Threats & Patches
System Health Policy
Vulnerability Management
Patch Management
Patch Settings
Patch Deployment
Asset Management
Inventory
Application Management and Control
Prohibited Software
- Jorge Caamano
- Last updated
Importance of Network Inventory Scanning
Network Inventory scanning is a critical component of network management, serving as the foundation for ensuring that all devices connected to a network are accounted for and effectively managed.
By conducting regular inventory scans, IT professionals can obtain a comprehensive overview of the network’s assets, including computers, servers, mobile devices, and software applications.
This visibility is essential for maintaining operational efficiency, as it allows for the effective allocation of resources, timely updates, and the identification of unauthorized devices that may pose security risks.
Moreover, inventory scanning plays a pivotal role in network security by identifying all devices connected to the network, including unauthorized or rogue devices. Regular inventory scanning also facilitates compliance with regulatory requirements by providing documentation of software usage and configurations.
Furthermore, inventory scanning facilitates compliance with various regulatory standards that mandate the management and protection of sensitive data.
By having a clear understanding of where data resides within the network and which systems have access to it, organizations can implement appropriate controls to safeguard this information.
Regular inventory scans help ensure that all assets are compliant with industry regulations, which is vital for avoiding legal penalties and maintaining the trust of customers and partners.
In conclusion, investing in robust inventory scanning tools and practices is essential for organizations seeking to maintain a secure, efficient, and resilient network environment.
How does Inventory scanning work?
Inventory scanning is based on network scanning, which is a technique that sweeps all hosts within a network for ping responses, ARP scans, and port scans. Since the possible number of hosts that can fit within a network is large, an automatic scanning tool is usually used. Scanning tools can be agent-based or agentless. The scan tool scans and discovers active hosts and services that appear as a result. IT administrators make decisions based on these results.
Does NinjaOne have an Network Inventory Scanning tool?
Yes, NinjaOne offers an agent-based scanning tool called Network Management Suite (NMS), that installs on a Windows computer within the network. This agent has a scanning tool and a monitoring tool that communicates with the endpoints and reports the status to the NinjaOne application. Follow the next instructions to download, install, run, and configure the NMS agent.
Prerequisite: Choose one Windows server within your network that will act as a monitoring device, this will be called the monitoring server.
- Download and install the NMS agent.
- From any NinjaOne dashboard, click the + sign in the top right corner of the screen.
- From the drop-down menu that appears, select NMS, the Add NMS device appears. Click the Download button, then close the screen.
- The file Ninja_NMS_Setup.exe is available in your Downloads folder. Copy this file to the monitoring server, and double click on it to run it. Follow the instructions to complete the installation, and at the end, restart the monitoring server to complete the installation process.
- Run and configure the NMS agent.
- After the monitoring server comes back online, the NMS agent will start automatically. The below screenshot shows the login screen.

- Enter the same credentials you use to login to the NinjaOne application, and click Sign in.
- From the drop-down menu, select your organization and click Register Organization, then confirm.
- The following Network Discovery screen will appear:
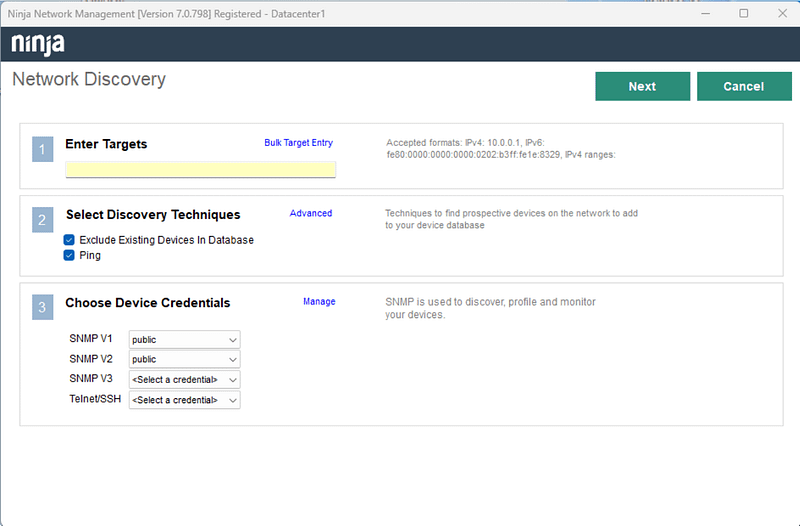
- Enter Targets.
- IPv4 or IPv6 addresses can be used. The allowed formats are:
- IPv4/subnet-mask, IPv4/suffix (CIDR format), IPv6.
- Ranges are allowed, separated by hyphen.
- If you want to scan more than one network, click on Bulk Target Entry, a dialog box will open and there you have the option to enter multiple network addresses, one address per row.
- Select Discovery Techniques.
- Exclude existing Devices in Database. Checkmark this field if you want to exclude devices already discovered by other means, like computer or mobile agents.
- Ping. Checkmark this field if you want to use ICMP to discover endpoints.
- By entering Advanced, you can:
- Fine tune the ICMP parameters.
- Add specific target TCP ports.
- Use DNS/NETBIOS to resolve the name of the discovered endpoint.
- Choose Device Credentials.
- Here you can enter the SNMP ports and credentials to use SNMP discovery.
- Once you have filled out the fields, click Next on the upper right corner, and the discovery will start. Once the discovery is done, click Next. A screen showing the new devices found will appear. Click Complete to add the new devices to the NinjaOne console.
- Now the new devices are visible on the NinjaOne console, and they are also visible on the NMS agent´s screen, as shown in the screenshots below.
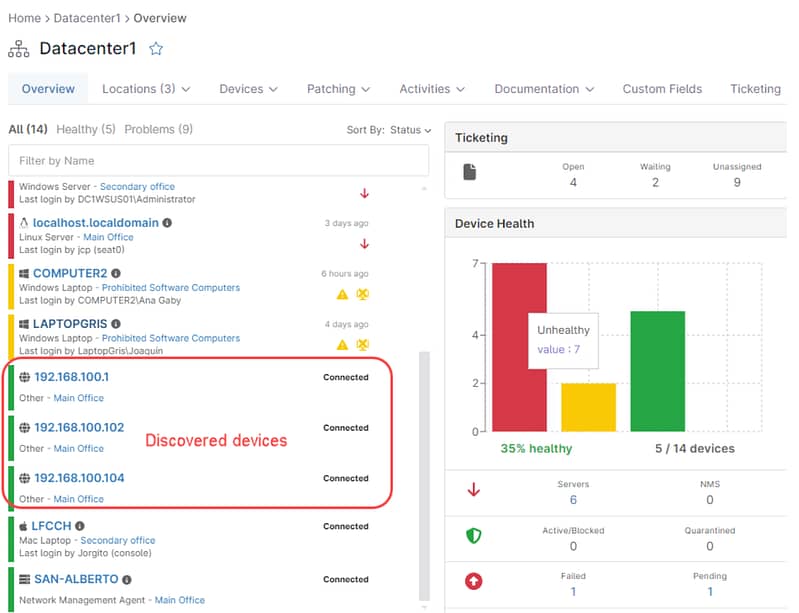
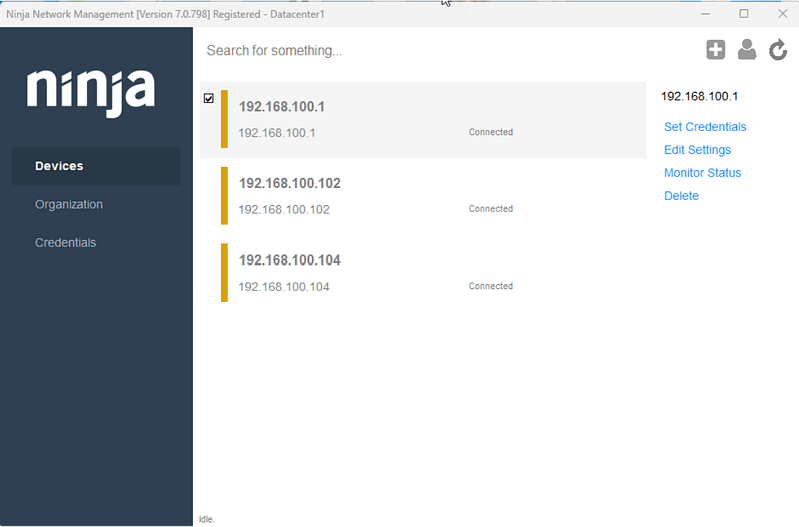
- You can use the Edit Settings on the NMS agent to add friendly names for your devices or change the device role. You can also change the monitoring preferences and add the necessary credentials.
What kind of devices can be discovered and monitored with the NinjaOne NMS agent?
The NMS agent can discover and monitor mobile devices, computers, printers, JBODs, managed switches, routers, any device with network access that responds to ICMP (ping).
More monitoring options can be obtained if the device has SNMP capabilities, for instance, an SNMP enabled JBOD device can be monitored for temperature, drives, fans, and other parameters available through SNMP.
Telnet and SSH are other protocols available in the NinjaOne NMS agent, they are used to monitor the availability of connection-based TCP/IP applications.
Next Steps
Network Inventory Scanning FAQs
What is Inventory Scanning?
What are the types of Inventory Scanning?
The methods used for network inventory scanning can operate in two primary ways:
- Scanning agents: These are deployed on each device within the network. They collect data and report back to a central database.
- Agentless scanners: These scan devices without needing to install agents on them, often using network protocols to gather information.
What are all the prerequisites for an Inventory Scan?
The prerequisite for an automated inventory scan is a server where the scanning tool will run, capable of managing all the traffic, especially if the number of nodes is large. Another prerequisite is the firewall, that needs to provide access to the scanning ports. Typical ports are UDP 61 (SNMP trap), UDP 514 (Syslog collector), UDP 2055 (Netflow collector), UDP 6343 (sFlow collector), but each scanning tool has its own port requirements.
How to perform an Inventory Scan?
The inventory scan consists of three steps:
- Device Discovery. This part is performed by a scanning tool and consists of finding a responding device withing the network.
- Analize results. This process consists in properly labeling and cataloging the discovered device, based on the way it responds to the scans. It is in this part of the process that rogue devices are sometimes found.
- Document and Report: Keep records of the scan results for future reference and compliance purposes.
Ready to become an IT Ninja?