Identify and mitigate configuration and patching vulnerabilities at scale with NinjaOne
Monitor Endpoints
Real-time Alerting
Automatic Prioritization
Vulnerability Mitigation
Customers love NinjaOne
improved patch compliance
reduced time spent on patch management
saved time on manual tasks through automation
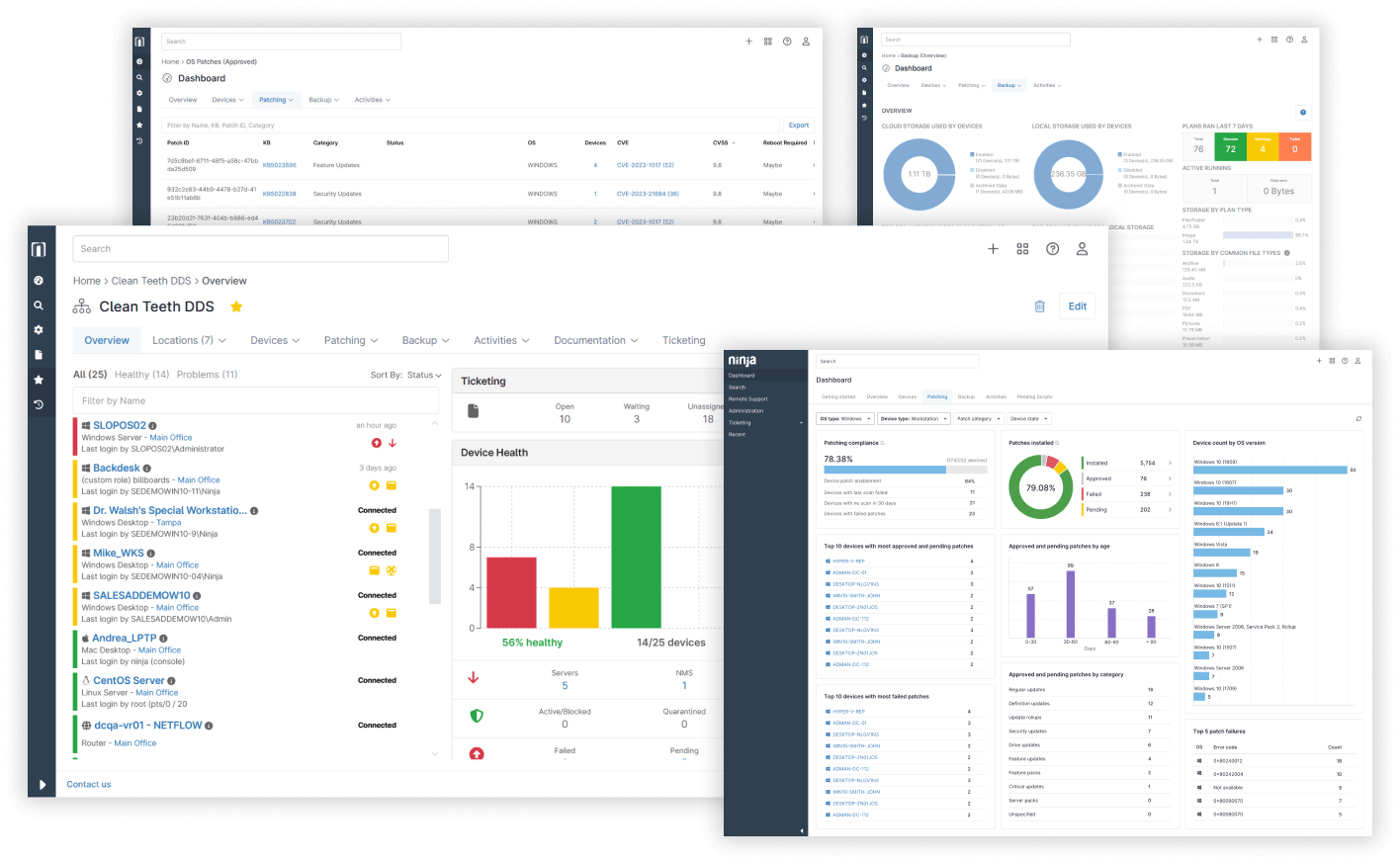
Alert and assess, prioritize, and mitigate vulnerabilities automatically
Single, intuitive console provides a comprehensive view of your IT estate
Gain deep visibility into your entire IT estate from a single, intuitive console that’s easy to deploy, learn and master.
Reduce patching time by as much as 90%
Patch third-party applications
Easily patch many popular third-party applications required to support various user workflows.
Automated vulnerability identification, assessment, and alerting
Leverage custom policies and third-party notifications to alert when vulnerabilities are detected.
Automatic prioritization of mitigation actions
Minimize the potential impact of multiple vulnerabilities by addressing based on CVSS-based criticality and impact.
Harden endpoints at scale
Configure devices at scale using policy-based endpoint management or deploy ad-hoc configuration changes to mitigate vulnerabilities.
Initiate vulnerability scans on-demand, or schedule on a recurring basis
Proactively scan endpoints and applications to unpatched vulnerabilities.
Deploy and manage antivirus solutions on all endpoints
Identify endpoints with misconfigured, outdated, or missing security software and take necessary remediation action from within the NinjaOne console.
Leverage cloud-first backup options to defend against ransomware
Protect critical business data from ransomware, accidental deletion, and disaster with cloud-first backup – directly from your NinjaOne console.
Improve your security posture from day one
Get 360-degree visibility into all your IT assets from a single console
NinjaOne provides complete, live visibility across your entire IT estate. View, control, harden, manage apps, patch, backup, and secure all your endpoints from a single solution.
Simplified, consistent patching
Multi-platform support
Ninja gives you a single-pane-of-glass to monitor, manage, patch, and support all your Windows, Mac, and Linux endpoints – no more siloed tools or context switching required. NinjaOne replaces 2.5 tools in new customer environments on average.
Quick deployment, Low TCO
As a 100% cloud-based solution, NinjaOne is quick to setup, requires minimal ongoing maintenance, and avoids costly on-premises infrastructure resulting in fast time-to-value and low total cost of ownership.
How IT departments improve security posture with NinjaOne
Improve vulnerability mitigation with NinjaOne’s powerful, intuitive unified IT management platform
Endpoint Management
One solution to monitor and manage your entire IT portfolio
Patch Management
Identify and remediate vulnerabilities at speed and scale
Endpoint Backup
Backup for distributed endpoints