Viewing vulnerable systems: a system that possesses weakness that attackers can exploit to gain unauthorized access, steal data, or disrupt operations. In other words, it’s a system susceptible to cyber-attacks. A system missing critical, or security updates is an example of a vulnerable system.
Unfortunately, in our world we are exposed to cybercriminals who are constantly trying to find new ways to get into our systems, which requires proactive measures to prevent such attacks, like antiviruses and firewalls. We can consider that a system that lacks these measures is also a vulnerable system.
How Can I Detect a Vulnerable System?
The manual method is logging in to the endpoint and checking firewall settings, antivirus software, installed patches, patching setting, etc. As the number of endpoints increases, this task becomes complicated. Management software facilitates this kind of task by automating and alerting about vulnerabilities found.
Viewing Vulnerable Systems: How Can I See Vulnerable Endpoints With NinjaOne?
There are different endpoint weaknesses that can be easily seen with NinjaOne.
1. Finding patching weaknesses.
a) Finding endpoints with patching disabled. If patching is disabled on an endpoint, it will never be patched, a situation that needs to be corrected. Follow the next instructions to find such devices.
- Open the device dashboard.
- Go to Additional Filters and from the drop-down menu, select OS Patching Enabled.
- Go to the Type filter and from the drop-down menu, select the type of endpoint you want, for instance, Windows Server.
- Any endpoint listed has patching disabled and corrective action must be taken.
b) Finding endpoints with patch scan that is old. Patch scan is a critical part of patching, if an endpoint is found not running such scan, it´s a red light that needs to be addressed. Follow the next instructions to find devices with patch scan older than two weeks.
- Open the device dashboard.
- Go to Additional Filters and from the drop-down menu, select Last OS Patch Scan. Then select Before and then select a date two weeks prior to now.
- Go to the Type filter and from the drop-down menu, select the type of endpoint you want, for instance, Windows Server.
- Any endpoint listed has two weeks without running patch scan, and corrective action must be taken.
2. Finding antivirus software missing.
Normally, the antivirus software should be the same across the company, this software can be detected by NinjaOne, but in the same way, if this software is missing, that can be detected too. Follow the next steps for an example of how to do it.
- Go to the device dashboard.
- Go to Additional Filters and from the drop-down menu, select Software Inventory. A dialog box will open.
- On the dialog box, select All time.
- Then, select Does not contain, then select All,
- Then click Add, a new dialog box will open and from there, select the software name, for instance, McAfee. (NinjaOne auto populates the software drop-down, so you can be sure your software will show up). Then click the blue button Add on the lower right of the dialog box.
- If it is known that there are more antivirus solutions installed in your company, you can continue adding the names. Click close once done.
- After these filters have been applied, a list of devices missing the antivirus will show up, including servers, switches, mobile devices, etc. To narrow down the search to only Windows desktops and laptops, for instance, go the Type, and select Windows Desktop, and select Windows laptop.
Can I Get Alerts About Vulnerable Endpoints With NinjaOne?
Yes, using policies and conditions you can get alerts on vulnerabilities. There are multiple options, let´s go through some examples.
1. Get alerts on Windows Firewall Service down.
NinjaOne provides a native template for the Windows Firewall Service down. Follow the next instructions to enable it in the policy of your preference.
a) Go to Administration then Policies, then Agent policies.
b) Click on your preferred policy. The policy editor will open.
c) Click Use Template.
d) Under Security, select Firewall Service Stopped. A message saying that the condition has been added will show up.
e) At this point you can keep adding other conditions or Close.
f) By default, this condition does not alert. Using the policy editor, you can change the severity, priority, alerting options, etc.
g) Click Save at the top right corner of the screen. Enter your MFA method answer, then close.
There are several other templates you can use to get notified on other Windows Firewall events, like Windows Firewall settings changed, Windows Firewall Failed, Changes made to Windows Firewall Exceptions, you can use them to get the alerts that best fit your needs.
Similarly, there are specific templates to alert about known antivirus services down, like Webroot, ESSET, Windows Defender, Trend Micro, Kapersky, Symantec, etc.
2. Get alerts on Windows Firewall disabled.
This is a different method for getting alerts, using custom fields and a PowerShell script for triggering condition in a policy.
a) Setup a new Custom Field called FirewallStatus.
- Go to Administration, then Devices, then Global Custom Fields.
- Click Add, then choose Field. A dialog box will appear.
- Fill out the Label, in this case, write FirewallStatus. The field name will autopopulate.
- Choose the Field type, in this case, multi-line.
- Click Create.
- Assign the proper permissions, for this case, Technician is read-only, Automations and API are read-write and Definition Scope is Device.
- Optionally fill out the description, ToolTip Text, footer text and click save.
b) Write a script that pulls data from the endpoint and stores the data in our custom field. We will use the Ninja-Property-Set command, which is the NinjaOne’s Powershell command to set a custom field to a specific value. The script will return the device´s firewall status in the next format:
Domain True/False
Private True/False
Public True/False
- Go to Administration, then Library, then Automation Library.
- Click Add, then choose New script. A dialog box will appear.
- On the right side, fill out the script´s properties (see following screenshot).
- On the left side, paste the next two lines: Get-NetFirewallProfile | Format-Table Name, Enabled -HideTableHeaders | Out-String Ninja-Property-Set firewallStatus $firewallstatus
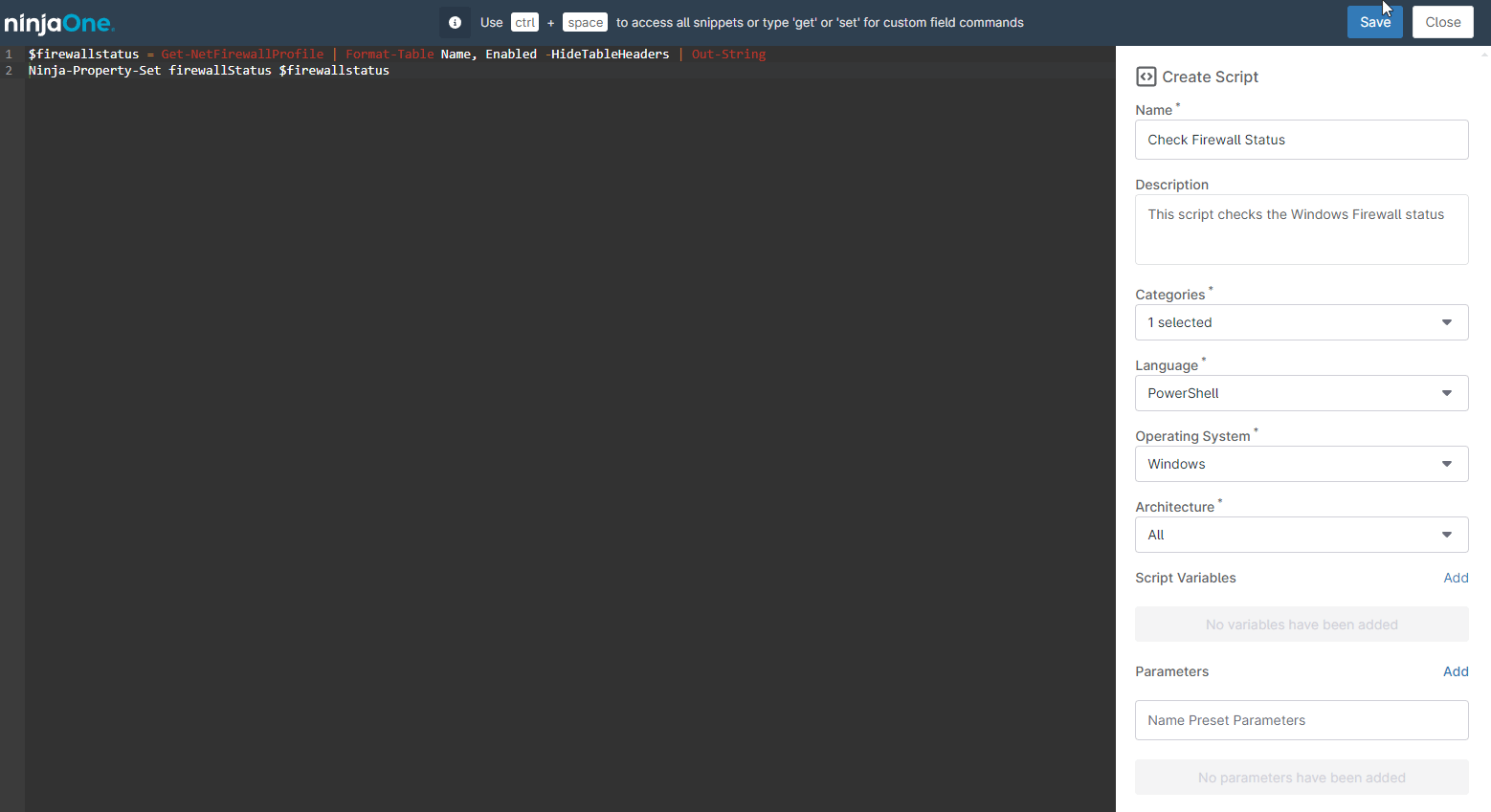
- Click Save, enter your MFA method answer and close.
c) Run the script at least once for all devices in the policy, which can easily be setup with a scheduled task or automation.
- Go to Administration, then Policies, then Agent policies.
- Click on your preferred policy, The policy´s settings will appear
- Select Scheduled Automations, then Add a Scheduled Automation
- Give it a Name, optional description, and fill out the schedule and notification settings as desired.
- On the top right click Add, the automation Library will appear
- Select the Check Firewall Status script we just built
- Finally click add to create the automation.
This automation will run the script at the designated time and fill in the custom field we created.
d) Add a policy condition that checks the FirewallStatus custom field, if the word “False” is present, that means that one or more firewall profiles is disabled, and an alert should be triggered.
- Go to Administration, then Policies, then Agent policies.
- Click on your preferred policy, The policy´s conditions will appear.
- Click Add a condition. A dialog box will open.
- Click Select a condition. A new dialog box will open, select Custom fields from the drop-down.
- Click the first Add from top to bottom.
- On the left side, select Firewall Status.
- On the right side, select contains.
- On the next empty box. Type False.
- Click apply.
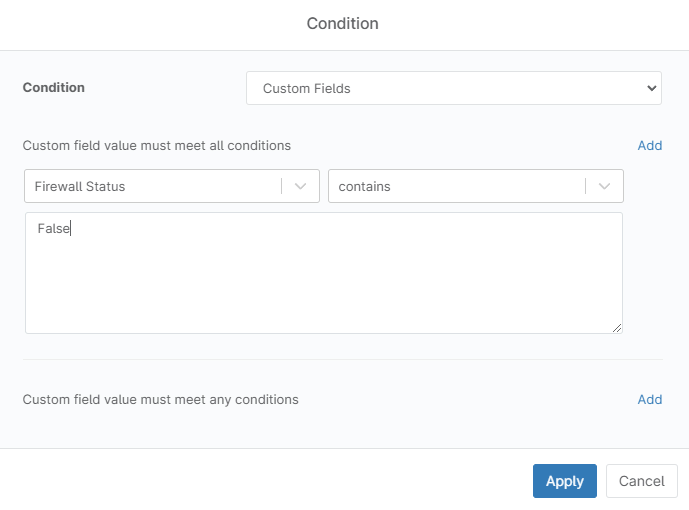
- Fill out the condition name, severity, priority, and notification options according to your preferences, then click Apply.
- Click Add.
After these three steps, any device linked to this policy and having any Windows firewall profile disabled, will create an alert, according to the preferences you chose in the condition.
