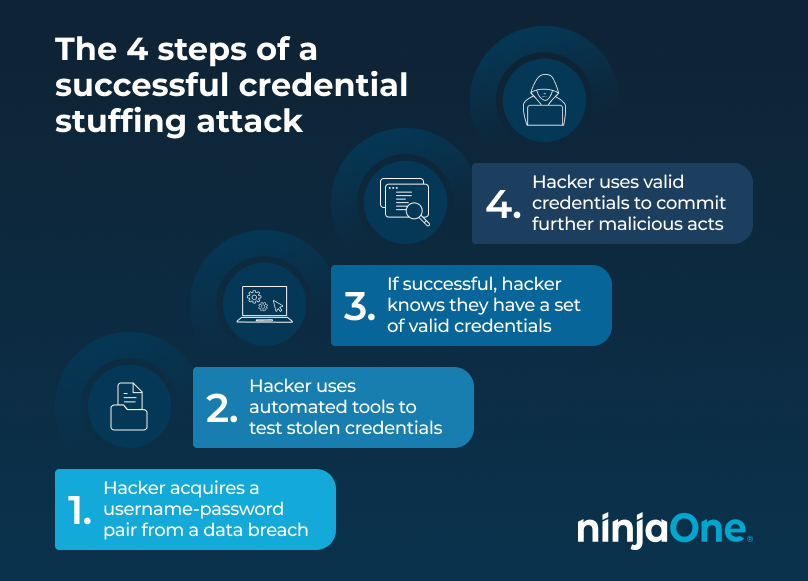
Credential stuffing is a form of cyberattack in which threat actors use collected credentials, such as your username and password, to gain fraudulent access to your accounts. Unlike brute force attacks, which guess your passwords using “encyclopedias” of common word combinations, credential stuffing uses known valid credentials from data breaches.
Credential stuffing is also different from credential dumping. Whereas the latter uses stolen credentials to access devices in the same network, the former injects stolen username and password pairs into various accounts that are known to be owned by you.
For example, if a hacker knows that you use the username-password pair A for account A, they will use the same pair A for accounts B, C, and so on. This highlights the inherent vulnerability in using the same password for different accounts: If a hacker gains access to your password, all accounts that use the same password are now compromised.
Minimize the risk of credential stuffing by understanding the top 5 IT security fundamentals.
How does credential stuffing work?
Credential stuffing is one of the most common cyberattacks, partly due to its simplicity.
Once a cybercriminal obtains your credentials, either from a data breach, phishing attack, or password dump site, they will then use automated tools to test the stolen credentials against all known accounts owned by you. If they are successful in accessing your account, they will see that they have a set of valid credentials.
From there, the possibilities are endless: cybercriminals can use these valid credentials to perform other malicious acts, such as making false purchases, stealing your credit card information and other sensitive data, or using your account to send phishing emails.
Is credential stuffing effective?
Credential stuffing focuses more on quantity than quality. Similar to “throwing spaghetti at the wall and seeing which one sticks,” it has a lower success rate than a more targeted attack, such as spear phishing. That said, it is still quite effective in accessing hundreds of thousands of user accounts yearly—especially because many people re-use the same username-password pair for multiple accounts.
The numbers speak for themselves: 14% of all data breaches involve the exploitation of vulnerabilities as an initial access step, particularly with weak or known username-password pairs. (2024 Data Breach Investigations Report, Verizon). More alarmingly, 93% of organizations report having two or more identity-related breaches in 2023, with machine identity (which includes credentials) as the riskiest identity type (Forbes, 2024).
Credential stuffing continues to be a major cybersecurity threat for organizations and individuals alike. To grasp the inherent threat of credential stuffing, just think about how many accounts you own that use the same username and password, and then consider how many millions of people do the same thing. This explains why 35,000 PayPal accounts were compromised by credential stuffing in 2023 and why Okta has alerted its customers against new credential stuffing attacks.
How do you detect credential stuffing?
Unfortunately, credential stuffing is difficult to detect. These attacks are typically launched through botnets and other automated tools that launch rogue requests that look legitimate. It may be challenging to differentiate between legitimate requests and credential-stuffing attempts. Still, one of the telltale signs of an attack is if you are suddenly having difficulties logging into your account, even when you’re confident you have the proper credentials.
While many websites notify you when a suspicious login attempt is made, it is still recommended that you take preventative measures instead. For example, a pre-emptive credential management strategy is easier to implement and more cost-effective than trying to fix a data breach.
NinjaOne’s Credential Exchange helps you run scripts using custom credentials.
How do you prevent credential stuffing?
One of the most effective ways to prevent credential stuffing is to use a unique password for every account you own and use. Consider using a password manager if you are worried about forgetting your passwords—and never write your passwords down on a piece of paper that can be easily stolen. Practice other healthy habits to maintain your cybersecurity hygiene, such as:
- Enable multi-factor authentication (MFA). To access a system or account, MFA requires users to identify themselves in multiple ways, including face ID and fingerprint scanning.
- Conduct regular cybersecurity training. It is crucial that all team members in your organization, not just your IT team, learn to secure their login credentials. As an individual, take proactive measures to update yourself on the latest cybersecurity strategies.
- Consider proactive IT support. If you are an MSP, consider implementing proactive IT support for all your end-users in case of a data breach.
NinjaOne mitigates the risk of credential stuffing
NinjaOne offers a more seamless, reliable, and secure way of protecting your credentials through its Credential Exchange tool. With the platform, you can run scripts without endpoint permission issues while gaining the highest-level privileges for patching with domain admin credential selection.
If you’re ready, request a free quote, sign up for a 14-day free trial, or watch a demo.

