Phishing is a form of social engineering that tricks users into clicking on malicious links or navigating fake websites to gain personal information (Cybersecurity & Infrastructure Security Agency). While there are many forms of phishing, spear phishing is one of the most dangerous forms to be aware of.
Unlike other forms of phishing, spear phishing is a targeted attack on an individual, usually in the form of an email supposedly from a trusted sender. A spear phishing attack aims to infect a device with malware or trick the recipient into some other action that will benefit the attacker, such as divulging personal information or transferring money to a fake bank account.
Spear fishing may be more time-consuming for cybercriminals, but it is also the most lucrative. For example, the Federal Trade Commission recently announced that nationwide investment scams in 2023 reached a whopping $10 billion—a 14% increase from 2022. Experts found that imposter scams, such as spear phishing emails, contributed to the rise. Sadly, they expect this number to only increase in the next few years.
This has played a significant role in the White House reaffirming its commitment to creating a “defensible, resilient, and values-aligned digital ecosystem” for the American government and all privately held corporations (2024 Report on the Cybersecurity Posture of the United States). One of its main initiatives is improving protection against cyber attacks, such as spear phishing.
Know the top vulnerabilities affecting IT companies today.
What is spear phishing?
Spear phishing is a highly personalized and calculated cyberattack that targets individuals or companies. Typically, these attacks are carried out through phishing emails that appear legitimate and encourage the recipient to share sensitive information with the sender. Most spear phishing emails are crafted to steal financial information, such as credit card details.
However, with the ever-evolving geopolitical landscape, spear phishing attacks now include infecting devices with malware, perpetuating ID theft, or even committing financial fraud. The stolen information is then resold in the black market or used as bait for you to pay the criminal.
Phishing vs. spear phishing vs. whaling
Phishing, spear phishing, and whaling are common types of cyber attacks, but some differences exist.
Phishing
Phishing uses fraudulent emails, SMS, or websites to lure people to divulge sensitive information. Compared to spear phishing and whaling, phishing is the least sophisticated, prioritizing quantity over quality. Phishing attacks are usually incredibly generic and sent to many people simultaneously. One good way to detect a phishing email is to check the salutation. If you’re addressed simply as “Hello, user!” or “Hello, customer!”, keeping your guard up may be a good idea.
Spear phishing
Spear phishing focuses on quality, sending highly personalized emails to targeted individuals. Because of the amount of research required to pull off a successful attack, spear phishing is less common but, arguably, more effective.
Whaling
Whaling uses the same personalized strategy as spear phishing attacks but only targets higher-level management and C-level executives. There is some debate regarding whether whaling is the same as spear phishing, and for the purposes of this article, we will lump whaling and spear phishing together.
Why is spear phishing so dangerous?
At the onset, spear phishing seems easy to spot. A suspicious-looking email? No problem! Someone asking for personal information? Pfft, block immediately.
But the truth is that spear phishing attacks are much more sophisticated than that. Cybercriminals conduct extensive research on you and your company. Using any information they can find (including from your public social media accounts), they can create an exceptionally well-crafted and tailored attack to dupe you into thinking that what you’re reading is from a legitimate source.
As a result, even high-ranking managers and C-suite executives can find themselves opening e-mails they feel are safe.
How do spear phishing attacks work?
There are four steps to creating a spear phishing scam.
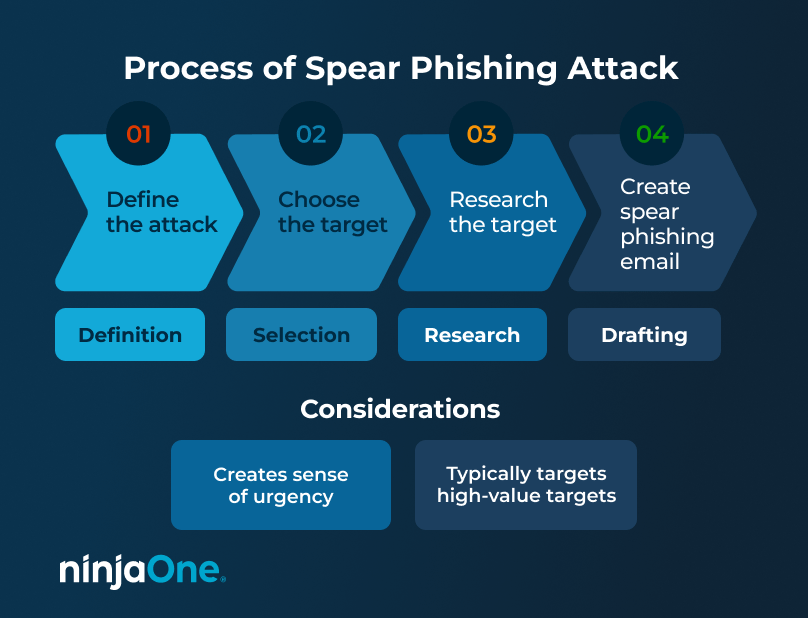
First, cybercriminals define their attack. This involves knowing what information they need and how to create the email to gain this data. For example, if the attacker wants your credit card information, they need to determine the best way to get it from you—perhaps by posing as your bank.
From there, they would create a list of possible targets and begin narrowing it down to the most high-value one. It’s worth noting that the term “value” here can mean different things. This is not only a person with the most to lose (though it’s a considerable factor). Instead, it’s also a target who would be easily manipulated and tricked into performing the desired action. Keep in mind that cybercriminals want the easiest way to win unless the financial reward is just too good to turn down.
The third step is research, which is the longest part of the process. Cybercriminals spend inordinate amounts of time researching everything about you, from your work to your pet to even your friend’s cousin’s preschool playmate. Anything that can be used to make you believe the legitimacy of the scam will be gathered. This information will be used in step four: creating the spear phishing email.
The email will be carefully worded to sound as authentic as possible. It will likewise carry a sense of urgency so you can respond immediately with certain details or download a specific file. Some spear phishing emails may direct you to a fake website for your bank, where you will be prompted to log in with your correct username and password.
Examples of spear phishing emails
There are some phishing email examples to be aware of.
1. Business compromise emails
According to the FBI’s Internet Crime Report, potential losses due to Internet crime exceeded $12.5 billion in 2023 and were expected to be even more significant in 2024. Nationwide, the most frequently reported crime was phishing schemes, with the most common type being some form of compromised business email.
In this type of attack, a hacker poses as someone from work (maybe a colleague, boss, or vendor) and asks you to perform an action, such as wiring money or changing bank account details. This is also known as email spoofing.
Real-world example: One of the most famous examples is Evaldas Rimasauskas, who manipulated big-name companies (including Facebook and Google) to pay around $121 million in fake invoices.
2. Whaling
Whaling attacks senior employees to gain sensitive information about a company or manipulate them into sending high-value wire transfers. It gets its name, arguably, from “Moby Dick”, or going after the “big fish” for the ultimate prize. It’s worth noting that while all spear phishing attacks are targeted, whaling focuses on prominent figures with essential functions, such as the CEO or COO.
Real-world example: Labeled as one of the biggest cyber frauds in Pune, an Indian real estate company lost around Rs 4 crore (around $600,000) through whale phishing.
3. CEO fraud
Also known as executive phishing, CEO fraud impersonates a high-level executive to trick team members into making unauthorized wire transfers or sharing sensitive data with the hacker. Unlike whaling, which targets the C-level executive, CEO fraud targets lower-level employees to act under the presumption of authority.
Real-world example: A finance worker wired $25 million to a fraudulent account after being “told” by his Chief Financial Officer to do so. It turns out that the COO was a deep-faked AI.
How to identify a spear phishing attack
The best way to prevent a spear phishing attack is to read the email before clicking any link or opening any attachments. Unfortunately, many users assume an email is safe without double-checking the sender’s validity or content. This is especially true if the email is supposedly from a high-ranking officer. Hackers use this to their advantage: They are banking on the fact that you won’t question a personalized or official-looking email.
That said, there is no one way to detect a spear phishing attack. It’s always best to trust your judgment. If you feel something is wrong, there is no harm in asking your director, supervisor, or whoever allegedly sent you that email if the information provided is correct.
Some common red flags to look out for include:
- Incorrect or wrongly spelled email address
- Spelling or grammar mistakes
- An unusual sense of urgency
- Unusual dates or times (such as a weekend or holiday)
- Links that don’t match the domain
- Requests sensitive information
- Attempts to panic you
Preventing a spear phishing attack
1. Conduct security awareness training
Whenever possible, provide security awareness training for all employees, not only for your IT teams. Every team member must develop the skills to spot, avoid, and report a phishing email. You may also want to consider a phishing email simulation so they can gain real-life experience of what a phishing email may look or sound like. The goal is to build a culture of security.
NinjaOne partnered with Webroot to produce an educational webinar on how MSPs can prevent phishing.
2. Keep yourself up-to-date with the news
Cyber threats continue to evolve each year. It is vital that you keep your ears to the ground and become aware of the new ways hackers create spear phishing attacks. One of the best and most legitimate ways to do this is to regularly check the official website of the Cybersecurity & Infrastructure Security Agency (CISA).
3. Implement security tools
It is important to use a remote monitoring and management software solution that can automatically patch, configure, and integrate remote services in a single platform. NinjaOne, for example, is a trusted endpoint management company that automates the hardest parts of IT to increase productivity, reduce security risk, and lower IT costs from day one. In addition, NinjaOne is a SOC2 Type-2 certified platform and enforces MFA on all accounts. SSO is also available in all packages and at all price points.
Stop spear phishing from damaging your company
It is impossible to stop spear phishing completely, but there are ways to mitigate its risk and potential impacts. Aside from regularly conducting proactive investigations to find suspicious emails and educating employees on the various types of spear phishing, it’s important that you work with a trusted vendor known for its security and performance.

