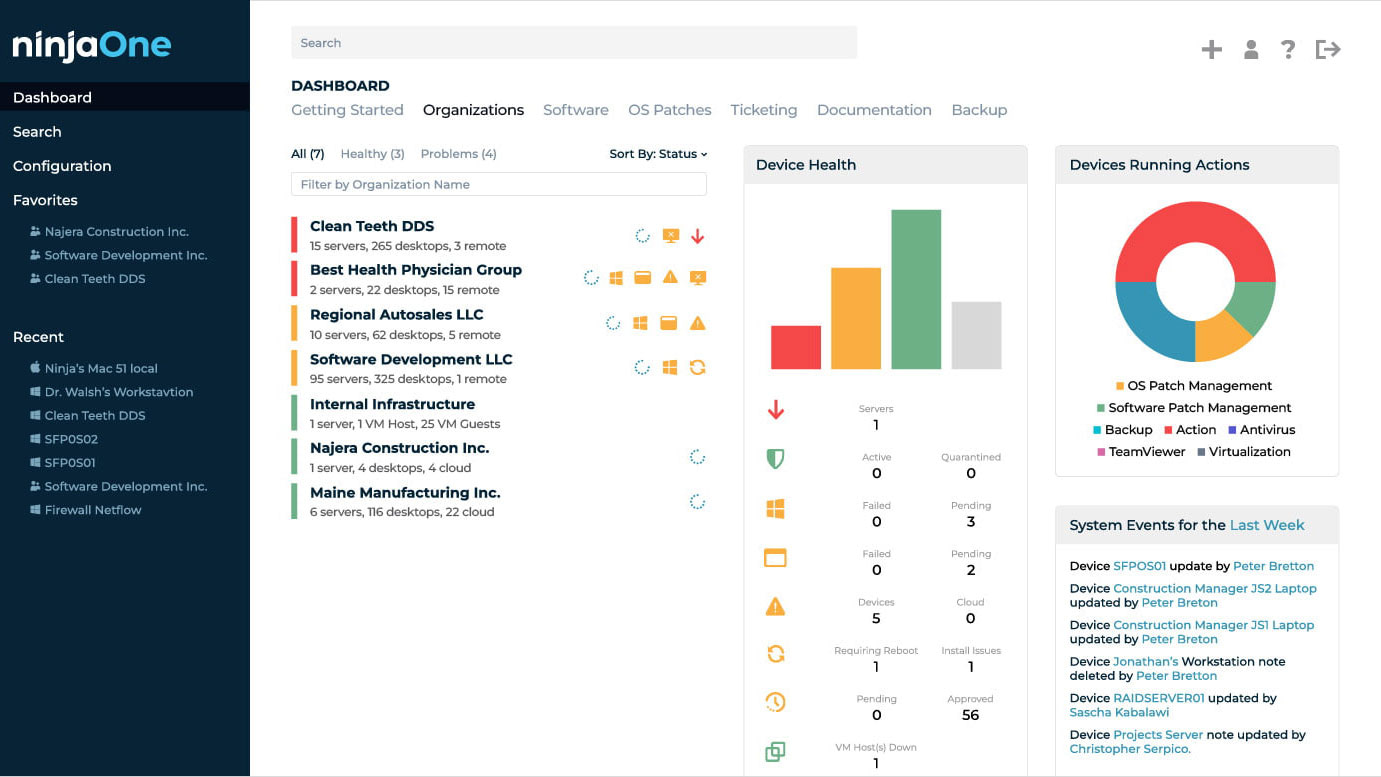
Explore the Benefits of NinjaOne IT Monitoring
Streamlined Operations
Proactive Problem Resolution
Cost-Efficient Scalability
Comprehensive Visibility
Compliance Made Easy
The future of IT Monitoring Software with NinjaOne
Centralized Dashboard
Automated Patch Management
Endpoint Management
Customizable Reports
Endpoint Security
Powerful Integrations
Asset Discovery and Inventory
Policy Management
Transform IT Monitoring: NinjaOne Simplifies Maintenance Effortlessly!
Efficient Patch Management
Swift Remote Troubleshooting
Simplified Compliance Audits
Ready to redefine the way you manage IT?
IT Monitoring Software FAQs
What is IT monitoring software?
IT monitoring software is a crucial tool for businesses, ensuring the continuous surveillance of their IT infrastructure, networks, and systems. It allows organizations to track the performance, health, and availability of hardware, software, and network components in real time. NinjaOne, specifically, goes beyond traditional monitoring by providing features such as automated alerts, centralized management, and comprehensive insights. With NinjaOne, you can effortlessly oversee your IT environment, detect issues promptly, and ensure optimal performance, all while benefiting from the platform’s user-friendly interface and streamlined maintenance processes.
What is an example of IT monitoring?
IT monitoring involves the utilization of advanced software tools for the continuous tracking and analysis of vital components within an organization’s infrastructure. This includes monitoring real-time device health metrics, performance analytics, security event logs, and system alerts. Employing this technical approach ensures ongoing surveillance and proactive management, contributing to optimal operational efficiency and security.
How do you monitor remote endpoints?
NinjaOne effectively monitors remote endpoints through the deployment of lightweight agents, ensuring continuous tracking of device health. It automates patch management, offers customizable alerts, provides in-depth performance analytics, enables automation, and facilitates secure remote access. These features collectively contribute to the streamlined and secure management of remote devices.
Related Resources
Data Protection Plan: Guide & 8 Steps for Creation
Learn about our recommended plans for essential safety and security of data within all organizations.
Data Protection Methods for IT & MSP Teams
Read about which data protection methods can help prevent data loss disasters from occurring.
The Key Principles of Data Protection
Discover what data protection is and how varying laws and regulations apply to companies doing business throughout the US, Canada, and the EU.


